This article is more than 1 year old
User flexibility without the risk
Don’t stumble into the responsibility void
Most organisations are seeing users and business groups starting to make their own technology decisions to some degree or another. On the one hand this provides those in the business with the freedom and flexibility they often crave, but unilateral adoption of equipment, software and services can create ambiguity over who is responsible for what. Action therefore needs to be taken to ensure that costs and risks do not escalate out of control.
User driven activity is broader than you might think
BYOD, employees using personal equipment for work purposes, has been a hot topic in the industry. However, it’s not BYOD per se that matters, it’s that users and local departments are making decisions about technology independently of the IT department. This applies both to employee related purchases, and where devices have been funded out of local budgets or on expenses. While most BYOD related conversations focus purely on mobile devices, in a recent Reg reader study conducted by Freeform Dynamics we found that unilateral user or local departmental activity was actually much broader than this. From a device perspective, a lot of respondents were also seeing activity around desktops and laptops.
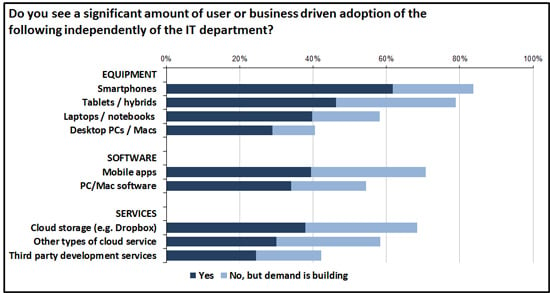
Furthermore, regardless of device type, purchasing activity didn’t stop here – with mobile devices pulling through the use of mobile apps, and Macs and PCs pulling through software. In addition, adoption of various types of cloud and Internet services, which may or may not be associated with equipment-related decisions, was also apparent (Figure 1).
It’s probably worth stressing that the data we are looking at on this chart is based on asking respondents whether they are already seeing or anticipating a ‘significant amount’ of activity taking place independently of the IT department. Realistically, this means adoption has already gone beyond the point where it can be ignored or dealt with on a case-by-case basis. And despite the fact that this kind of activity is normally centred around specific groups or types of users, if these collectively add up to more than a few percent of the workforce in your organisation, you need to think about who is responsible for what.
Make sure you don’t stumble into the responsibility void
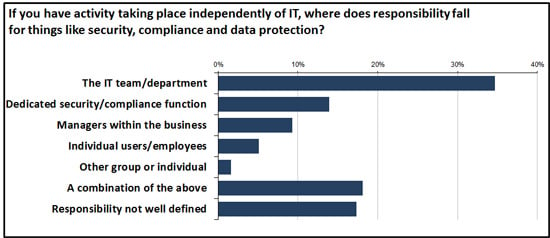
Historically, the IT department has taken care of things like security, compliance, and data protection. Indeed the technology procurement process often takes these things into account when IT is in control, along with things like manageability, future proofing, fitness for purpose, and so on. But what happens when IT is not involved in selecting and acquiring solutions? After all, you cannot expect the IT team to manage things over which they have no control, or are not aware of. Nevertheless, the research tells us that even when employees and business units are acting unilaterally, IT is still held responsible for some pretty fundamental aspects of risk management in a third of cases (Figure 2).
When IT is picking up responsibility in this way, there could be a couple of things behind this. It may be that there are mechanisms in place for employees or local business units to declare any additional technology in use so that IT is notified and is able to put appropriate safeguards in place as necessary. This will almost certainly represent additional overhead (compared to the use of solutions procured through the traditional IT route), but at least any potential exposure will be covered.
Feedback from participants in the research, however, suggests that in many cases the IT team only gets to know about what’s in use through network monitoring tools or, more frequently, when something goes wrong and the user or the manager comes running for help. Either way, IT is left in the impossible position of having responsibility without the necessary authority.
But what happens in the other two thirds of cases? As we look at the above chart it is clear that responsibility is often ill-defined or allocated to people who may not have the knowledge and experience to understand the risks, let alone what action to take to manage them. In effect, we end up with a responsibility void.
Communicate well and maintain as much visibility as you can
If you know or suspect that a responsibility void has opened up in your organisation, or you see things heading in this direction, what can you do about it? First and foremost you need to make sure that there’s a good dialogue between IT and the business. This needs to start at a fairly high level because business executives and managers don’t naturally spend a lot of time considering the type of things that can go wrong if the proper controls aren't in place. As part of this, where necessary, senior managers need to be reminded that risk management is fundamentally a business rather than an IT issue, and that IT is willing to help, but can only do so if the business cooperates. If there are bridges to be repaired for whatever reason e.g. because past rifts have opened up between the IT department and its internal clients, these need to be acknowledged and addressed.
When it comes to procuring equipment, software and services, it makes sense to have the IT team provide support at one level or another even if it is not directly involved in the decision-making process. This may take the form of documented guidance on the things to think about when selecting solutions, and even policies that draw the line between what’s acceptable and what’s not, setting out conditions and prerequisites for appropriate use. In order to prevent the IT team being seen as ‘kill-joys’, however, it must be made clear that these are company policies or guidelines, i.e. authorised by senior management for solid business reasons.
Of course beyond the people side of things there’s also a lot of technology out there that can help, from virtualisation solutions which keep sensitive data centralised, through management and security software to control and protect information on end user devices, to monitoring tools which help you track what’s going on in general. The strictness of the measures you put into place will vary depending on your needs and culture. At the very minimum, though, you would be advised to have in place at least some level of policy, user awareness training, and mechanisms to provide visibility, even if you trust users to do the right thing on a day-to-day basis.
If you’re interested in more detail on some of the points discussed above, we would encourage you to download the full report associated with the research we have referenced. It’s available here.