This article is more than 1 year old
How the NSA hacks PCs, phones, routers, hard disks 'at speed of light': Spy tech catalog leaks
It's not as bad as you thought - it's much worse
The cellphone network you are connected to is not the network you want
Mobile communications are also wide open, it seems. The NSA catalog offers a mobile base station called the Typhon HX (priced at $175,800) that will mimic a network provider's infrastructure and collect mobile signals to decode and study; it effectively taps cellphones.
Appelbaum said this type of hacking was spotted in action by the Ecuadorian embassy shortly after Julian Assange arrived as a house guest. The embassy's staff started getting welcome messages from Uganda Telecom on their mobile because the British intelligence services hadn't reconfigured their data slurping base-station correctly from a previous operation, apparently.
Mobile phone SIM cards can also be easily hacked, the documents claim, using a tool dubbed MONKEYCALANDER. This exploits a flaw, only recently spotted by security researchers but used by the NSA since 2007, that allows code to be installed on a SIM card that will track and monitor an individual user's calls and location.
The catalog also details an exploit called DROPOUTJEEP which claims it can gain complete control of an Apple iPhone via a backdoor, at least back in 2007 when the cyberweapon catalog was drawn up. The NSA says the DROPOUTJEEP exploit has a 100 per cent success rate, leading Applebaum to speculate that Cupertino may have helped the NSA out with the software. The first version of DROPOUTJEEP needed an agent to get his or her hands on the device, but remotely launched versions were promised.
Also listed is flash ROM malware for compromising satellite phones, in case you felt like using that, plus exploits to remotely control Windows Mobile handsets.
Speaking of Windows, NIGHTSTAND is a handy little box of tricks that can, with a range of 8 miles, transmit carefully crafted Wi-Fi traffic to potentially gain control of a PC running Windows XP and Internet Explorer. A tiny Linux-powered computer called SPARROW II can be fitted to drones to scope out poorly secured wireless networks from the skies.
Your hard disk is not the device you thought it was
Hard drives are also easy meat for the NSA, according to the documents. Software called IRATEMONK can be installed on the firmware in disks from Western Digital, Seagate, Maxtor, and Samsung to allow full access to the target's data and operating system. And because it's flashed onto the chips, via other remotely installed malware, the customized firmware is almost impossible to detect. This allows spies to hide and execute anything they like on the connected computer, even if the drive is wiped.
If you want to see how a reprogrammed disk firmware can silently alter files, turn to this independent, earlier research. An example target of IRATEMONK cited by the NSA is a cyber-cafe of PCs.
"Western Digital has no knowledge of, nor has it participated in the development of technology by government entities that create ‘implants’ on Western Digital hard drives, as Der Spiegel described," a WD spokesperson told El Reg in a statement.
The parcels from Amazon are not the parcels you want
On the hardware front, the TAO hacking team also has specialists in "close access operations" or "Off Net" projects where physical access is required to a target's system. This can involve intercepting laptops ordered online from Amazon and others, adding tracking hardware, and then delivering them as normal in the correct packaging, as well as breaking into private property for hardware installation.
The catalog offers a number of hardware tools that can be installed by a g-man. $200,000, for example, will buy you 50 USB cables that have a secondary radio communications system called COTTONMOUTH that allows the agency to send and collect data directly through the ether. A VGA monitor cable called RAGEMASTER intercepts video signals and beams them to a nearby government snoop using a radar-based technique. A similar device exists for keyboards.
Those cables were built by the NSA's ANT team, which also has a fondness for attacking and infiltrating the firmware on your PC: this is the low-level software that's not without its bugs, first to run, and boots your operating system. If this is compromised and reprogrammed using the ANT crew's SWAP program, then it's pretty much game over for the target as the whole system above the firmware can be remotely controlled and monitored as required. Another tool called WISTFULTOLL leaps upon Windows Management Instrumentation to access data on systems.
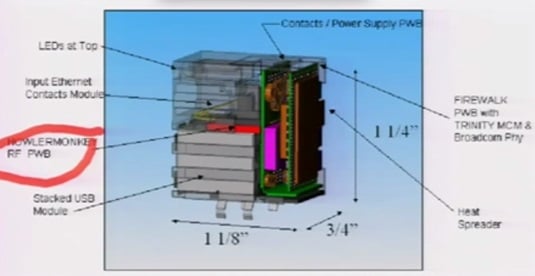
HOWLERMONKEY ... Check your Ethernet ports
The NSA has also developed a set of tiny surveillance electronics dubbed HOWLERMONKEY that hides within computer hardware, such as an ordinary Ethernet port, Appelbaum said. The one pictured above, dubbed FIREWALK, looks no different to a standard RJ45 socket, but can inject data into and slurp any bytes from packets coming through the physical connection automatically, and relay the information back to base via a radio link.
Wireless communications can also be subverted by installing a separate Wi-Fi card dubbed BULLDOZER. Even if the user has wireless switched off by default, a PCI-connected BULLDOZER can be used to link into a nearly subverted router and collect metadata and content from targeted systems.
Servers built by HP and Dell were also mentioned as an easily subverted system. Hardware dubbed GODSURGE can be fitted to a JTAG debugging port in Dell's PowerEdge machines to provide full access, and the catalog says such monitoring uses common off-the-shelf components that can't be directly attributed to the NSA.
IRONCHEF, we're told, is a BIOS-level nasty designed to target HP ProLiant kit; its PowerEdge cousin is called DEITYBOUNCE.
Where to find all the leaked information
The full document set has now been uploaded to whistleblowing website Cryptome for public perusal. Appelbaum and the Der Spiegel team have been careful to exclude the published names of NSA staff who carry out these attacks, and the names of the people and organizations the agency has targeted. An interactive infographic summarizing the leaks can be found here.
El Reg has contacted all of the companies named by Appelbaum in his presentation, but had limited response given that it’s the Christmas holidays. But if the dossier is to be believed, then there are going to be angry words between the NSA, manufacturers and hardware customers – the latter likely to be searching for more secure products.
Appelbaum said that he'd tried to talk to US legislators about the situation but was continually rebuffed. Part of the problem, he said, was that politicians don't understand the technology behind such systems, and in many cases the lawmakers don’t want to acknowledge there's a problem until a political solution has been worked out.
The leaked catalog is roughly six years old; new technologies developed in the mean time by the NSA (estimated annual budget: $10bn) are anyone's guess, or worst nightmares.
Readers may find some cheer, or not, from the suggestion that most of these techniques are used against highly targeted individuals rather than everyone en mass: NSA analysts need the help of the FBI and CIA to install the hidden hardware snoopers, for example, either by intercepting shipments or by carrying out a so-called black bag job.
The intelligence agencies argue they are combatting terrorism, a claim that is now being fought over in the US courts. Today, questions remain as to who exactly is scrutinizing these surveillance operations and to what level – and who else has their hands on these grave security vulnerabilities that the NSA is otherwise sitting on and secretly exploiting.
"The real problem is who is in charge here," Jon Callas, cofounder of the Silent Circle encrypted communications system, told The Register.
Referring to the secretive FISA court that supposedly oversees the NSA, Callas continued: "For us who are Americans we have the belief that we are ultimately in charge. Now it seems we have secret courts, with secret laws, so how do you run a free society under those kind of conditions?"
"We have a societal belief that some things are not acceptable and while Jake can be hyperbolic, I cheer him on – sunlight is the best disinfectant." ®
Bootnote
With the exception of SEASONEDMOTH, there's no mention of any of these exploits having a time-limited kill switch. Presumably the NSA has means of deactivating online taps, but one wonders how much kit is out there on eBay and with dealers that still contains examples of ANT's intrusive craft.
Applebaum suggests that those interested (which should include pretty much everyone in the security industry as well as IT departments purchasing on the grey market) should look for samples that use the RC6 block cipher and which emit encrypted UDP traffic.
Updated to add
Dell got in touch with us after publication to deny any involvement in the vulnerabilities exploited by the NSA:
We take very seriously any issues that may impact the integrity of our products or customer security and privacy. Should we become aware of a possible vulnerability in any of Dell’s products we will communicate with our customers in a transparent manner as we have done in the past.Dell does not work with any government – United States or otherwise – to compromise our products to make them potentially vulnerable for exploit. This includes ‘software implants’ or so-called ‘backdoors’ for any purpose whatsoever.
In a statement, Apple echoed much of what Dell and other vendors have said:
Apple has never worked with the NSA to create a backdoor in any of our products, including iPhone. Additionally, we have been unaware of this alleged NSA program targeting our products.Whenever we hear about attempts to undermine Apple’s industry-leading security, we thoroughly investigate and take appropriate steps to protect our customers. We will continue to use our resources to stay ahead of malicious hackers and defend our customers from security attacks, regardless of who’s behind them.
