This article is more than 1 year old
Move over, Stuxnet: Industroyer malware linked to Kiev blackouts
Modular nasty can seize direct control of substation switches and circuit breakers
Security researchers have discovered malware capable of disrupting industrial control processes.
Industroyer can cause the same sort of damage as BlackEnergy, a malware strain blamed for attacks on energy firms that caused blackouts in Ukraine in December 2015. The malware may have featured in follow-up attacks last December and can significantly harm electric power systems. It could be refitted to target other types of critical infrastructure, according to security firm ESET.
Industroyer is a particularly dangerous threat, since it is capable of controlling electricity substation switches and circuit breakers directly. To do so, it uses industrial communication protocols used worldwide in power supply infrastructure, transportation control systems, and other critical infrastructure systems (water, gas).These switches and circuit breakers are digital equivalents of analogue switches; technically they can be engineered to perform various functions. Thus, the potential impact may range from simply turning off power distribution, cascading failures, to more serious damage to equipment, and may vary from one substation to another.
Industroyer is modular. Its core component is a backdoor used to manage the attack: it installs and controls the other components and connects to a remote server to receive commands and report back to the attackers.
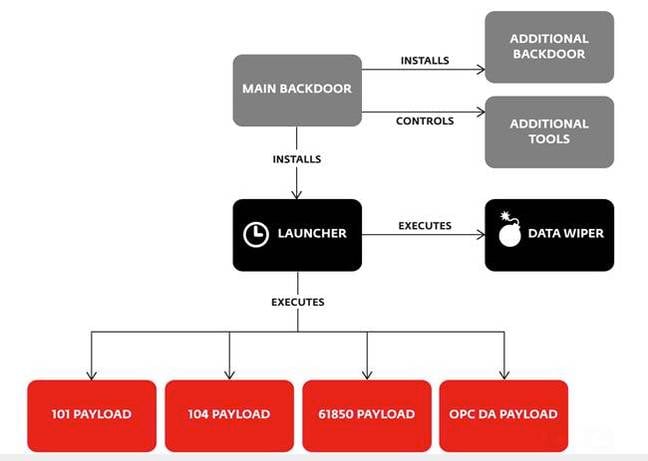
Industroyer industrial control malware
The unknown authors of the malware are familiar with industrial control systems. Industroyer uses inherent security weaknesses, rather than vulnerabilities as such, to spread.
The malware bundles features designed to remain under the radar, ensure persistence, and wipe traces of itself after completing the job. Another module is a denial-of-service tool that exploits the CVE-2015-5374 vulnerability in Siemens SIPROTECT devices and render targeted devices unresponsive. It also contains a wiper component. ESET's researchers describe the malware as the most sophisticated to hit industrial control systems since Stuxnet, the Iranian nuclear centrifuge crashing cyber-weapon.
Industroyer is highly customisable malware. While being universal, in that it can be used to attack any industrial control system using some of the targeted communication protocols, some of the components in analyzed samples were designed to target particular hardware. For example, the wiper component and one of the payload components are tailored for use against systems incorporating certain industrial power control products by ABB, and the DoS component works specifically against Siemens SIPROTECT devices used in electrical substations and other related fields of application.While in principle it's difficult to attribute attacks to malware without performing an on-site incident response, it's highly probable that Industroyer was used in the December 2016 attack on the Ukrainian power grid. On top of the fact that the malware clearly possesses the unique capabilities to perform the attack, it contains an activation timestamp for December 17, 2016, the day of the power outage.
The 2016 attack on Ukraine's power grid deprived part of its capital, Kiev, of power for an hour. ®
