This article is more than 1 year old
Treemometers: A new scientific scandal
If a peer review fails in the woods...
A scientific scandal is casting a shadow over a number of recent peer-reviewed climate papers.
At least eight papers purporting to reconstruct the historical temperature record times may need to be revisited, with significant implications for contemporary climate studies, the basis of the IPCC's assessments. A number of these involve senior climatologists at the British climate research centre CRU at the University East Anglia. In every case, peer review failed to pick up the errors.
At issue is the use of tree rings as a temperature proxy, or dendrochronology. Using statistical techniques, researchers take the ring data to create a "reconstruction" of historical temperature anomalies. But trees are a highly controversial indicator of temperature, since the rings principally record Co2, and also record humidity, rainfall, nutrient intake and other local factors.
Picking a temperature signal out of all this noise is problematic, and a dendrochronology can differ significantly from instrumented data. In dendro jargon, this disparity is called "divergence". The process of creating a raw data set also involves a selective use of samples - a choice open to a scientist's biases.
Yet none of this has stopped paleoclimataologists from making bold claims using tree ring data.
In particular, since 2000, a large number of peer-reviewed climate papers have incorporated data from trees at the Yamal Peninsula in Siberia. This dataset gained favour, curiously superseding a newer and larger data set from nearby. The older Yamal trees indicated pronounced and dramatic uptick in temperatures.
How could this be? Scientists have ensured much of the measurement data used in the reconstructions remains a secret - failing to fulfill procedures to archive the raw data. Without the raw data, other scientists could not reproduce the results. The most prestigious peer reviewed journals, including Nature and Science, were reluctant to demand the data from contributors. Until now, that is.
At the insistence of editors of the Royal Society's Philosophical Transactions B the data has leaked into the open - and Yamal's mystery is no more.
From this we know that the Yamal data set uses just 12 trees from a larger set to produce its dramatic recent trend. Yet many more were cored, and a larger data set (of 34) from the vicinity shows no dramatic recent warming, and warmer temperatures in the middle ages.
In all there are 252 cores in the CRU Yamal data set, of which ten were alive 1990. All 12 cores selected show strong growth since the mid-19th century. The implication is clear: the dozen were cherry-picked.
(This oversimplifies the story somewhat: for more detail, read this fascinating narrative by blogger BishopHill here.)
Controversy has been raging since 1995, when an explosive paper by Keith Briffa at the Climate Research Unit at the University of East Anglia asserted that that the medieval warm period was actually really cold, and recent warming is unusually warm. Both archaeology and the historical accounts, Briffa was declaring, were bunk. Briffa relied on just three cores from Siberia to demonstrate this.
Three years later Nature published a paper by Mann, Bradley and Hughes based on temperature reconstructions which showed something similar: warmer now, cooler then. With Briffa and Mann as chapter editors of the UN's Intergovernmental Panel on Climate Change (IPCC), this distinctive pattern became emblematic - the "Logo of Global Warming".
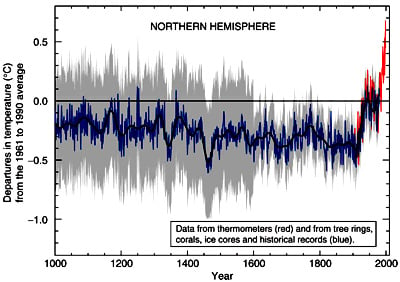
IPCC's Assessment Report from 2001 - with the error bars in grey emphasised
