This article is more than 1 year old
Google hit by building automation security FAIL
Choc Factory's Oz HQ hacked by researchers
The building housing Google Australia's lavish Sydney headquarters is running the known-vulnerable Tridium Niagara building management system, and has been compromised by the Cylance researchers who have made Niagara their mission.
The researchers identified the underlying system – QNX on an embedded system – and extracted the admin password from the system's config file. After that, as the company's blog post explains, they were able to wander around the control environment pretty much at will.
Billy Rios and Terry McCorkle demonstrate the successful attack by posting the building's Level 3 layout, water, and air-conditioning systems with the blog post. They also mention an “after hours button” they said they were “afraid to test” because of its hammer symbol in the system (hint: it probably merely activates the doors so people can get out after the doors have been switched off).
The Cylance gents admit that this vulnerability posting – which has been reported to Google – is linkbait in the service of awareness-raising.
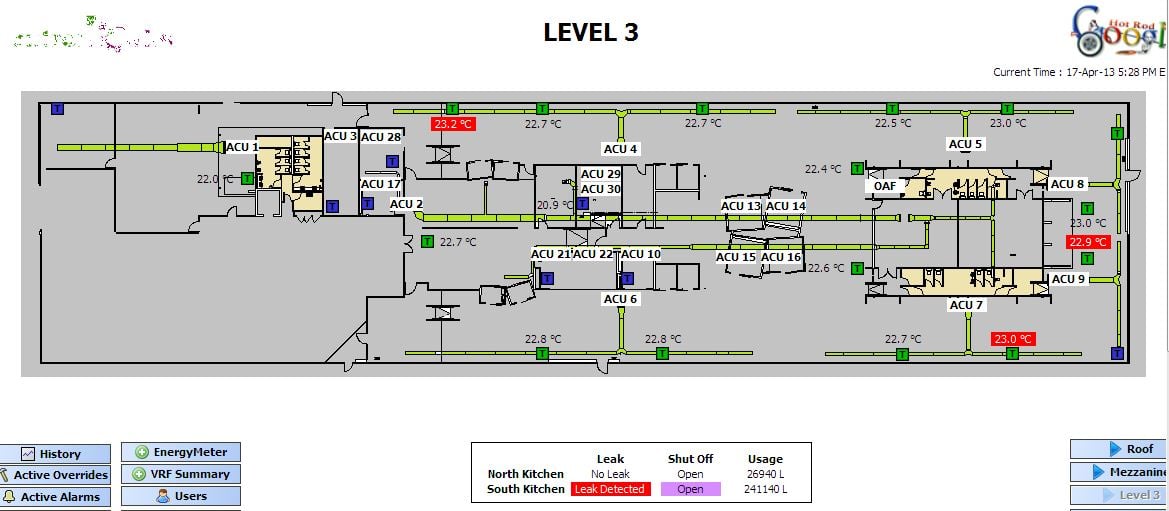
Plumber pr0n: The Level 3 water and HVAC layout of an office inhabited by Google Australia
“At the time of this blog post, this exact issue affects tens of thousands of devices on the Internet and thousands of different organizations. Thank you Google for helping us raise awareness on this issue!” they write.
They noted that the Google vulnerability was present because the building in which the company resides was running an older version of the Niagara system, so there's likely to be a contractor with some explaining to do.
The Tridium kit had a patch in August 2012, after Cylance went public over its vulnerabilities. ®
