This article is more than 1 year old
The weakest link in Software as a Service
Is that an elephant I see in the room?
The delivery of cloud based application functionality via the Software as a Service (SaaS) model frequently sparks security-related concerns. In our latest workshop on hosted apps, Reg readers have been very forthcoming about their nervousness in this area.
In parallel with the workshop, however, we have been gathering data through a more structured reader survey. The aim of this was partly to understand perceptions and experiences with regard to SaaS, but also to put the specific discussion of SaaS related risk into a more general context. As with all emotive topics, and cloud computing is one of these, it is all too easy to lose perspective.
The reality is that we can discuss for as long as we like how inherently secure or otherwise various SaaS based offerings are, but at some point we need to pay attention to the huge elephant in the room. We are, of course, talking about the behaviour of end users, and this chart from the survey sums up the situation pretty well:
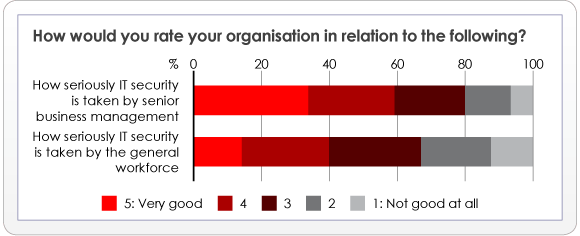
If you took part in the survey and your responses fell more into the red or amber areas on this picture then you obviously have some significant user-related exposure. Furthermore, that exposure is likely to overshadow any risks arising from the use of SaaS, assuming you are working with competent providers.
If your responses fell more into the green areas on the top two bars of the chart, then congratulations for having engendered a responsible attitude to IT security within the workforce. But before getting too complacent, we need to remember that the holes through which information can potentially leak are many, and even the most security aware user can make mistakes.
The training gap we also see on the above chart that exists in many organisations is significant here, as are the responses to another question from the survey illustrating that IT can’t possibly plug all of the holes:
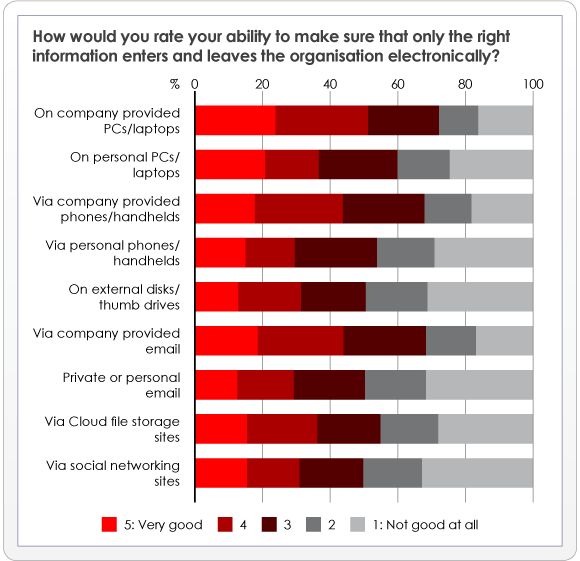
When we consider the impact of SaaS on security in this context, apart from putting perceived provider or service related risks into their proper perspective, we can also see opportunities for cloud options to potentially reduce end-user related exposure.
If you are using a hosted office suite, for example, documents, spreadsheets and presentations tend to be saved to a cloud storage area. This makes them broadly accessible (subject to security and access rights) without the need to copy them to local devices.
You could argue that internal network-based storage (file servers, NAS drives, SharePoint, etc) achieve the same, but this isn’t typically the case. Using desktop software to directly open and save documents stored on the network can be slow on many corporate networks, and intolerable when working over broadband from a home-office, encouraging local copies to be made to overcome this. When the software itself is running in the cloud, in the same environment as the data, opening and saving even the largest file is extremely quick as documents are not being pulled and pushed across the network.
Of course stopping users making local copies of data for offline use and transfer between systems can’t be completely eradicated, but anything that reduces the need and/or temptation is going to help. Having said this, it is becoming increasingly common for SaaS solutions to support offline use through stand-alone client software working from a local cache of the cloud based data. The advantage here is that security and access policies are often enforced in the cache through properly controlled synchronisation, so even in mobile scenarios, cloud services can provide enhanced security. Taking a step back, we need to consider another dimension to end-user created risk that has to do with cloud service adoption. Our survey results tell us that more organisations are starting to see an active demand for SaaS from business management and end users, and we know from anecdotal feedback that we can only expect this to grow:
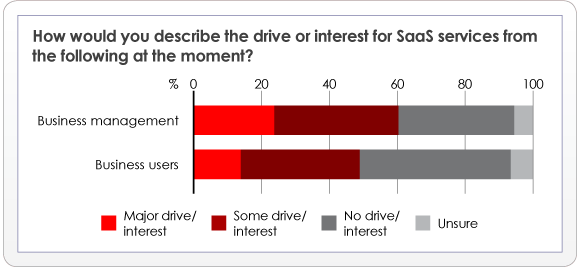
Where IT is in the loop on SaaS adoption, the opportunity naturally arises for proper attention to be paid to security and access issues. If departments, workgroups or individual users are adopting SaaS independently of IT, however, then with the loose attitude to security we have seen, and/or ignorance due to inadequate training, unnecessary exposure can arise. Even if the provider makes security and access features available, beyond standard measures such as default https sessions, there is no guarantee end users will take advantage of them. Indeed users are notorious for switching off anything they consider to be inconvenient, and enhanced security options often fall into this category.
The overriding lesson from all this is to maintain proper perspective when it comes to security and the cloud. The chances are that the service provider’s physical security measures and facilities to manage access policy are at least as good as yours, and in many cases will actually be a lot better. So, rather than agonise over that aspect of SaaS, it might be better to focus on the user end of the equation, as that’s where most of the real risks are likely to be.
In practical terms, a priority action that falls out of this is paying more attention to user education and awareness. Instigating clear policies and governance in relation to SaaS adoption, with appropriate ‘stick and carrot’ motivation, is also important, particularly for defining ground rules for when users are acting independently of IT.
The chances are that hosted services in their various forms are likely to touch most organisations going forward if they haven’t done already. Strengthening the ‘weakest link’ sooner rather than later is therefore a good idea. Not only will this lay the groundwork for effective SaaS adoption, it will also help to boost security in general across the organisation, with all of the risk management and compliance benefits that come with that. ®
