This article is more than 1 year old
Uni boffins: 'Accurate' Android AV app outperforms most rivals
...Don't sweat, VXers, it's STILL no use against hidden nasties
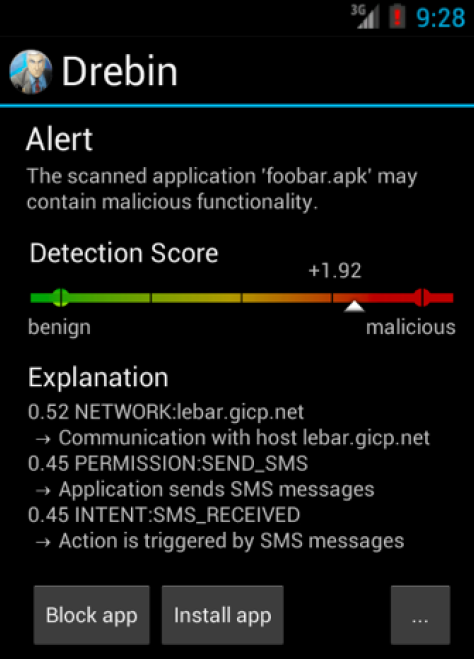
German researchers have built an Android app capable of detecting 94 percent of malware quick enough to run on mobile devices they say bests current offerings in effectiveness and description.
Daniel Arp, Konrad Rieck, Malte Hubner and Hugo Gascon of the University of Gottingen – together with Michael Spreitzenbarth of Siemens computer emergency response team – pitted their DREBIN tool against 123,453 benign applications from different Android app stores and 5560 new malware samples, the largest set yet used.
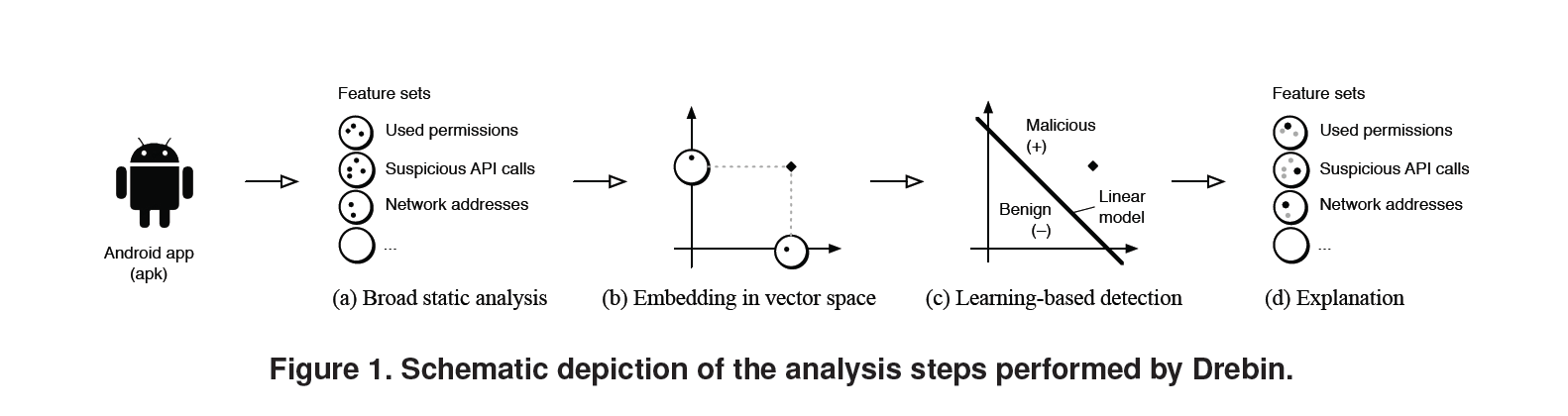
"As the limited resources impede monitoring applications at run-time, DREBIN performs a broad static analysis, gathering as many features of an application as possible," the researchers wrote in the paper DREBIN: Effective and Explainable Detection of Android Malware in Your Pocket (PDF).
"... DREBIN outperforms several related approaches and detects 94 percent of the malware with few false alarms (one percent false-positive), where the explanations provided for each detection reveal relevant properties of the detected malware.
"To the best of our knowledge, DREBIN is the first method which provides effective and explainable detection of Android malware directly on smartphone devices."
It took the app 10 seconds to analyse five modern Android phones making it suitable for screening downloaded apps on the device. Older phones took about 20 seconds to scan while on a 2.26Ghz core duo desktop with 4Gb of RAM the tool could scan a whopping 100,000 apps a day.
Dynamically loaded and obfuscated malware – the bane of anti-malware offerings – could still give DREBIN the slip, the authors concede.
Its use of static analysis was another limitation in which the retrieved code of detected malware was inaccessible. This area was the subject of future research.
However its combination of static analysis and machine learning remained effective in making compromise more expensive for attackers by forcing them to better hide their malware. It could also detect efforts by VXers to repack malware or insert junk data.
DREBIN gathered information on a target app's code and manifest which were organised into strings including permissions and API calls, and embedded in a joint vector space.
"As an example, an application sending premium SMS messages is cast to a specific region in the vector space associated with the corresponding permissions, intents and API calls," the researchers wrote. "This geometric representation enables DREBIN to identify combinations and patterns of features indicative for malware automatically using machine learning techniques."
Various platforms had been proposed to help save users who blindly OK app permissions from themselves. Existing systems such as TaintDroid, DroidRanger and RiskRanker were effective, but relied on manually crafted detection patterns that would miss some new malware and may come with large device performance cost.
Rival antivirus tools running at a one perc ent false-positive rate detected between 10 to 50 per cent of malware, while DREBIN found 94 per cent. The researchers put its additional detection capabilities in part on the ability to monitor requested permissions, suspicious API calls, intent filters and network addresses. ®