I imagine that is the question most users will ask when they see this dialog box:
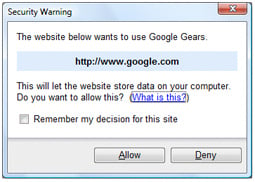
There are a couple of things I don't like about this dialog. First, the website is defined only by a URL. The problem is, it's a plain http connection so there's no SSL certificate involved, so I can't easily check the identity of the site. This one is Google, so it's not too difficult; but what if it is some other site? It is not particularly easy to verify the ownership of a URL; whois information is not reliable.
Second, what are the implications of my decision? If you click "What is this", you get this page, which explains offline functionality but doesn't mention security. It does mention that Gears is a beta - personally I think this should be up-front in the security warning dialog as well. Do you trust this beta software?
If you go to the Frequently Asked Questions, there is still no mention of security. Is nobody asking about it? This article is the closest I can see, but merely repeats the information in the original dialog, that Gears allows websites to write to my computer. Enquiring minds ask: where can they write data? Where can they read data? Could they install malware or execute code?
We could do with a link to this page, about the Gears security model. This tells me that Gears uses a same origin policy:
A web page with a particular scheme, host, and port can only access resources with the same scheme, host, and port.
It also says:
Google Gears data files are protected with the user's operating system login credentials. Users with separate login names cannot access each other's Google Gears data files, as enforced by the operating system.
The bit about "as enforced by the operating system" should be highlighted. If your users have local admin rights, as on some Windows boxes, they will be able to access files belonging to other users.
But is Gears safe? What if I'm taken in by a scam site and give it permission to use Gears?
It may not be too bad. Gears can't write anywhere on my hard drive, only to a location in my local profile or home directory. It doesn't use the browser cache, presumably because it isn't reliable; it may get cleared. Still, I guess some sort of attack might be possible along the lines of: write an executable to my local resource store, then give me a link to click and run it. Gears could fill your home directory with stuff you do not want, of course, but that's the explicit permission you give when you agree to let a site write to your computer.
This presumes that Gears does not have security bugs. There may be and probably are ways to mount attacks using Gears that I have not thought of.
Bottom line: Gears is probably fairly safe, provided that the site really is trustworthy, but it is a beta and the usual caveats apply. Check that URL carefully. Avoid Gears when used by smaller organizations that might not have sites well defended against malware. I still don't like the dialog though; and I'm surprised that Google does not make it easier for users to examine the security issues.
This post is prompted the announcement of Offline access to Google Docs.
This article originally appeared in ITWriting.
Copyright (c) 2007, ITWriting.com.
A freelance journalist since 1992, Tim Anderson specializes in programming and internet development topics. He has columns in Personal Computer World and IT Week, and also contributes regularly to The Register. He writes from time to time for other periodicals including Developer Network Journal Online, and Hardcopy.
