This article is more than 1 year old
Microsoft blunts hooks of nasty Internet Explorer phishing flaw
Hacker drops policy bypass disclosure
Microsoft is investigating an alleged vulnerability in its flagship Internet Explorer browser.
The cross-site scripting hole disclosed Saturday by hacker David Leo includes functional proof of concept code, according to confirmed reports.
Vulture South reported the flaw to Microsoft Friday and has been told it is working to develop a patch. We've not been offered a timeframe fo the fix.
The flaw reportedly works against updated instances of the browser operating on Windows 7.
We shall not link to the flaw because the demonstration page runs a heap of scripts, but if you want to see it at work point your browser to http://www.deusen.co.uk/items/insider3show.3362009741042107, where Leo explains the exploit.
Tumblr security bod Joey Fowler writing on the Full Disclosure mailing list said the vulnerability was a credible and dangerous threat.
"As long as the page(s) being framed don't contain X-Frame-Options headers (with `deny` or `same-origin` values), it executes successfully," Fowler said in a confirmed post.
"Pending the payload being injected, most Content Security Policies are also bypassed (by injecting HTML instead of JavaScript)."
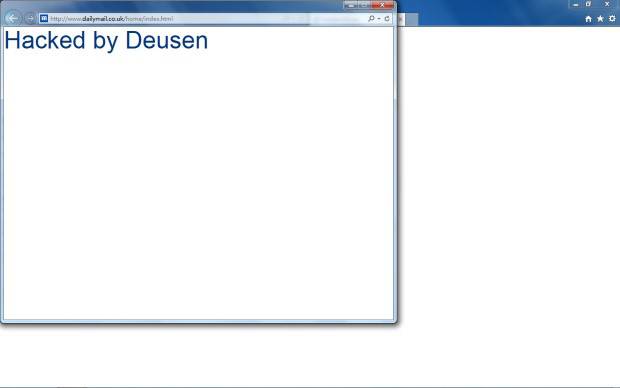
Fowler said it made available all viable cross-site scripting vectors to attackers.
Leo used "news" site The Daily Mail to demonstrate the attack. Internet Explorer users clicking his crafted would be served a prompt and direct users to the mail page where an external page was loaded reading 'hacked by Deusen'.
The browser address bar would remain unchanged during the attack making it an attractive means of phishing users which could easily be used in live attacks prior to Redmond releasing a patch. ®
