This article is more than 1 year old
How Nokia managed to drive its in-house Linux train off the rails
When Meego lost its mojo
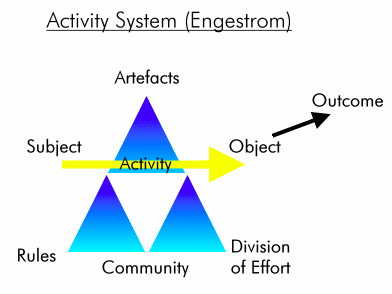
Activity Theory
"The Harmattan UI was originally based on the Activity Theory principle, a frame of reference for studying human behavior and development processes. The goal is to understand society, personality and, most importantly, how these two are connected. The theory was originally developed by the Russian psychologist Vygotsky," notes Taskumuro.
Does this make sense? We'll have a quiz at the end.
It turns out this isn't actually a theory at all, in any scientific sense. It isn't a falsifiable hypothesis. It has no predictive value. Wrap your chops around this to get a flavour:
Activities are open systems. When an activity system adopts a new element from the outside (for example, a new technology or a new object), it often leads to an aggravated secondary contradiction where some old element (for example, the rules or the division of labor) collides with the new one. Such contradictions generate disturbances and conflicts, but also innovate attempts to change the activity.
The "activity theory"-based UI absorbed an enormous amount of effort at Nokia, and the team missed the first deadline for a device. Product teams were waiting for a finished Maemo to put in the chassis of the Nokia N8 - for a phone code-named Columbus. But the resulting work was a UI that looked remarkably like everyone else's: a kind of 'digital dashboard'. The theory-based UI was abandoned at the end of 2009. The N8 eventually appeared in 2010, but Columbus had to be cancelled.
Back to the drawing board: the Harmattan UI was abandoned
The Harmattan UI's replacement was a generic 'Simple Dali' design, intended to be finished by July 2010. But this a bare bones UI was deemed to insufficiently different from any one else's UI. The third UI was Swipe, and knocked together quickly. This was eventually what appeared in the N9 last year.
According to Nokia roadmaps, before Meego was sidelined the N9 was due to be called the N9-01. Preceding this N9 would be a keyboard communicator design, very similar to the Symbian-based E7, only running the Swipe UI. It was cancelled close to the production date.
The report also has some details of Nokia's cancelled tablet - codenamed 'Senna' and using the same design language as the N9 (and subsequent Lumia 800 and 900) - but much larger.
There were more bumps which eventually caused the wheels to fall off Nokia's Linux.

The fourth generation tablet, the N900 ,also made phone calls
Intel had thrown enormous resources behind the WiMAX technology, which was a market flop - network operators opted for LTE instead, and investors didn't fancy setting up hugely expensive rival WiMAX networks to vie with LTE. One exception was ClearWire, which has since switched to LTE. Similarly, the only major network to bet on WiMAX, Sprint, is also now turning to LTE. Intel has also had to acknowledge reality and play catch-up: it doesn't today have WiMAX support for its Atom chips.
As Meego became the "platform of the future", staff piled in - it was the "hot" development project to work on. But as the report notes:
"Everyone inside Nokia had their opinion on MeeGo and the MeeGo team listened [to] everyone."

What might have been:
The never-released Nokia N950 brought a QWERTY slider keyboard to the slick N9 Swipe UI.
And finally, Nokia failed to win cross-industry support for MeeGo from rival manufacturers. They were perfectly happy with Google's Android, which had given them a competitive platform, and was yet to be ruffled by licensing and patent issues.
"In the war of the ecosystems, breaking into the North American market without LTE support and proper support from other manufacturers and operators would have been an impossible task for Nokia," The Taskumuro report continues.
Too much, too late?
As we've discussed before, Nokia's long-term vision can't be faulted - it embarked on developing a rich mobile tablet OS years before the market demanded one, and bravely kept the project going through years of poor sales.
The iPhone's success saw the market demand for devices which were primarily tablets, information devices, but with added cellular phone capability. By that time Nokia had one in the bag, and it was mature. But it wasted valuable time with conflicting and anarchic development efforts. It couldn't ship. Yet almost anything would have been an improvement on Symbian, which was tarnishing Nokia's reputation - particularly after the N97 debacle. It's tantalising to think what might have been if Nokia had shipped the N9 two years earlier, in the summer or autumn of 2009.
Success tends to breed success - people want in. Perhaps with a popular Meego product Nokia could have picked up some licensees nervous about a reliance on Android. Who knows?
As it was, Nokia finally had a competitive platform but would have had to go it alone. That wasn't a gamble that Elop was prepared to take. Microsoft now does the heavy lifting, at huge expense, to will the "third ecosystem" of Metro into existence.
Well done to Sampsa Kurri - who we believe wrote the feature, which isn't bylined - for teasing out some new details.
It's all over here.®
