This article is more than 1 year old
Chinese gang shoots down aerospace security with MSFT flaws
'Panda Emissary' group has an appetite for defence projects
Black Hat 2015 An alleged Chinese advanced hacking group has been found cherry-picking data from high-profile governments and corporations, p0wning many within six hours according to Dell researchers.
The group, codenamed TG-3390 or Panda Emissary, is thought to operate from China and have an appetite for defence-related aerospace projects.
Its techniques mean domain credentials and multiple systems are compromised with six hours of gaining access to an environment.
Watering holes are the group's attack vector of choice, as it likes to compromise websites popular with a target organisation's staff. Doing so gives the gang a beachhead into the target's network.
To date it has popped about 100 sites. Each of these watering holes employs a whitelist to ensure that only staff from a target organisation are attacked in a move that helps maintain stealth.
Researchers say the group, revealed at Black Hat 2015 in Las Vegas this week, is notable in its small-scale data exfiltration and use of custom Microsoft Exchange backdoors.
"The group extensively uses long-running [watering holes], and relies on whitelists to deliver payloads to select victims," Dell's counter-threat unit says .
"After the initial compromise, TG-3390 delivers the HttpBrowser backdoor to its victims. The threat actors then move quickly to compromise Microsoft Exchange servers and to gain complete control of the target environment.
"The threat actors are adept at identifying key data stores and selectively exfiltrating all of the high-value information associated with their goal."
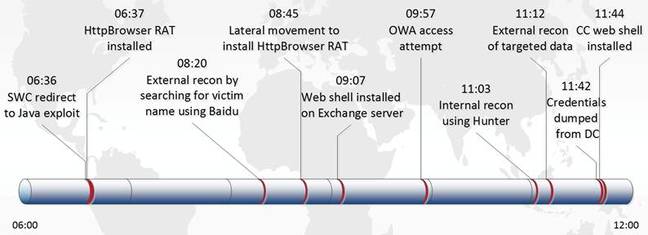
Six hours to p0wnage.
Researchers say they information plucked from targets is specific to projects, and rather than a wholesale en-masse exfiltration, which shores up the argument that the group is hacking for specialist interests.
"CTU researchers have observed the threat group obtaining information about specific U.S. defense projects that would be desirable to those operating within a country with a manufacturing base, an interest in U.S. military capability, or both," they say.
Dell did not go as far as to say the group are a hacking-for-hire outfit, however.
They add that other organisations targeted include Middle East, Europe, and Asia embassies based in Washington DC, non-governmental organisations, and government agencies. The outfit exploits old vulnerabilities not yet patched by victims, with Java (CVE-2011-3544, CVE-2010-0738) a favourite, and makes use of DLL side-loading.
It also has access to a criminal development team focused on building hacking tools and is proficient at hiding malware and does not bother with reconnaissance, instead waiting to gain a foothold in target organisations.
"The adversary's end goal is to exfiltrate, not infiltrate. After gaining access to a target network in one intrusion analysed by CTU researchers, TG-3390 actors identified and exfiltrated data for specific projects run by the target organisation."
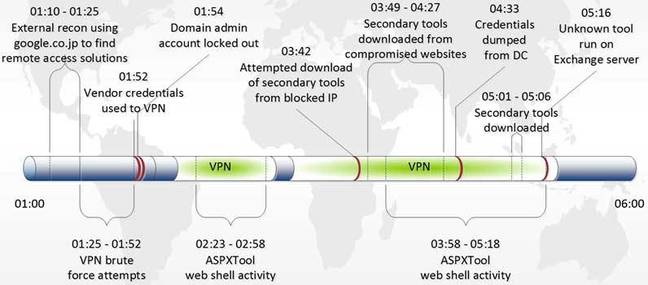
Five hours to regain access.
Researchers observed the group after being punted from a network attempting to re-gain access through its backdoors and failing that targeting insecure remote access portals.
Given the perils of attribution, Dell acknowledges the group's suspected Chinese origin which includes local working hours, and use of native language tools, could be an elaborate false-flag operation.
Tools used include custom tools OwaAuth web shell and ASPXTool, and popular criminal hacking tools PlugX, HttpBrowser, and ChinaChopper.
Terrified enterprises should use two factor authentication for all remote access, search for logs and particular user agent strings. ®
