This article is more than 1 year old
Authy 2FA app popped by simple, secret, code
The patch has arrived and the horse has bolted
Attackers could bypass the Authy two factor authentication (2FA) system by typing a phrase in a token field.
Authy's apps make it possible for punters to log in to services like Gmail, Dropbox and Facebook, or even Amazon Web Services, with a one-time password sourced from an app. But prior to the advent of a patch issued 8 February, attackers could type '../sms' into the two factor code field to bypass authentication.
Egor Homakov (@homakov) who reported the flaw overnight says the cause is the default Sinatra dependency rack-protection.
"It turns out even URL encoding was futile - path_traversal module in rack-protection was decoding %2f back to slashes," Homakov says.
"This literally affects every API running Sinatra and reading parameters from the path. This is also a great example how libraries or features that aim to add security actually introduce security vulnerabilities."
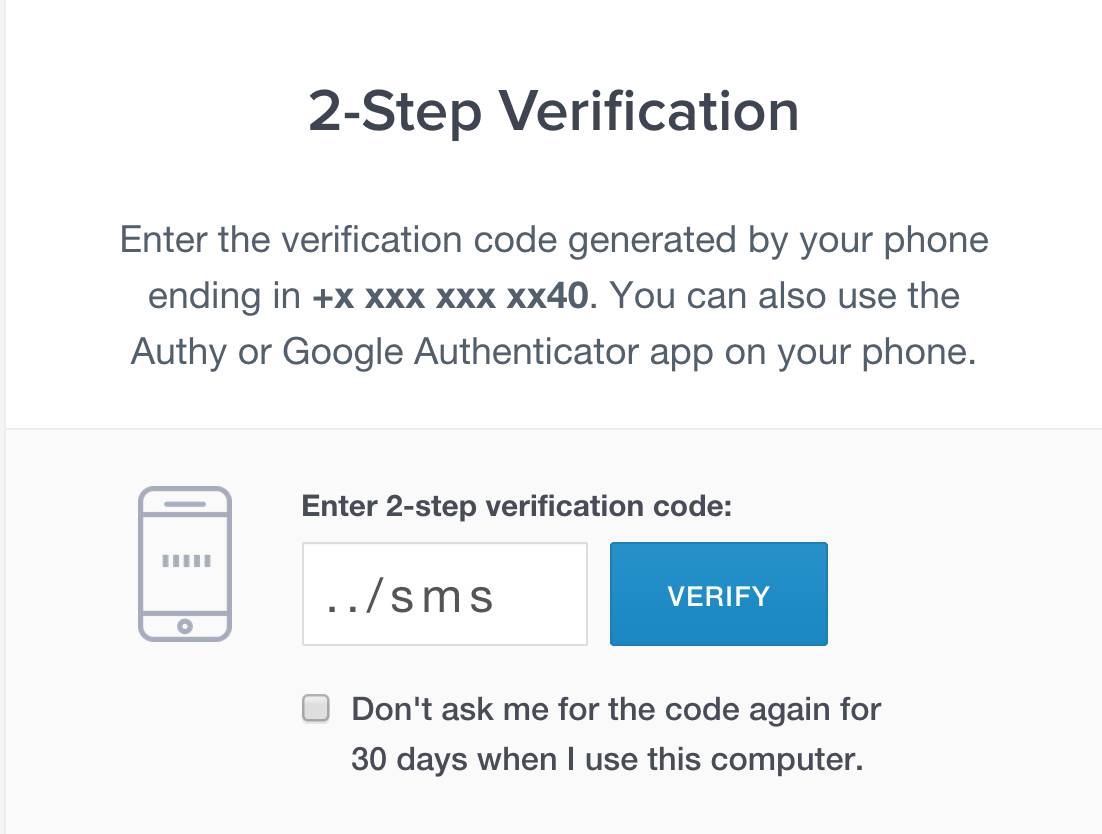
Homakov found multiple flaws affecting Authy-node, and Authy-Python that led to the vulnerability. This included a lack of escaping for slashes introducing directory traversal for '../sms'.
"It introduces path traversal making attacker’s job much easier - you only need to type '../sms' to turn /verify API call into /sms (/verify/../sms/authy_id) which will always return 200 status and will bypass 2FA," he says.
Authy has not yet published details of the vulnerability. ®
