This article is more than 1 year old
Now Ashley Madison hackers reveal 'CEO's emails and source code'
Meanwhile, IBM, Cisco and HP lead the IT pack on adultery website, it seems
Updated Another load of internal files swiped by hackers from Ashley Madison have been leaked online – and they apparently feature the CEO's emails and the website's source code.
The 18.5GB leak includes, it is claimed, archives of internal company emails, including one folder labeled Noel Biderman – the chief exec of Avid Life Media, Ashley Madison's parent.
Given the size of the file and the relatively small number of people seeding it over file-sharing networks, it will be some time before it can be downloaded and its veracity ascertained. Several people who have tried to fetch the cache warned some of the compressed data is corrupted.
A torrent of the archive was published on the website of Impact Team, the Ashley Madison hackers. "Hey Noel, you can admit it's real now," the gang said in a message announcing the second archive.
On Tuesday, the group released a 9.6GB collection of user databases containing profiles, email addresses, fantasies, sexual preferences, etc, of as many as 36 million people who used Ashley Madison, a Tinder-for-adulterers website, and its sister site Established Men, which was set up for women to find sugar daddies. Other information, including some users' GPS coordinates, post codes and ZIP codes, dates of birth, hashed passwords, and partial credit card numbers, was also included.
Just over 24 million accounts have valid email addresses, while 12 million do not, according to people who have crunched through the data – the Ashley Madison site does not verify accounts' email addresses, so a lot of them are bogus.
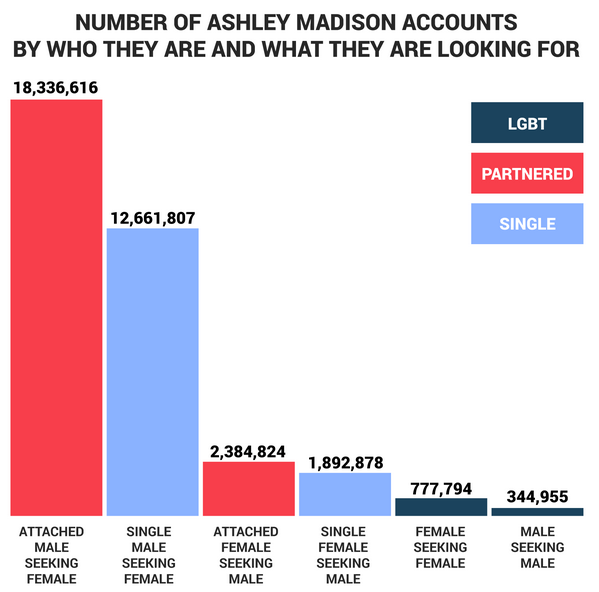
Some 31 million accounts say they are men, and 5 million say they are women. One in four say they are single, so not everyone was using the site to cheat on a partner or spouse. Some were using the site to set up a threesome with their wife or husband.
The leaked account databases, examined by The Register, look legitimate, which would suggest that the new archive is also kosher. It looks as though the Impact Team had enough time and opportunity to thoroughly plunder the Avid Life Media servers and collect as much data as they wanted.
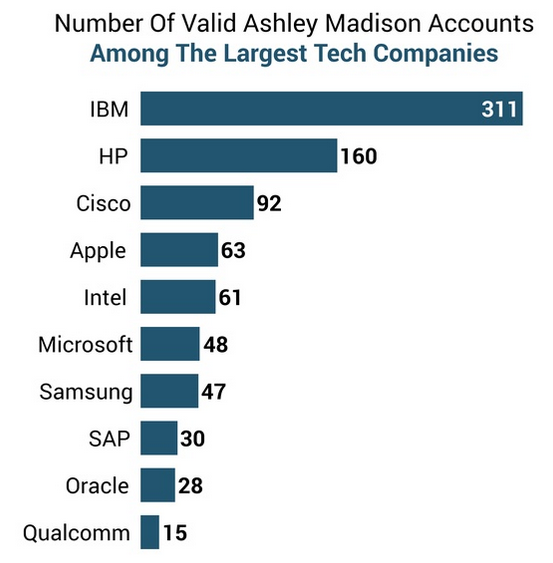
Unbelievably, it appears about 100 people used .gov.uk and .police.uk email accounts to sign up for Ashley Madison accounts. Thousands more used .gov and .mil addresses in the US, and it appears hundreds used work accounts at tech giants.
Releasing the profile records was a major blow for privacy – and for the art of seduction. The vast majority of profiles read like a teen's first attempt at writing erotica ("What i'm looking for is a woman with a hypnotizing touch. a soft body. she makes me feel like i'm having an asthma attack cause she just takes my breath away") to the downright tragic ("My real downfall though is that I left right after high school so no car, yet, and also I don't have a house of my own so I have a problem there but I hope you don't mind.")
"it is my belief that 'what goes around comes around'" writes one person on their Ashley Madison profile page, now leaked online.
— Chris Williams (@diodesign) August 19, 2015
Assuming the new folders do contain company emails, this latest leak could be even more damaging for Avid Life Media than the first document dump – especially if, as the TrustedSec blog notes, other miscreants find vulnerabilities in the leaked code and exploit them to infiltrate the web biz.
But, as we've seen in the case of the Sony hack, The Hacking Team takedown, and Anonymous' attack against HB Gary Federal, internal company emails can be very damaging to a company's reputation. People writing internal emails often say things they wouldn't be caught dead uttering in public and there are all kinds of juicy nuggets that are let slip.
Avid Life Media said the company had no statement on the matter at this time. We'll add updates as they come in. ®
Updated to add
Avid Life Media has had a change of heart, and given us this statement:
We are aware of the reports that criminals have stolen proprietary company files from Avid Life Media (ALM) and are disseminating them online. We are working with law enforcement, including the U.S. Federal Bureau of Investigation (FBI), the Royal Canadian Mounted Police (RCMP), the Ontario Provincial Police (OPP), and the Toronto Police Services (TPS) to determine who is behind this criminal activity.
Regardless of the nature of the content, our customers, this company, and its employees are all exercising their legal and individual rights, and all deserve the ability to do so unhindered by outside interference, vigilantism, selective moralizing and judgment. The individual or individuals who are responsible for this straightforward case of theft should be held accountable to the fullest extent of international law.