This article is more than 1 year old
Thunderstrike shocks OS X with firmware bootkit
Permanent backdoor affects all Macs packing Thunderbolt ports
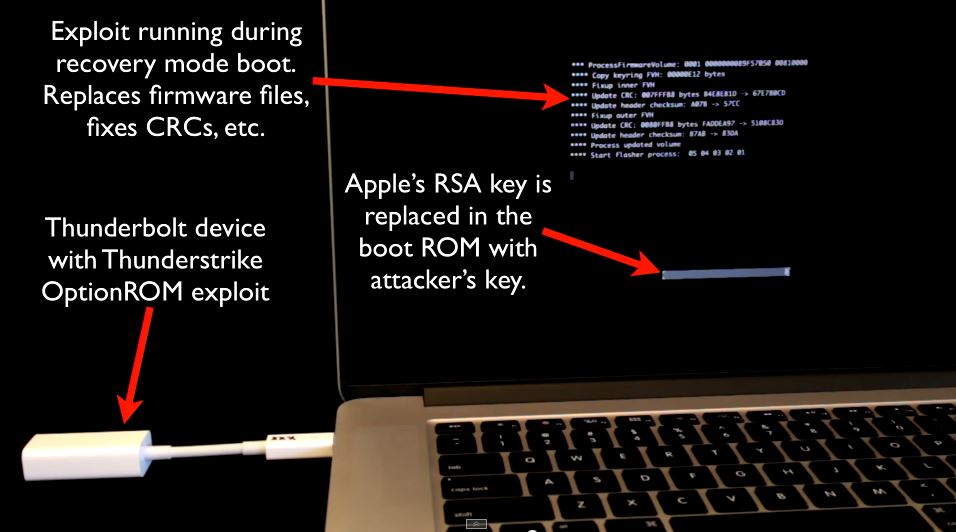
Reverse engineer Trammell Hudson has created an attack dubbed Thunderstrike which can quietly, persistently and virally compromise Apple Macs from boot.
The Thunderstruck attack uses 35 year-old legacy option ROMs to replace the RSA keys in a Mac's extensible firmware interface (EFI) to allow malicious firmware to be installed and lock out attempts to remove it.
It works against all Macbooks released since Thunderbolt's 2011 introduction, Hudson said, noting that he successfully tested seven machines.
"When we boot the machine the Thunderstrike exploit runs in the recovery mode boot replacing firmware and Apple's update routine flashes its RSA key onto the motherboard - and once that is done, we own the system and we can flash whatever we want using Apple's own update tools," Hudson told an applauding audience at the Chaos Communications Congress.
"Because we replaced the key this bootkit can't be removed through software alone because we control the key the firmware is going to use.
"There is no official channel to remove it."
Possible attack vectors for the exploit were NSA-style interception of Mac shipments, unobserved brief physical access to targeted computers, aka 'Evil Maid' attacks, or "virulent" spreading through shared devices.
It could likely even use the so-called Dark Jedi attack introduced at the conference to facilitate remote attacks, a feat Hudson said he would work to develop.
The work was based on research by Assurance.com.au pen tester Loukas K who in 2012 (vid) built a gigabit Ethernet Thunderbolt adaptor that could backdoor the OS X kernel.
"You might ask why isn't there a cryptographic check at boot time? ... The flash ROMs are only checked when they are being updated and once written it is never checked again [possibly] due to saving speed," he said.
Apple is patching some of the two-year-old Thunderstrike vulnerabilities to Mac Minis and iMac Retinas, but not altogether closing off the option ROM attack vector, while older Macs could have firmware downgraded and then attacked.
Hudson disabled Thunderbolt option ROMs across his Macs, a feat he noted could only be done prior to attack by Thunderstrike. A more permanent method would be to disable thunderbolt PCIe functions altogether to close off other attack vectors.
Hudson has written a technical blog on the exploit. ®