This article is more than 1 year old
Pass the remote control: vPro eases systems management
Power at your fingertips
Desktop management is big money. It’s a critical topic for any size business seeking to optimise its IT. The right combination of software and hardware results in very impressive desktop management capabilities.
The heavy hitter on the hardware side is without question Intel. The vendor’s vPro provides unprecedented hardware-based systems management while adding negligible additional cost per system.
Now in its seventh iteration, the platform has evolved quite a bit over the years. The critical component, and the one most people care about, is called Active Management Technology (AMT), which allows remote management of systems. Version changes to AMT are reflected in the version numbers of vPro.
vPro is a branding exercise packaging certain technologies together with AMT. A vPro desktop will have hardware-assisted virtualisation, Intel’s Trusted Execution Technology and support for the No Execute bit.
Safety precautions
Network security is also part of the package. vPro notebooks must support IEEE 802.1x, Microsoft’s Network Access Protection(NAP) and Cisco’s Self Defending Network platforms.
Desktops provide support for 802.1x and SDN, but are not required to support NAP.
The key to the product’s success is the ability to remotely control a vPro system’s keyboard, video and mouse over the network (IP-KVM). Traditionally, taking advantage of this feature required the use of dedicated desktop management software such as Symantec’s Altiris or Microsoft’s System Center suite.
vPro desktops with AMT version 6 or newer, however, do not have this requirement. Modern AMT offerings include a built-in VNC server that should be compatible with your favorite VNC client. RealVNC’s VNC Viewer Plus has taken this even further, integrating control over additional vPro elements into the client software.
This is a very different management capability than can be handled through software remote-access systems such as RDP. vPro provides remote KVM capabilities through the entire boot cycle of the system, which allows you to access the BIOS of the computer, make changes to add-in card firmware and more.
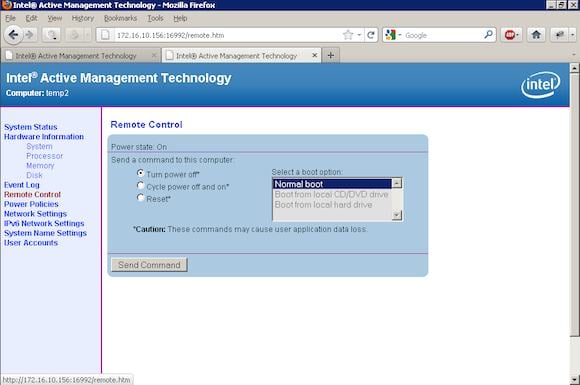
vPro supports remotely power management, the ability to turn a computer on or off or reboot it independently of KVM keyboard or user input. This is useful for example when a frozen operating system is not accepting keyboard inputs.
Distance no object
A feature with far-reaching support implications is the ability to mount ISO files remotely. This means you can remotely load an operating system or use diagnostic tools without user intervention. Loading Windows 7 up on a computer by mounting an iso across a VPN from halfway around the world isn’t fast, but it works and it works well.
Worth a mention too is the Third Party Data Store. This is a small amount (192kb) of flash memory that is part of AMT and can be read or written to even when the PC is off. It is generally used by third-party software vendors to store information such as version numbers to ensure that software assets can be tracked. There are however many other uses.
vPro is capable of serving up a complete hardware inventory, and supports network discoverability. Using established third-party desktop management software, PowerShell or custom scripts and the vPro API, a complete inventory of all vPro systems on your network can be quickly created.
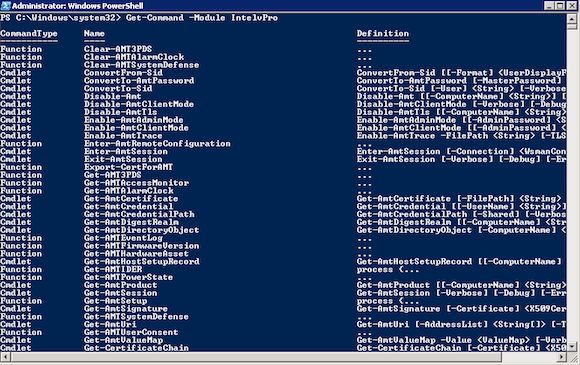
This can be done out-of-band, on a schedule as per various alerts and even if your systems are powered down.
vPro enables you to remotely control every aspect of your desktop, eliminating the need for deskside assistance for anything other than outright hardware failure. This is incredibly powerful, so Intel has made sure that as many security features as possible are built into the system to prevent its misuse.
Restricted entry
Robust network features are naturally included. If you suspect that you are dealing with an infected system, you can block or throttle all network traffic to and from the wired or wireless interfaces. Add-in network cards, even those made by Intel, cannot be controlled in this fashion.
There is a hardware firewall which allows you to create various packet filters to restrict dangerous traffic, or to "whitelist" certain addresses with which you want to allow communication. Expect this feature to gain a lot more importance when IPv6 starts to take off.
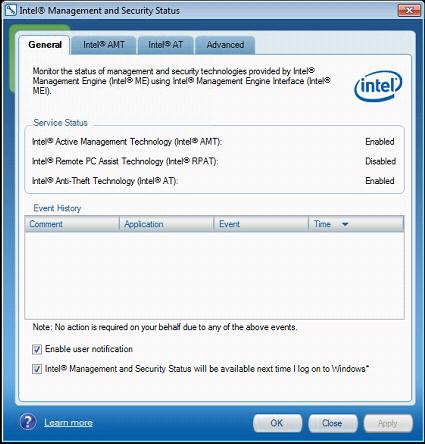
Newer versions bring anti-theft technologies to the table for mobile devices. If your notebook happens to have a cellular modem (or dongle), it can be controlled in a manner similar to mobile device management for smartphones.
Locked out
Notebooks so equipped can be sent a "poison pill" SMS message, which locks the notebook into an unusable state (you can customise the lock message).
The system can also be locked if there are too many invalid login attempts, or the system hasn’t "called home" within the specified time.
It can all be accessed without expensive third-party software
If the cellular modem contains a GPS radio, then vPro can scrape the location information and send that back to home base. Intel calls this Locator Beacon. Systems can be configured to report their location on a regular basis, as a one-time item, or continuously if suspected stolen.
Given Intel’s ambitions to take on ARM on its own turf, this has profound implications for embedded, cellular and tablet markets. The consumerisation of IT starts to look a lot less daunting when you can tie this level of security to the device.
The last important feature on the checklist is Intel’s Identity Protection Technology, a hardware implementation of a one-time key. Every 30 seconds, a new key is randomly generated, to be used along with passwords as a form of two-factor authentication to access online resources that require additional security.
This is an impressive array of remote management features for any desktop. What is even more impressive is that it can all be accessed without expensive third-party management software. Intel has made all of this accessible via either the vPro APIs or a vPro system’s built-in management web site interface for an additional hardware cost of less than $50 for the average desktop.
Just because you can manage your fleet of vPro systems without full-blown desktop management software does not mean that you should. vPro really shines when you pair it with software-based management systems to provide a single unified interface controlling all aspects of your desktop environments.
Using software such as Altiris or Microsoft’s System Center suite gives you the best overview of the devices in your care. Picture an interface with a list of properly grouped PCs, the ability to click a single button and reboot or remote control a computer.
You can poll asset information from these systems to see what hardware they contain or what software is installed. You can view patch levels schedule updates, review policies and even check the physical location of devices.
While vPro is certainly important as a support tool, it also has possibilities as an administration tool.
One example is re-imaging an entire lab full of PCs on a schedule. Create an ISO image with your favorite system imaging application and set it up in such a way that it automatically pulls an image from a known location, wipes the local system and applies the image. Set up a vPro script to reboot all the PCs in the lab and boot from the ISO.
BlackBerry flavour
This same concept can be applied to software installs while the operating system is enabled. Not all software comes nicely wrapped in an msi file for distribution via group policy. A combination of vPro scripting and operating system scripting could make an ISO available to a group of PCs so that operating system side scripts could execute the install.
For high security requirement systems, you can script changes in system defenses. Imagine simply turning off the network card on systems except when absolutely necessary to push new data to the device.
vPro provides the ability not simply to manage but to automate configuration and security independently of the operating system. That alone is worth a look.
In five short years we have seen an interesting IP-KVM with a lot of restrictions become a nearly complete out-of-band endpoint management system. Most companies should be making vPro mandatory.
Quite apart from the support enhancements it brings, when combined with proper software management the mobile device management features put the notebook on par with a BlackBerry in terms of security.
Intel has taken the time to address the security concerns regarding the technology, and I fully expect them to continue to make future vPro systems even more impenetrable.
There is simply no good reason why you should not to be using vPro in the enterprise and an impressive feature list of reasons why you should. ®
