This article is more than 1 year old
Analogue modems allow UNSTOPPABLE Android attack ... at 13bps
Yes it's slow, but it's enough to leak data to another Android
The better your Android smartphone's audio, the worse its security – the audio channel is the latest path for “low and slow” data leak attacks.
A research group at the Rochester Institute of Technology (RIT) has demonstrated that you could create a covert data channel using a smartphone's voice channel.
While it only runs at 13 bits per second, the researchers reckon that's enough to exfiltrate data (if you're patient), or the channel could be used to spread malware that opens up more attack possibilities.
And, of course, because your average Android security product watches out for suspicious data interactions, the voice-carrying hardware might go completely unnoticed.
What Bushra Aloraini, Daryl Johnson, Bill Stackpole, and Sumita Mishra of the RIT's Golisano College of Computing and Information Science did was create a software modem (remember Winmodem?) that encodes data on the voice stream, but doesn't take up enough of that stream so that the user will notice.
Therein lies the importance of high-quality voice: in an older Android mobe with just a baseband processor (BP) and an application processor (AP), “end users and applications are not able to access the cellular voice stream”.
Newer mobes designed to slake our thirst for high-quality multimedia are different – they have dedicated A/V processors, with the application processor doing audio routing. As the paper states, the “audio path to the cellular voice channel could be reached and controlled from the AP and potentially the end user.”
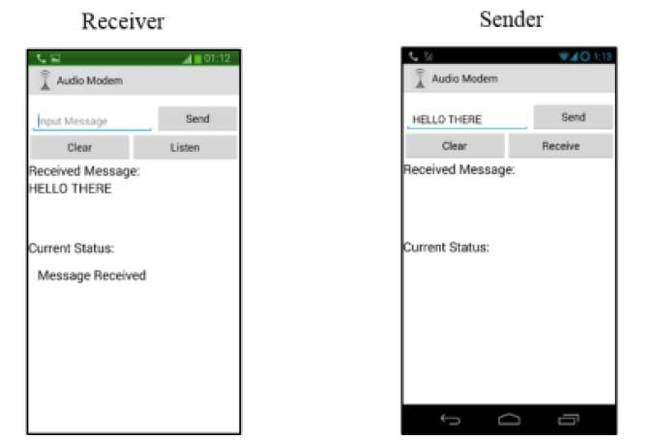
The Android audio modem successfully transmits a message
The researchers' audio modem works just like an old-school dial-up modem, using frequency-shift keying to encode digital states (in their case, Morse code, with 600 Hz representing a dot and 1,000 Hz representing a dash).
The audio modem is accompanied with a rootkit that hides the modem in Android, and gives it continuous privileged access to the system. ®
