This article is more than 1 year old
WTF is... the Quantified Self?
Human hacking by the numbers
Me. Myself. I
Ex-banker and personal data advocate Adriana Lukas has been running the London QS group since its inception in September 2010 in a small AV-equipped room in University College London. “We had 30 people in the early days,” says Lukas, “and I always arranged them in a circle for conversations.” Show-and-Tell – individuals presenting their methods and objectives to the rest of the group – is a central part of the original Wolf-Kelly concept, but Lukas was keen to avoid the kind of presenter/audience divide typical of the lecture hall. “Show-and-tell was kind of optional,” says Lukas. “But as the numbers grew – you can’t have a conversation when you have 100 people in the room.”
Currently London QS meetings take place – every six weeks or so – in the larger facilities offered by Google’s Campus in Bonhill St, East London.

Not just for jogger: gadgets like Fitbit's One help you record life data
QSers tend to call themselves “self-hackers”, a description coined by Kevin Kelly, who was struck by the similarity between the movement’s early adopters and the amateur personal computer pioneers who formed Silicon Valley’s Homebrew Computer Club in the mid-1970s. Back then if you wanted a computer you had to build your own. There wasn’t a lot you could do with it, except help other people build theirs. What was it for? Who knew? But it was taken for granted that in some way yet to be discovered, personal computers were the Wave of the Future.
“People were driven to build and use those computers because they had a real personal meaning,” says Gary Wolf. And today’s self-hackers feel much the same way about their sensors and data sets.
Adriana Lukas doesn’t mess with the gadgets herself, although at one stage she did experiment with FitBit, a belt clip-on with a motion sensor that measures daily activity. When she lost it she realised her interest was not so much in her own data, but in the more general questions: personal data security and the problem of how to extract meaning from an ocean of raw numerics. So Lukas is hardly your typical self-hacker. But then none of them are. Every QS aficionado seems to have his or her own personal agenda.
Personal data
Sacha Chua, ex-IBM and now a professional social media consultant, occupies what you might call the hardcore end of the QS spectrum. Over the course of last year she collected a formidable amount of data on the overall use of her time. Her main categories include:
- Sleep
- Discretionary time spent on hobbies/socialising
- Personal care routines and exercise
- Paid Work
- Unpaid work, including commuting, shopping, household tasks
- Business skills development
Chua has graphed and correlated these data from 2012 with a view to making the most of her time in 2013. There’s a serious weight of information here, needing some sophisticated statistics to extract meaning. Andy Leigh of the London QS group has a rather more straightforward goal: he simply wants to lose weight – by rowing round the world. In his bedroom.
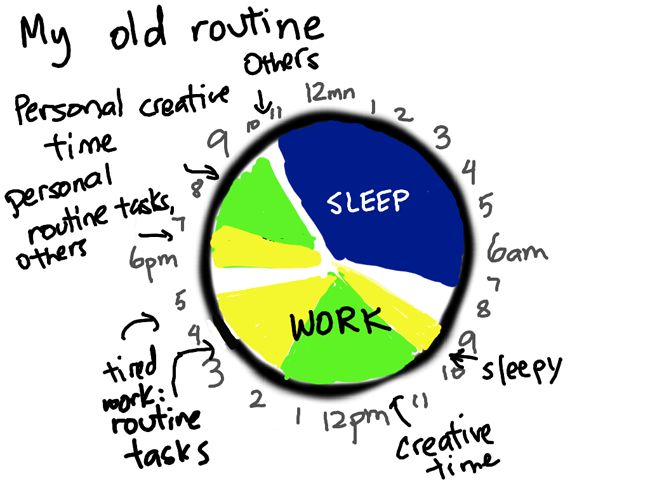
Sascha Chua used extensive QS techniques to straighten out her chaotic day...
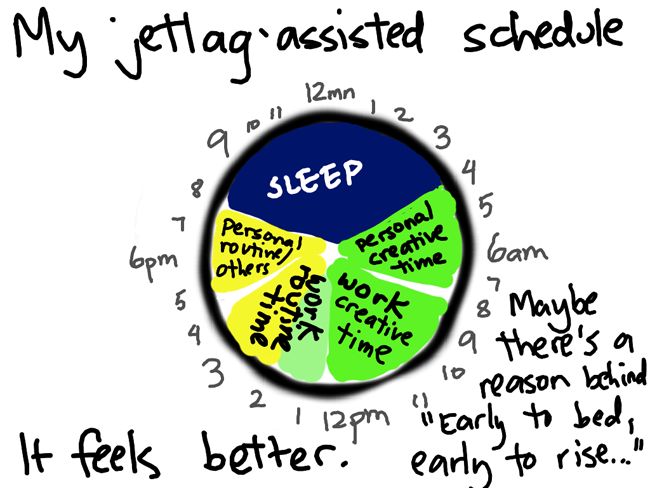
...and organise it into a more productive pattern
Following an injury that restricted a good deal of his customary physical activity, Leigh put on fat. He learned that rowing, if done correctly, could be a useful low-impact exercise. Inspired by the example of Guinness record holder Dave Holby, Leigh ordered himself a rowing machine.
It arrived broken. “So before sending it back, I did what any geek would to do — I took it apart to see how it worked.” Armed with the information of where the machine’s sensors were and how they connected to the front panel display, when the replacement arrived Leigh was able to install his own Arduino in place of the inbuilt proprietary black box.
“The Arduino’s a little computer on a board,” Leigh explained at his London QS Show-and-Tell, “an open source electronics platform that allows you to prototype projects without spending a lot of money and without having to do too much in the way of building stuff yourself.”
