This article is more than 1 year old
China weaponizes its Great Firewall into the GREAT FIRE CANNON, menaces entire globe
You've got censorship – you've all got censorship now
China has upgraded the website-blocking systems on its borders, dubbed The Great Firewall, so it can blast foreign businesses and orgs off the internet.
Researchers from the University of Toronto, the International Computer Science Institute, the University of California Berkeley and Princeton University, have confirmed what we've all suspected: China is hijacking web traffic entering the Middle Kingdom to overpower sites critical of the authoritarian state.
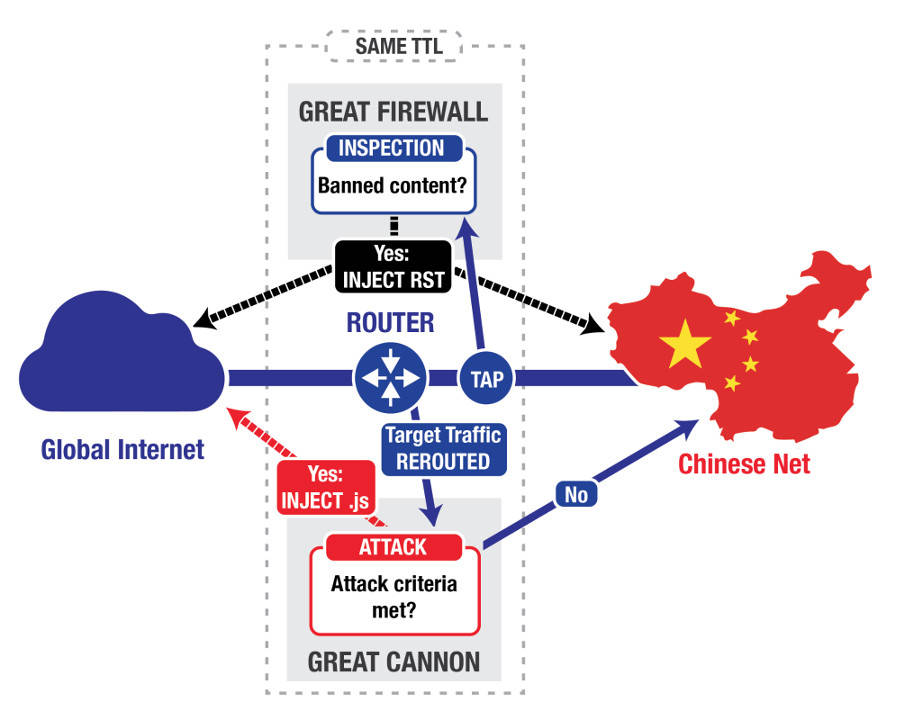
Typically, connections to web servers in the People's Republic must pass through the nation's border routers, which may inject malicious JavaScript into the fetched web pages. This code forces victims' browsers to silently and continuously fire requests at selected targets.
These sites may end up being overwhelmed and crash as a result – a classic denial of service – meaning no one in the world can access them.
It would seem to be a clear case of China engineering a way to knock arbitrary websites off the internet for everyone.
Such an attack was launched last month at California-based GitHub.com, which was hosting two projects that circumvented the Great Firewall's censorship mechanisms, and GreatFire.org, a website dedicated to fighting China's web blocking. GitHub mitigated the assault to mostly stay online.
This weaponized firewall has been dubbed the Great Cannon by the researchers, and typically hijacks requests to Baidu's ad network in China. Anyone visiting a website that serves ads from Baidu, for example, could end up unwittingly silencing a foreign site disliked by the Chinese authorities.
(A technical writeup of the GitHub attack by Robert Graham of ErrataSec can be found here.)
"In the attack on GitHub and GreatFire.org, the Great Cannon intercepted traffic sent to Baidu infrastructure servers that host commonly used analytics, social, or advertising scripts," the university researchers explained in a blog post on Friday.
"If the Great Cannon saw a request for certain JavaScript files on one of these servers, it appeared to probabilistically take one of two actions: it either passed the request onto Baidu’s servers unmolested (roughly 98.25 per cent of the time), or it dropped the request before it reached Baidu and instead sent a malicious script back to the requesting user (roughly 1.75 per cent of the time)."
The researchers note that the Great Cannon and Great Firewall are very similarly structured, with both taking internet traffic either coming in or going out of the country and analyzing it before either passing on or redirecting the traffic.
Unlike the Great Firewall, however, the Great Cannon operates with a very narrow focus, only intercepting traffic to a few specified locations before injecting it with JavaScript code to carry out the distributed denial-of-service attack.
The researchers are also convinced the Chinese government is directly behind the Great Cannon's operations. They note that the Great Cannon and Great Firewall are located in facilities run by state-run Chinese ISPs.
"Deploying the Great Cannon is a major shift in tactics, and has a highly visible impact," they wrote.
"It is likely that this attack, with its potential for political backlash would require the approval of high-level authorities within the Chinese government."
Least we think China is alone in this behavior, the researchers note that Great Cannon actually bears a striking resemblance to another web-injection platform – the QUANTUM tool the NSA and GCHQ have used in the past to attack telco sysadmins and other dangerous types. ®