This article is more than 1 year old
Jamie Oliver serves up steaming pile of malware
Hacker recipe: a dash of Flash, a sprinkle of Silverlight, a pinch of Java and YOU'RE DONE
Tousle-haired celebrity chef Jamie Oliver has served up a stomach-churning exploit kit to those who visit his web site.
His eponymous .com site, ranked 519 in the UK and drawing some 10 million visitors a month was compromised to plate-up the foul-tasting Fiesta exploit kit to compromise user machines.
Malwarebytes senior researcher Jérôme Segura said crook cooks orchestrated a "carefully and well hidden" attack and hid an iframe URL with base-64 encoding.
"The web masters will need to look for additional evidence of infection, rather than simply restore or delete the offending script," Segura said in an advisory.
"Stolen login credentials or a vulnerable plugin can allow an attacker to gain access to a remote server and alter it."
Segura alerted Oliver's web admins who appear to have rinsed the dirty site.
He said it was unknown if the attack was pulled off using a compromised plugin used on Oliver's site, or through stolen credentials.
The attack saw recipe-seekers redirected to an exploit kit landing page through a compromised but legitimate WordPress site.
Visitors could be compromised if their machines remained unpatched against at least three vulnerabilities for Flash (CVE-2015-0311), Silverlight (CVE-2013-0074), and Java.
Detection rates for the Dorkbot trojan dropper remained low. At the time of attack two of 57 anti virus platforms detected it as malware.
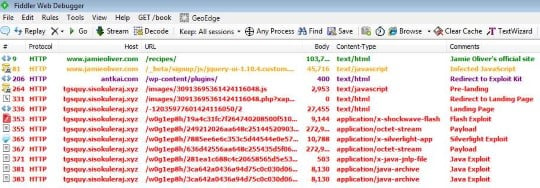
Attackers served the exploit once only and not to those users operating VPNs.
Infected machines would be redirected to dodgy sites serving fake updates for Java and Microsoft Security Essentials.
The attack may have been the most dangerous yet served to Oliver's mockney fans, but it was probably not the most embarrassing (NSFW). ®
