This article is more than 1 year old
Happy birthday, Lisa: Apple's slow but heavy workhorse turns 30
The story of the machine the Mac maker would rather you forgot
Software Development
Some Apple history books give the impression that Steve Jobs just waltzed into Xerox Parc, had a chat with the guys there, and plagiarised the company’s research efforts. The fact is, at some point, a deal was struck where Xerox could acquire 100,000 pre-IPO stock from Apple for $1m and, in return, Jobs and a handful of Apple engineers were granted access to Xerox's non-public technology for a few days.

Evidently, Xerox was focussed on maintaining existing revenue streams from its profitable photocopier business and thought its internal research efforts were not ready for primetime. The business believed that its labs would only develop specialised technology for institutions and corporations that could afford it, and the costs would be prohibitive for the mainstream. So the pre-IPO shares package seemed like a good deal to Xerox and if Apple could make something of these ideas, well, the Cupertino kids could knock themselves out. Xerox didn't hold its breath.
Raskin takes credit for suggesting the PARC visit – he’d been a visiting scholar while at Stanford – but his intention was to get Jobs to see the technologies being demonstrated there to clarify similar work already going on at Apple, most notably with his Macintosh project. Indeed, the work at PARC wasn’t especially secret, as the Xerox Alto computer – the first to incorporate a mouse and graphical user interface (GUI) – had been demonstrated numerous times in the 1970s; about 2,000 people got a viewing in 1975.
And being a research facility, it published papers covering its work that would have been widely read throughout the industry. Byte magazine even ran an in-depth piece on the labs' Smalltalk System-80 in 1981.
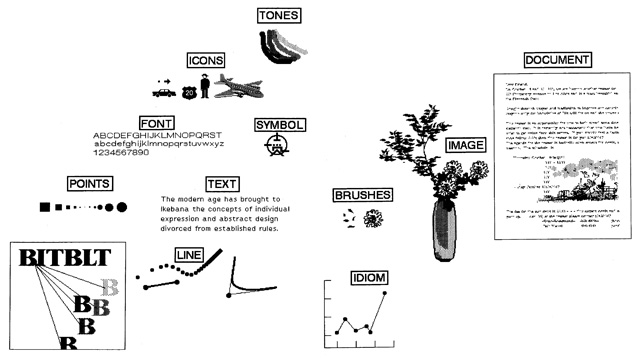
Smalltalk-80 graphics: Points, Rectangles, Forms, Pens, and Text are five kinds of objects used to create a wide range of imagery
Certainly Raskin’s plan worked as Jobs did see technologies including networking, object-oriented programming and large portrait bitmapped displays running what-you-see-is-what-you-get (WYSIWYG) editing of text and graphics among other things. But it was the GUI on the bitmapped display that stuck in Jobs’ mind. Although Raskin had been emphatic about bitmapped screens as the future and as part of his Macintosh project, up until that point, the Apple Lisa’s early development proposal had been for a machine that churned out characters on a green screen.
The Xerox Star 8010 was described as an “an executive workstation” and was the commercial culmination of the Alto computer. A seat at the machine cost around $16,000. Yet this workstation was part of an office system that included Ethernet networking, print servers and laser printing with a total cost of about $75,000; additional machines cost $16k. While Xerox did manage to produce about 25,000 systems, the concept hadn’t been intended as a commercial product.
Apple also welcomed aboard 15 Xerox staffers after the visit. Among them was Larry Tesler who jumped ship from Xerox in July 1980, seven months after the PARC visit where he had demonstrated the mouse – a device borrowed by the work of Douglas Engelbart and Bill English at the Stanford Research Institute. In fact, at some point just about everybody in the industry borrowed from Engelbart following his showing of his NLS (oN-Line System) work in 1968, later dubbed the Mother of all Demos.
The mouse was used to operate Smalltalk, an object-oriented software programming environment, devised chiefly by Alan Kay. For many, Kay’s work is the stuff of legend and, given the questions asked by Apple engineers during the PARC visits, it was obvious they had studied Smalltalk before showing up. Xerox staffers even remarked that the experience was like talking to members of their own team.
In Smalltalk-80: The Language and its Implementation (the Bluebook) by Adele Goldberg and David Robson, it is described as:
…a language of description (a programming language) which serves as an interface between the models in the human mind and those in computing hardware, and a language of interaction (a user interface) which matches the human communication system to that of the computer.
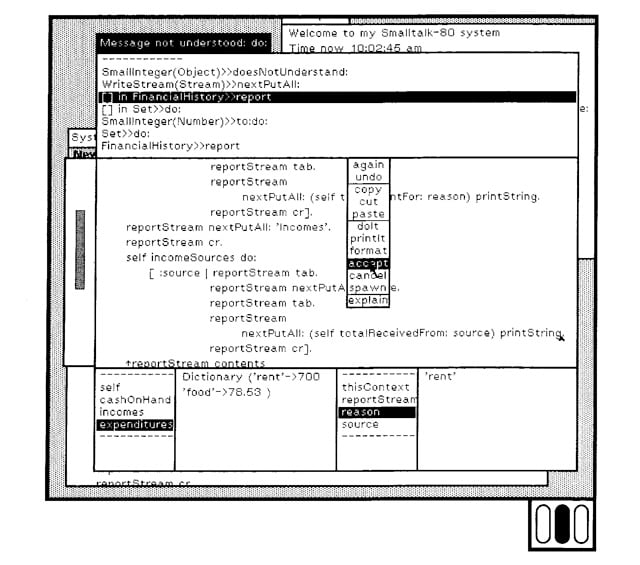
Programming the easy way, courtesy of Smalltalk
Here, the Xerox focus is on making programming easier, much easier. Yet Jobs was inspired to work on making the whole computing experience easier, and the differences are vast. With input from Jobs and help from Glenn Edens, engineer Trip Hawkins – who would later go on to found games giant EA – redefined the spec for the Apple Lisa to combine the mouse and the GUI as key features for direct user manipulation of the objects on-screen. The target audience of business customers would remain, but the Lisa had a renewed purpose and it was to render alternative business computing platforms obsolete.
Kay eventually left Xerox for Atari and later became an Apple Fellow in 1984. Bruce Horn was largely responsible for the Smalltalk microcode used on the Xerox Dorado – a Xerox Star prototype – and he joined Apple in 1981.
