This article is more than 1 year old
'Domain shadowing' hijacks registrar accounts to spawn attack sites
Industrialised hack site creation exploit on the rise
Fiends behind the world's most infamous exploit kit Angler are stealing login credentials to create tens of thousands of pop-up domains used in hit-and-run -style attacks.
The new attacks are dubbed 'Domain Shadowing' and represent the latest evolution of online crime in which scores of web sites are set up to compromise victims before white hat security bods have a chance to act.
Cisco Talos researcher Nick Biasini says the "massive" and ongoing attacks targeting Adobe Flash and Microsoft Silverlight rocketed in December after being used in small sporadic campaigns since 2011. Here's his analysis:
"Domain shadowing using compromised registrant credentials is the most effective, difficult to stop, technique that threat actors have used to date. The accounts are largely random so there is no way to track which domains will be used next.Additionally, the subdomains are very high volume, short lived, and random, with no discernible patterns. This makes blocking increasingly difficult. Finally, it has also hindered research. It has become progressively more difficult to get active samples from an exploit kit landing page that is active for less than an hour. This helps increase the attack window for threat actors since researchers have to increase the level of effort to gather and analyze the samples."
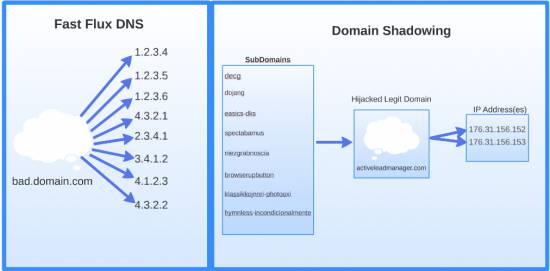
Fast Flux versus Domain Shadowing.
Biasini says the attacks start with phishing emails purported to originate from the targeted registrar and are effective because most people do not regularly monitor domain registrant accounts.
The speed of rotation, a new form of fast-flux, keeps emerging exploits out of the hands of white hat researchers in what Biasini says is the new "productised industrialisation of hacking" previously the realm of advanced targeted attackers.
A third of the 10,000 bogus sub domains were linked to GoDaddy, four times as many as those linked to a second unnamed registrar.
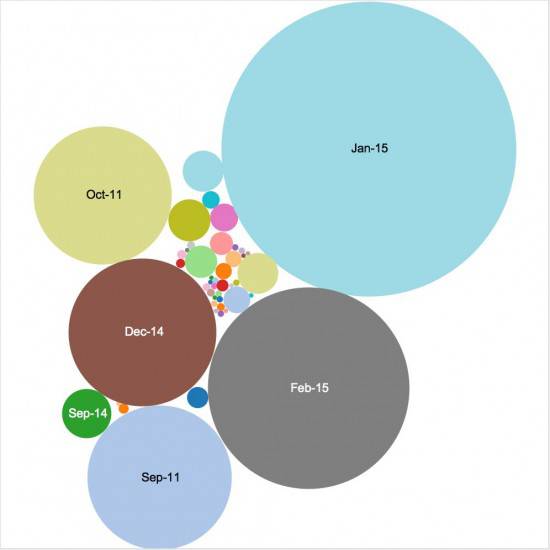
Domain Shadowing attacks on the up.
The first tier of sub domains is generally used to redirect victims to sub-tier landing pages that host the Angler exploit kit. It is used as a kind of scout outnumbering landing pages by a factor of five in its bid to snag users, sometimes through the form of malicious advertisements.
"If a group is going to take the time to create a phishing campaign this would be the registrar to target, and the data Talos has found indicates that is the case," Biasini says.
Most exploits will trip antivirus heuristics and good intrusion prevention systems. ®
