This article is more than 1 year old
Gone phishing with eBay
Why is there a naked woman in that Bentley?
There I was, on Monday night, scanning eBay for car bits. This is not a problem. I have this under complete control. I can give up buying worn out parts and rusty bits of bodywork at any time. Really.
Anyway, I spotted a real bargain, a 2007 Bentley Continental for 0.01 GBP. Since these usually retail for something in the region of £135,000 I felt that this represented a considerable saving.
Unusually for the vendor of such a prestigious vehicle, the listor had decided to post an image of a young lady in place of the car itself. I reasoned that perhaps this was his daughter and the picture was meant to show that his family also loved the car.
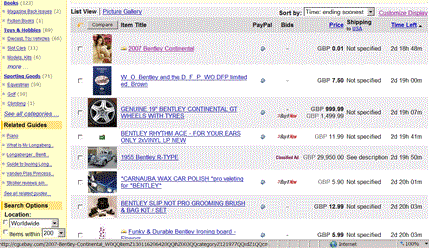
True, my theory didn’t entirely explain why she was naked to the waist but I clicked on the link anyway, hoping to acquire a bargain.
Several screens flashed before my eyes (unnervingly like my life going past) and then good old IE7 told me that I was about to be phished. It was quite correct, I was very phished (or, as we say in the UK, phished off). How come I could be browsing eBay one moment and phished the next?
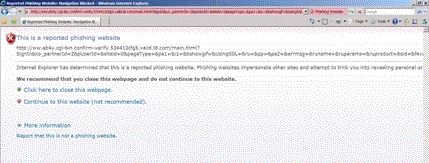
The URL is:
http://ww.eb4y.cgl-bin.confirm-verify.534413cfg5.valid.i8.com/main.html?
SignIn&co_partnerId=2&pUserId=&siteid=0&pageType=&pa1=&i1=&bshowgif=&Using
SSL=&ru=&pp=&pa2=&errmsg=&runame=&ruparams=&ruproduct=&sid=&favoritenav=&c
onfirm=&ebxPageType=&existingEmail=&isCheckout=&migrateVisitor=&SignIn&co
_partnerId=2&pUserId=&siteid=0&pageType=&pa1=&i1=&bshowgif=&UsingSSL=&ru=&
pp=&pa2=&errmsg=&runame=&ruparams=&ruproduct=&sid=&favoritenav=&confirm=&e
bxPageType=&existingEmail=&isCheckout=&migrateVisitor=
My journalistic instincts were, inevitably, hooked and I decided to investigate but first, I reported the incident to eBay to try to ensure that other poor fish were not landed in the same way. The time was 21:54.
The first step was to try to isolate the problem – was it my machine or eBay? I emailed one of my long suffering Reg. Developer editors (David Norfolk) who, despite the time, obligingly tried the same listing and got the same result. So, it could be malicious code on the PC but both David and I would have to be infected in the same way; possible, but unlikely.
By repeatedly pressing PrtScr I managed to obtain a screen shot of the listing itself as it flashed past.
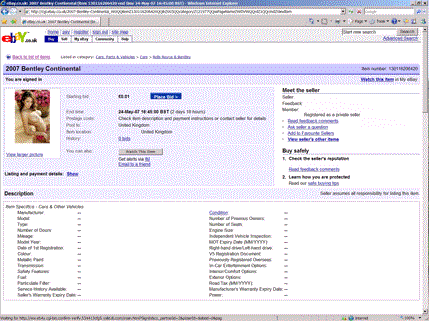
For those without a microscope, the bottom of the screen reads as:
![]()
We’ve blanked the identity of the ‘seller’ because it is highly likely that he/she is innocent and the account was hijacked (see the response from eBay below).
Question - How do you hijack an eBay account in order to go phishing?
Answer - By phishing.
(Dictionary definition of recursion - see recursion.)
A little more investigation showed that the listings weren’t just aimed at potential Bentley owners.
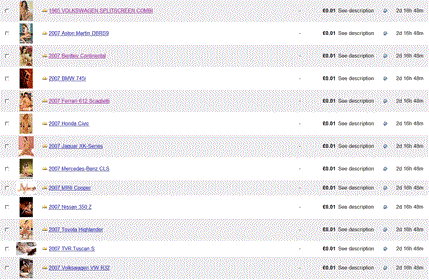
At about 00:15 Tuesday morning the listings finally disappeared.
Naturally, we were keen to find out what had happened: we had some evidence, including the source code of the original page, so we contacted eBay. The company’s response was interesting. We first contacted it on Tuesday and, despite repeated requests, found it very difficult to get any hard information.
Eventually, on Friday afternoon, as we were going to press, we received the following:
“In this particular case, a genuine user's eBay account was taken over by fraudsters who attempted to use it to post fraudulent listings. eBay’s systems identified the fraudulent listing and eBay’s customer support team moved quickly to remove it from the site and restore the account to its rightful owner. eBay takes any threat to the security of its users extremely seriously and we also work closely with ISPs and law enforcement to bring down the spoof websites we identify."
It would appear that this statement corroborates what we observed; nevertheless it is worth examining the statement in detail.
For a start, whilst it is true to say “fraudsters who attempted ….. to post fraudulent listing”; more information is conveyed by the equally true statement “fraudsters who succeeded …. in posting fraudulent listings”.
Secondly, there is no information here about the eBay systems that identified the fraudulent listing. Is it simply the feedback from users or are there also algorithmic systems that prowl the system looking for naughtiness?
Let’s assume for a minute that eBay does have effective internal systems for detecting fraudulent listings. In that case it would be far, far better for the users of eBay if these ran proactively, before the listing was posted. If on the other hand eBay doesn’t have such systems and relies on user feedback to identify fraudulent listings, the implication is that we can expect fraudulent listings to be up for an unknown period of time before removal. As a user of eBay are you happy about this? I’m not.
Thirdly, it took eBay at least two hours to respond to this after it was reported. Do you consider this to be moving “quickly”?
As we were trying to find out exactly what had happened, an apparently related incident was also brewing.
The bottom line is that the evidence we have seen suggests that it may be possible for users to post listings on eBay that redirect off the site.
It ought to go without saying, but we’ll do it anyway. Be careful out there.
