This article is more than 1 year old
A close shave: How to destroy your hard drives without burning down the data centre
Thermite, kinetic shock and power surges tested
DEF CON 23 Four years ago at DEF CON a popular presentation examined how best to destroy hard drives in a data centre within 60 seconds of a three-letter agency knocking at the door. Now, that research has been updated with new techniques.
Security researcher Zoz looked at three core methods for destroying platter and SSD drives – thermal, explosive and electric – within a simulated 1U frame. A successful technique would have to make the drives unreadable, not damage other data centre equipment and not threaten human life.
It turns out that this is surprisingly difficult to achieve.
Thermite was the first test material and Zoz unscrewed a standard Seagate platter drive, filled the inside with a bag containing 15 grams of thermite (stuffed into the side so the drive would still operate) and rigged one of the bus pins as an igniter.
The results were rather poor. While one section of the top platter was significantly damaged, the data on the disk, and the two platters underneath it, could conceivably be read. Placing the thermite on top of the drive was also tried, but the outcome for that method was even worse.
So Zoz and his compatriots tried thermate, which is chemically similar to thermite but adds barium nitrate to increase temperatures. The resulting pyrotechnics were impressive, but again the drives could be cleaned off and potentially read.

Thermate, like thermite, proved a little disappointing
Next up he tried a plasma cutter mounted above the platter. This worked well at burning through the Seagate casing, but once it began cutting the disks the platters froze in place and the cutter just left a hole in one sector of the drive.
He then tried kinetic destruction, using a nail gun powered by the propellant from a .22 bullet. This punched a nail right through the drive and he suggested that these could be positioned above the drive and fire multiple nails to destroy all the platters.
A pneumatic press worked satisfactorily as well, with the added bonus of pressure welding some of the platters together. But Zoz found this solution rather boring and moved on to explosives.
With the help of some advanced chemistry skills, and the support of a friendly local bomb squad, Zoz mixed together a two-part explosive he dubbed FELIX. Then it was a question of working out the most effective means to deploy it.
He opted for a 3D-printed shaped charge. By cutting a cone or groove in the explosive the energy of the blast can be directed and so he printed a cup of explosives over the drive.
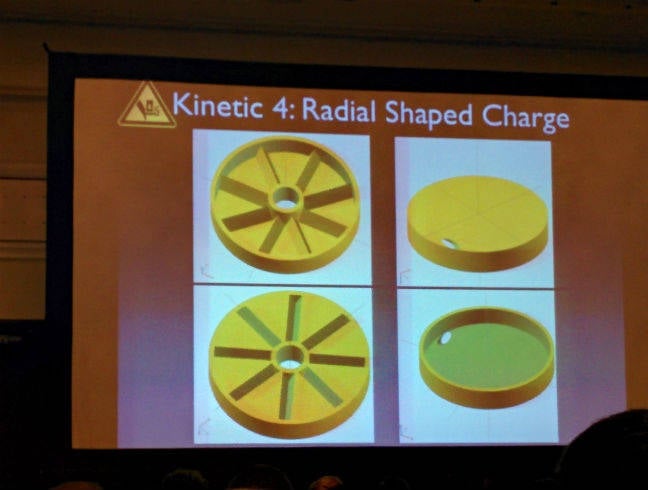
It's all down to getting the right shape, apparently
The results were somewhat discouraging: the platters suffered significant damage but weren't totally unreadable. So he built another shaped charge, with six spokes to punch through the platters and upped the amount of explosives, which worked a treat.
The bomb squad also gave him a couple of shaped charges that would normally be used to blast out the side of oil wells. While these punched through the drive's platters admirably, they also went through the quarter inch steel plate the drive was resting on and pummelled another 15 inches into the ground.
Clearly this technique wouldn't work in a data centre, so he looked for a material to pack around the 1U rack to absorb some of the force of the explosion. The material should be capable of containing a blast, easily deployable and preferably cheap.
The material in question was one the bomb squad used themselves while blowing out locks – shaving foam. The foam showed a considerable dampening effect but it was still going to be too much for a data centre.

Amazing what a couple of cans of shaving foam will do (left) compared to a raw explosion (right)
Zoz tried varying the amount of explosives, eventually settling on 100 grain detonation cord coiled up and placed over the platters on top of the casing. This not only destroyed the casing but also pressure welded the platters together, making them unreadable, but again containment of the blast remained an issue.
Finally, Zoz and his team turned to electricity.
This technique isn't much use against platter drives but could be handy against solid-state drives. He used a flash drive for testing, since SSDs are very expensive, and managed to snap the chip in half with a high-voltage surge.
The conclusion? None of the techniques were perfect, although it's clear that the testing team had a lot of fun.
But to be absolutely sure your drive will never be read, there's only one solution that really works – degauss and shred the platters and dispose of them in multiple locations. ®
