This article is more than 1 year old
DUDE, WHERE'S MY CAR? New leccy BMWs have flimsy password security – researcher
Motor giant told to try harder with mobe app
Exclusive New BMW cars have security shortcomings that could allow thieves to pop open a victim's flash motor from a smartphone.
Ken Munro, a partner at Pen Test Partners, uncovered security issues in the systems that pair the latest generation of beamers with owners' mobiles. By stringing together the flaws, a crook could open doors, windows and the boot, and leave the lights on for an added headache.
Preliminary findings from the ongoing research – which El Reg passed onto BMW last month – suggest it may be possible to determine the usernames of drivers through social networks, and then use a mix of social engineering and other techniques to gain access to vehicles – or trick BMW into suspending security protections, clearing the way for other attacks.
The car manufacturer said it had passed Munro's research onto its people in Germany, and played down any risk. "If it was an issue then it's solved now," a spokesman told The Register. It's understood the company has added an extra layer of protection: a new check for a PIN when accessing the mobile application.
Professor David Stupples, head of City University London's Centre for Cyber Security Sciences in London, has a keen interest in the security of embedded computing, and praised Munro's research.
Munro said he discovered the weaknesses after a friend took delivery of an electric BMW i3.
"I had already started looking at the builtin email reader application when the security discussion around the Tesla emerged," Munro told us. "My mate knows that I’m into security, so he walked me through the process of account creation, signup and authentication that he went through when registering the car."
The i3 and i8 have an iOS app called iRemote, which is closely related to the Android and iOS Connected Drive application familiar to most BMW and Mini drivers.

BMW iRemote app ... charged and in the dock
"iRemote allows owners to monitor battery life, potential range on a map, plus the ability to lock/unlock the car and turn on pre-heating/cooling, like the standard Connected Drive app," Munro explained.
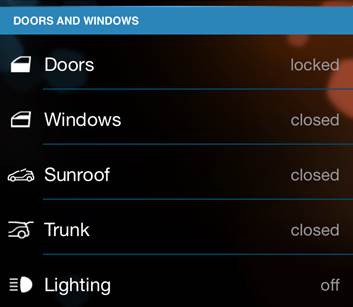
BMW iRemote controls ... power in crooks' hands
The researcher investigated whether it was possible to manipulate iRemote, perhaps using it in conjunction with Connected Drive, to locate a car and unlock it – close to a worst-case scenario. The security expert's initial findings point to a variety of shortcomings in BMW's approach, none of which are as severe as the mistakes made by Tesla this year.
"The BMW approach seems to be a fair bit more secure than the Tesla approach," Munro said. "Some care has been put in to the iOS app: standard man-in-the-middle attacks would be unsuccessful. That’s not to say they wouldn’t be possible, just that they would be rather harder.
"The process of signing up a car to iRemote could only be carried out by phone. Some significant validation of the user was carried out, more so than for Connected Drive."
Munro gave BMW credit for considering security, although there are some flaws in its design. "They’ve clearly given the process quite a bit of thought, certainly more than Tesla, though perhaps not quite enough," he said.
Predictable username peril
One notable weakness, according to Munro, is BMW's failure to steer customers away from a predictable username. When registering the vehicle with the BMW call centre for iRemote, the user gets a username along the lines of firstname.lastname. This makes life easier for miscreants to cause mischief. All you need to do is spot an owner online and lift their name.
"Surely customers should be advised against choosing a predictable username?" said Munro. "It doesn’t take much to find i3 users on the interwebs – they’re all shouting about their cool new car. I’m with them – it’s an awesome bit of kit. So, I have a fair chance of guessing the app username."
That by itself isn't the end of the world, but as we'll see, it's useful to know if you want to annoy, or rob, an i3 or i8 owner. Once you've proved a username is valid or not, of course.
"Validation of a username is often possible through a 'forgotten password' form online. BMW don’t have a form – big tick for them," Munro said. "You have to phone a call centre, so it’s out-of-band, requiring some social engineering."
And there's another plus on the side of the German car-maker. "The login to Connected Drive doesn’t offer enumeration – error messages from failed logins are non-specific. Another big tick," Munro said.
Locked out of the app
So nothing to see here, please move along? Well, not quite, as Munro discovered – the software leaks whether or not a username is valid after a number of failed attempts:
My friend had accidentally locked himself out of Connected Drive whilst trying to configure the mail reader. I asked him what happened: after five attempts – fat fingers! – the account locked, displaying an error message. You only get a lockout if the user account name is valid. So now we have a denial of service; one can validate usernames gleaned online from other sources, then lock users out of Connected Drive AND iRemote by submitting bad passwords. Big deal, though I imagine most Connected Drive users would get the hump if they lost their functionality.
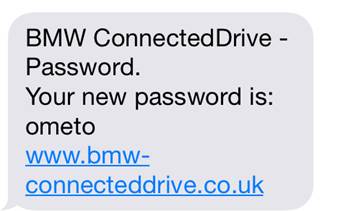
Craptastic password reset by SMS
Another problem uncovered by Pen Test Partners involves an "inconsistency between authentication and reset processes on Connected Drive and iRemote". In other words, a reset password is given a rather trivial string of five random lowercase characters, and the app doesn't recommend the user change it.
Bear in mind security researcher Nitesh Dhanjani just discovered a security hole in the systems protecting Tesla S owners online: the electric car maker used six-character passwords when registering owners, and failed to limit the number of login attempts. This allowed thieves to potentially brute-force their way into Tesla S user accounts.
Back to the i3, Munro explained to The Register:
When my friend accidentally locked himself out, the reset was out-of-band, sending a one-time password by SMS to the registered phone on the account. Another big tick for BMW. HOWEVER, that password was 5 alpha chars, all lower case. Not a problem if it’s changed on first use, though. The Connected Drive web application correctly required a change on first use. The iRemote application didn’t – the five-char password worked, and continued to work until I suggested to my friend that it might be a good idea to change it. BUT, the iRemote app locked out if the password was incorrectly entered 10 times.
More corner-cutting than car-jacking, of course, but the list goes on. During its research, Pen Test Partners noticed that the iRemote application is case-insensitive when checking passwords, another minor demerit for the German car-maker as it limits password strength.
But is it possible to open up stranger's beamer from afar? Perhaps so. You'd need is the iOS app, the username, and the obtained or guessed password – there's no way to limit the car to one mobe.
And if the victim reuses the same password, or close variations, then compromising some other website account could unlock, literally, the mark's motor. (One needs the physical key fob to start the engine, although letting off the handbrake can make a car disappear.)
"The first time provisioning process for Connected Drive and iRemote is fairly robust. It would be hard to do much without some social engineering," Munro said.
"However, once you’re up on iOS with iRemote, it’s trivial to provision ANOTHER iPhone with the app. AppStore, the same username and the same password. To prove the point, my friend showed me the process of installing and configuring the app on his wife’s phone, so she could talk to the car too.
"Once we have the password to the Connected Drive account, it’s all over. You just provision a second phone and iRemote and Connected Drive, and you have all the access you need to find and unlock the car."
Munro continued:
You could profile the user online; find their mail account through social media research; enumerate or validate their iRemote credentials using the web based login; then check the various password breach databases (e.g. the Adobe dump) and see if they’ve reused a password. Install the iRemote app, enter username and password, find the car using the app, and unlock it … This has to be the simplest vector to compromise a vehicle.
The vulnerable security mechanism works in a similar way to older BMW vehicles, but the vector to find the username and password is completely different: it exploits issues with the provisioning process for iRemote and the i-Series cars.
