This article is more than 1 year old
Chrome is the most secured browser - new study
Firefox finishes last in 3 browser security race
Sin of omission
The report refers to sandboxing as a "standard best practice within many popular applications." Chrome implements sandboxes in versions that run on Windows, Mac OS X, and Linux. Microsoft deployed sandboxing more than five years ago, starting when users ran IE version 7 on Windows Vista or later versions of Windows. Even Apple, which commands a tiny fraction of the browser market, implemented a robust sandbox in versions of Safari that run on Lion, the latest release of OS X.
In this context, the continuing failure of Firefox to offer sandboxing features is hard to excuse.
In a statement issued prior to the release of Accuvant's report, Johnathan Nightingale, Mozilla's director of Firefox engineering, said:
"Firefox includes a broad array of technologies to eliminate or reduce security threats, from platform level features like address space randomization to internal systems like our layout frame poisoning system. Sandboxing is a useful addition to that toolbox that we are investigating, but no technology is a silver bullet. We invest in security throughout the development process with internal and external code reviews, constant testing and analysis of running code, and rapid response to security issues when they emerge. We're proud of our reputation on security, and it remains a central priority for Firefox.
Reining in add-ons
The researchers also gave Chrome high marks for the strict limitations it places on software add-ons that extend the things users can do with the browser. As a result, attackers who manage to exploit extension bugs or trick victims into installing malicious add-ons are severely limited in the damage they can do. By comparison, IE and Firefox give extensions much wider latitude. IE add-ons, for instance, have the ability to create processes and to access the Windows clipboard, which can be a means of funneling malicious data from one application to another.
The other area where Chrome outflanked its rivals was its offering of what's known as JIT hardening. Short for just in time, JIT refers to code that's compiled on the fly and executed inside the browser. Attackers have long relied on JIT techniques to convert JavaScript into malicious machine code that bypasses exploit mitigations such as ASLR.
JIT hardening in Chrome, and to a lesser extent in IE, counteract JIT attacks by compiling JavaScript in an unpredictable way that makes it hard for attackers to control. Mozilla developers have yet to implement the feature in Firefox.
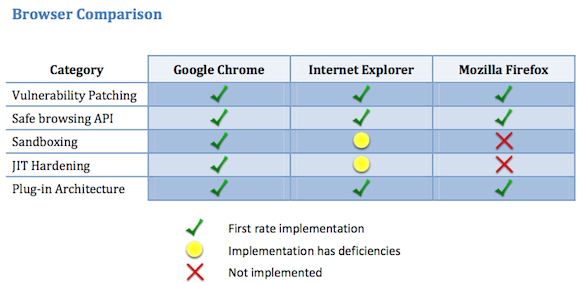
Accuvant rated Chrome and Firefix the most and least secured of the major browsers respectively (click to enlarge)
Besides ranking the security of the top three browsers, the paper argues that many of the metrics regularly used to gauge how well software stands up to hack attacks are unreliable. One such metric is the number of vulnerabilities patched, based on the assumption that more bugs indicate poorer-quality code than programs with fewer bugs. Other frequently cited factors include how quickly bugs are fixed and the severity of the bugs.
In the end, a browser will either succumb to a given exploit or it won't, and that's all that mattered to the paper's authors.
"We really didn't believe those [metrics] had much merit because it's really hard to correlate those things, especially between browsers and vendors," said Valasek, who along with Smith, was assisted by Accuvant colleagues Joshua Drake, Paul Mehta, Charlie Miller, and Shawn Moyer. "So we decided: Let's focus this paper on exploitation mitigation technology to show how these actually stand up against attackers when they find a vulnerability." ®
