This article is more than 1 year old
Hacker sinks Royal Navy website
SQL injection exploited by serial military site 'show-off' hacker
The Royal Navy's main website has been taken offline following claims by a Romanian hacker that he broke into the site, swiping the login credentials of administrators in the process.
The hacker, TinKode, posted information on the web to support his claim to have penetrated the site, www.royalnavy.mod.uk.
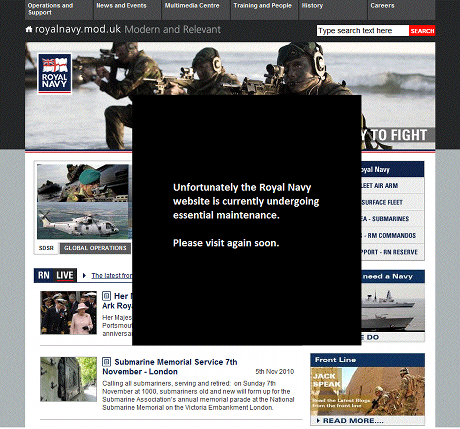
The Royal Navy replaced its website with this static image.
TinKode has previous form for breaking into the website of military organisations. He had previously published data on SQL injection vulnerabilities in sites run by the US Army and (separately) information about security holes on Nasa's website, net security firm Sophos notes.
Sophos reckons the attack was motivated out of mischief rather than anything more nefarious or malign, such as an attempt to plant malicious code targeting surfers visiting the site, many of who could be expected to work in the defence industry.
"This hack was more about showing off and embarrassing people," a Sophos spokesman explained. Sophos reckon TinKode broke in using a SQL injection vulnerability on the jackspeak* blog.
The site is primarily designed to publicise the Navy's work and to act as a point of contact for recruitment. It's very unlikely that any confidential much yet secret material was kept on a public facing website.
Nonetheless the attack is hugely embarrassing, not least because it happened less than a month after defending against cyber-attacks was ranked alongside combating international terrorism as the two highest priorities for UK national security at the end of the National Security Strategy review. ®
* Jackspeak is a term for navy slang - eg "It's warmer in here than a jan dockie's starboard oggy pocket" (translation: It's quite warm). Thanks to former Navy officer turned Reg defence correspondent Lewis Page for this insight into navy life.
