This article is more than 1 year old
Lads from Lagos turn from 419 scams to basic malware slinging
Smooth-tongued online lovers struggle to get to grips with slimy RAT infestations
Nigerian scammers are developing beyond 419 advance-fee fraud scams against individuals by using trojans to steal valuable information from businesses instead.
Security researchers at Palo Alto Networks reports that cyber criminals in Nigeria have evolved common malware campaigns to infiltrate businesses that have not previously been their primary targets. Over the last three years or so the Lads from Lagos are using tools more commonly associated with comparatively sophisticated criminal and espionage groups in order to steal business-critical data from enterprises.
Today's Nigerian criminals are using Remote Administration Tools (RATs) and other malware available through underground forums, including commercial RATs such as NetWire, that establish complete control over infected systems. The Silver Spaniel malware associated with these attack is undergoing constant modification so that it stays one step ahead of anti-virus and other security software defences.
The cybercrooks also use a second (crypting) tool named DataScrambler to render the file undetectable by most antivirus engines before distributing the infection file as e-mail attachments. One such infected file was called “Quatation For Iran May Order.exe” and "New Samples Required.exe". The Nigerians are not coding the malware themselves, it is believed.
The DarkComet RAT has also cropped up in some attacks linked to Nigeria. The attackers configure each RAT to connect to a dynamic DNS domain obtained from NoIP.com, which they access through a VPN. The NetWire RAT retails from $40 (basic) to $140 ("professional", fully featured) through various underground forums.
It's all pretty basic stuff but potentially effective nonetheless.
“These Silver Spaniel malware activities originate in Nigeria and employ tactics, techniques and procedures similar to one another," said Ryan Olson, Unit 42 Intelligence Director, Palo Alto Networks. "The actors don’t show a high level of technical acumen, but represent a growing threat to businesses that have not previously been their primary targets.”
Back in the day 419 scams were a cottage (or more accurately cyber-cafe) industry across west Africa and South Africa. Crooks spammed out a deluge of implausible letters in the faint hope of catching the occasional credulous soul who would act on the implausible claims they made.
Prospective marks were typically promised a cut in the share of funds / inheritance supposedly held in a bank account in exchange for their help as a supposed recipient of the funds. Victims are encouraged to cough up an escalating quantity of fees up front in the hopes of getting their hands on this non-existent windfall. In some cases victims are induced into travelling to Nigeria to meet supposed lawyers or other middlemen. In such cases a mark is likely to end up driven out of town and beaten before being robbed. The 419 moniker comes from the section of Nigerian's penal code dealing with such crimes.
419 scammers are typically experts at social engineering, but novices with malware. Even so Palo Alto customers in Taiwan and South Korea have been targeted for attack by western African ne'er do wells over recent months.
Some of that brazen culture remains even for those nowadays becoming malware slingers. One scammer - using the moniker Engr Ojie Victor - has even been using Facebook to get help with his scam, complaining that the malware he has acquired doesn't work properly, Palo Alto reports.
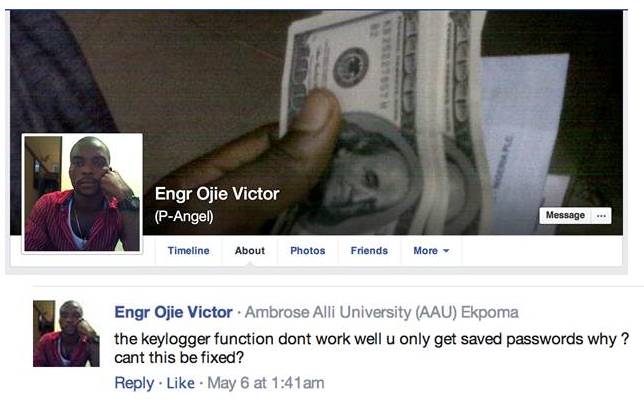
Lad from Lagos struggles with RAT infestation
The cover photo of Victor's Facebook profile shows a hand holding a small stack of $100 bills. This is one of many photos of cash posted on his Facebook page, which uses the custom URL https://www.facebook.com/lovenotwars - which was open to the public prior to its recent takedown.
Victor apparently uses the handle “lovenotwars” in many locations on the internet, including dating sites where he claims to be a middle-aged man seeking love in Canada, the US and multiple Scandinavian countries. Multiple profiles established around 2011 all contain similar content, something Palo Alto researchers regard as highly suspicious.
"Scammers often use fake dating profiles to lure individuals into thinking they have entered an online relationship, only to be scammed out of hundreds or thousands of dollars," the security researchers warn.
Evidently the OpSec skills of the Lads from Lagos lag a long way between those of Chinese, Russian or US state-sponsored hackers.
"While these actors are not nearly as sophisticated as the top cyber crime and espionage groups in the world, we believe they represent an emerging threat to businesses," Palo Alto warns.
A white-paper by Palo Alto's newly formed Unit 42 threat intelligence team on 419 Evolution can be found here (PDF). ®
