This article is more than 1 year old
There's a Moose loose aboot this hoose: Linux worm hijacks Twitter feeds for spam slinging
Mynd you, møøse bites Kan be pretty nasti
ESET researchers Olivier Bilodeau and Thomas Dupuy have found malware capable of compromising routers and embedded devices, seizing control of social networking accounts, and booting out competitors.
The duo report the Moose malware exploits weak login credentials in the networking gear, and does not require vulnerabilities to be exploited. Nor does it contain a feature for persistence or creating backdoors.
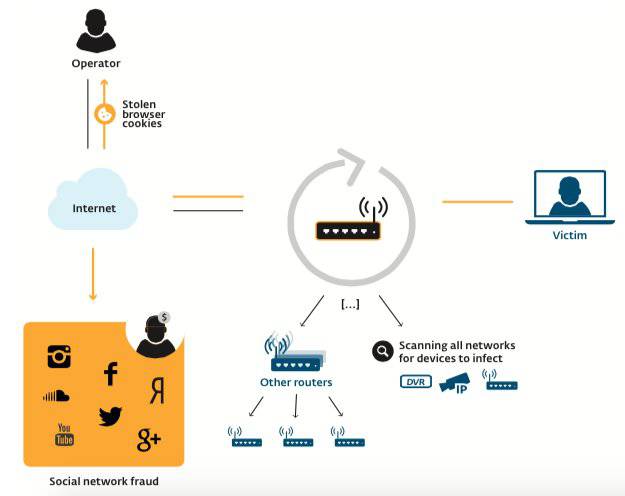
But it has infected large numbers of routers and embedded gadgets, intercepts and steals web cookies, and hijacks social media accounts to turn them into spam bots.
"During our analysis we often asked ourselves, 'Why so much effort in order to interact with social networks?' But of course there is a market for follows, likes, views and whatnot," the researchers said in a white paper [PDF].
"The operators of this botnet are generating revenue by performing social network fraud. The consumer routers under attack provide a means to proxy malicious traffic from the operators through to the social network sites leveraging highly reputable Internet Service Providers’ (ISPs) IP addresses."
Olivier Bilodeau, a malware researcher at ESET, told El Reg security correspondent John Leyden that Moose was unrelated to these other recent attacks.
“The Linux/Moose threat is unrelated to the two threats mentioned in the links below. It is a new threat documented for the first time by us. It is different to the DDoS router worm, bitcoin miners worm and DNS changers," Bilodeau explained. "In fact, it is not interested in performing such attacks. Instead, it steals consumer network traffic and leverages the good IP reputation and bandwidth of consumers to perform social network fraud. I am not aware of any other router threat being operated that way.”
Security firm Rapid 7 ran internet scans using indicators of compromise and finds about 50,000 routers are infected by the man-in-the-middle malware.
Bilodeu and Dupuy compare the traffic on port 10073 to normal HTTPS traffic as logged by the SANS Internet Storms Center and find similarly large infection rates.
"In themselves the numbers might paint an incomplete picture, since the probes are seeing just a subset of the internet traffic — but if we compare them with HTTPS traffic over the same period, we see that Moose activity was roughly only an order of magnitude below HTTPS," Bilodeau and Dupuy report.
"Over 24 hours, almost 170,000 connection attempts were made on port 10073, meant for 23000 unique hosts.
"Of those, 36 completed the TCP handshake, which means that they might be infected, or they have another service on this port, or they are firewalled weirdly."
The duo says some 85,000 Telnet connection attempts were made on 18,000 unique hosts, of which 161 responded with a login banner. Those simulated statistics are comparable to actual router infection, they say.
Some 49 percent of Moose attack traffic related to compromised Twitter accounts, 47 percent for Instagram, and 3 percent related to Yandex, Amazon, and YouTube.
Moose could destroy rival malware running on MIPS and ARM devices in a bid to preserve scant available resources.
Vulnerable devices are those running the popular μClibc C library including Actiontec; Hik Vision; Netgear; Synology; TP-Link; ZyXEL, and Zhone. The researchers note that it's possible that medical devices could fall victim, and they highlight the Hospira Drug Infusion Pump as vulnerable.
The pair said Moose spreads to near IP range devices exploiting the likelihood that a network may have more than one misconfigured firewall and router.
"Considering the rudimentary techniques used by Moose in order to gain access to other devices, it is unfortunate that the security of embedded devices isn’t taken more seriously by vendors," the researchers note. ®
