This article is more than 1 year old
Vegan eats BeEf, gets hooked
Bad taste still lingers
Botnet slaughterer Brian Wallace has created a module to detect when attackers are using the popular browser-busting BeEF hacking framework.
The Chrome extension codenamed Vegan allows victims to detect when attackers have hooked their web browser instances using the enormously powerful Browser Exploit Framework.
Vegan could detect and block BeEF but not entirely stop it, Wallace (@botnet_hunter) says.
"In order for BeEF to gain control over a browser, the browser must be tricked to execute malicious JavaScript code [which] can happen on any website that the attacker can control, or even in malicious advertisements, and tends to occur transparently to the affected user," Wallace says.
"I decided to build my protection (Vegan) into Chrome browser so I could easily deploy it to devices regardless of the OS, handle HTTPS seamlessly with HTTP and approach the problem from the chokepoint.
"While a detection method is important, it really only tells the user they are now at the will of the attacker, and there is not much the victim can do." Victim machines that run the malicious JavaScript will connect to BeEF's control panel allowing hackers to execute highly-capable attacks and gather further user information.
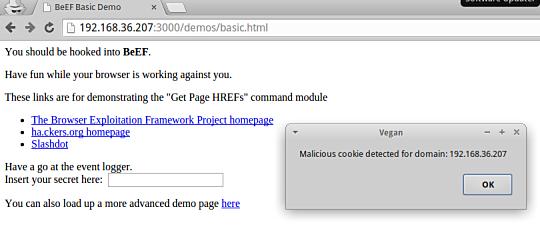
Vegan in action.
Wallace says the alternative to Vegan is messy, complicated, and unreliable. Targets could configure their Snort intrusion detection systems to look for the BEEFHOOK cookie which may signal a BeEf attack, but that method could be subverted if attackers modify those values or simply employ HTTPS.
Wade Alcorn, BeEF creator and director of Brisbane-based Alcorn Group, welcomes the extension saying it is valuable for raising awareness.
"It is an awesome name," Alcorn says.
"Almost a decade ago, I started the BeEF project to provide a method to raise awareness of client-side attack vectors and to create a tool to evaluate an organisation's security posture.
"I am hopeful the Vegan extension will provide another opportunity to increase education among those responsible for their organisation's security."
I'd like make it very clear, I'm a fan of @beefproject but I want to ensure I know if I get hooked. re: http://t.co/h4o4clbk3M
— bwall: Brian Wallace (@botnet_hunter) June 25, 2015
Alcorn says the security community has a way to go before such threats are sufficiently mitigated.
"It is a positive sign to see the awareness of client-side risks is increasing." ®
