This article is more than 1 year old
eBay scammers work unpatched weaknesses in Firefox, IE
Other sites also vulnerable to CSS attack
Updated eBay scammers have been exploiting unpatched weaknesses in the Firefox and Internet Explorer browsers to deliver counterfeit pages that try to dupe people surfing the online auction house to bid on fraudulent listings.
The attacks managed to inject eBay pages with hostile code by exploiting issues long known to afflict Firefox and IE. While eBay has managed to block the exploit from working on its domains, other websites that accept user-generated content may still be vulnerable to the attacks, web security experts warn.
Firefox security volunteers say they are in the process of patching the vulnerability. For their part, Microsoft officials say the exploits aren't the result of a vulnerability in IE but rather of websites that fail to properly protect against such attacks.
The evil genius behind the eBay scheme managed to pull off what amounts to an XSS, or cross-site scripting, attack that injected forbidden javascript elements stored on third-party websites. That allowed the eBay pages to contain outside email links and other unauthorized code while still evading toolbars designed to detect fraudulent listings.
In addition to injecting a link that automatically prompts users to email the seller at an aol.com address, the scam used a random number generator to change the item number each time the page was loaded. Item numbers are supposed to be unique and are used to report fraudulent listings. Changing the number made it harder for eBay's fraud busters to remove bogus auctions.
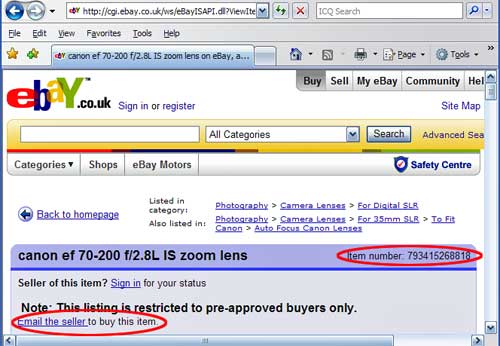
Picture perfect: an eBay listing with fraudulent elements injected into it
The attacks targeted Firefox by exploiting the way the browser implements what's known as XBL, or XML binding language. By invoking a rogue CSS, or cascade style sheet, hosted on a third-party site, the Mozilla browser was tricked into running forbidden code that injected fraudulent content into the listings. Over the past week, there has been considerable debate among Mozilla security volunteers about whether the condition amounted to a security vulnerability or an intended feature. They decided to make changes to the browser after witnessing the eBay scams that abused it.
"Patches are being constructed to get rid of an existing useful feature due to the patent inability of some websites to take elementary protective measures even after 5 years of the feature existing and after being repeatedly told to NOT link to external sheets by all browser vendors," one debate participant wrote El Reg in an email. "Note that the patch won't really help eBay much unless they really do start filtering the CSS they allow, since so much can be accomplished with just CSS."
A similar issue also related to off-site CSSes allowed the eBay attacks to work flawlessly on IE browsers, as the above screenshot makes clear. The exploit targeted IE functionality commonly referred to as expressions that has long been a known vector of XSS exploits. While IE 8 has been locked down to prevent such attacks, versions 6 and 7 of the Microsoft browser have not, and Bill Sisk, Microsoft's security response communications manager, said there are no plans to add such protections to the older browsers.
"Our investigation has shown that it is not a vulnerability in Internet Explorer," Sisk wrote in an email over the weekend. "In fact, the claim represents a method by which malicious attackers can exploit specific functionality in websites to bypass security measures. The nature of these attacks is not new and website operators commonly have protections in place to mitigate against such attacks."
Sisk's point is well-taken that eBay and other websites have an affirmative duty to filter code that allows these attacks to succeed. But his insistence that IE is blameless isn't entirely right, either. Microsoft has rightfully decided to protect IE 8 users by changing some of the browser's behavior concerning external CSS. Users of IE 7 deserve no less.
As was the case last week even large, sensitive sites such as eBay don't always protect against such attacks. Company spokeswoman Nichola Sharpe issued a statement that read in part: "This is not a new security threat, our online security experts are already aware of this and have identified it as a known bug in Firefox. eBay utilizes sophisticated security technologies to protect our customers against attacks such as this. We continually update our security to deal with emerging threats - and have done so with this threat."
Maybe, but eBay took more than 24 hours to remove one such fraudulent listing after it was reported, said Cefn Hoile, a browser security expert who first reported the Firefox issue.
"eBay has to take some responsibility for sure," Hoile wrote in an email. "They chose to serve this content which incorporated the third party stylesheet."
The only way to effectively protect users from such attacks is to white-list filter a set number of CSS functions deemed to be safe and to block everything else. That may be patently obvious to some, but if eBay has only now gotten around to implementing such measures, it's a good bet plenty of other websites are still wide open to this attack. Which means we wouldn't be surprised to see more attacks like these coming to a Web 2.0 site near you. ®
This article was updated to remove the words "bugs" and "vulnerabilities" to reflect Microsoft's contention that the attacks aren't the result of flaws in IE.
