This article is more than 1 year old
New XSS vuln hits eBay as rubbish passw0rds persist
Tat bazaars own password rules don't apply when users pick new sekrit w0rdz
eBay punters rushing to secure accounts could be selecting the world's worst passwords after the online tat bazaar was found accepting the most common and weakest passwords in contravention to its stated policy.
eBay has been slowly asking its users to reset account passwords after it admitted last week that unknown criminals made off with names, dates of birth, addresses, and proprietary hashed passwords.
It did not reveal the number of inactive accounts compromised and said hackers did not nab financial data nor pivot to PayPal after they broke in using staff credentials in late Feburary.
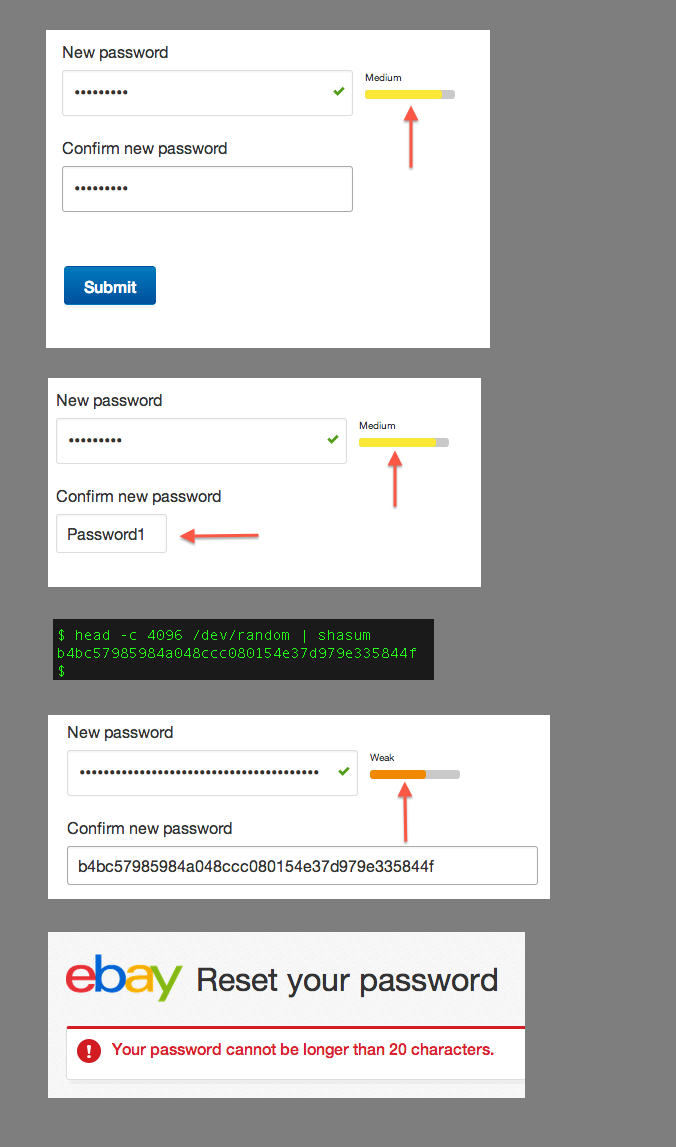
Crypto bod and co-founder of the TrueCrypt audit project Kenn White pointed out on Twitter that the bazaar accepted the world's most commonly used and low-entropy passwords while red-flagging and limiting stronger codes.
This writer has confirmed eBay accepted the most commonly used password as revealed in 2012 during its user password reset process. It also permitted those combinations explicitly marked unacceptable by eBay.
eBay's borked password system flagged high entropy (randomness) passwords generated by LastPass as weak, elevating more risky and common passwords as stronger options.
The system did not however allow users to enter passwords shorter than six characters (nor longer than 20) or those without an albeit weak number, letter or special symbol combination.
Researchers also reported and posted details on vulnerabilities within eBay web assets. Jordan Lee Jones (@CEHSecurity) reported an exploit developed in the MetaSploit security tool which allowed him to upload a shell via an eBay flash upload page.
An email from the British researcher to eBay security staff indicated the shell has been removed) and the vulnerability patched.
He also reported a cross site-scripting (XSS) vulnerbility in eBay's labs page which remained offline at the time of writing.
German researcher Michael E reported to Hacker News a separate and unpatched XSS in eBay which could allow attackers to create auction pages with unauthorised Javascript that could launch a payload to steal users' cookies. Ebay reused the cookies across sessions regardless of whether the victim logged out their account or reset passwords.
The vulnerabilities come as eBay took flak over its slow password reset procedure under which some affected users were only now receiving emails urging them to change their passwords.
The company could face fines of up to £500,000 from the Information Commissioner's Office. ®