This article is more than 1 year old
Even 'super hackers' leave entries in logs, so prepare to drown in data
The 1990s called. It wants its breach classification system back
Gartner: Super hackers basically don't exist, your incident response plan sucks, and you should relish the opportunity to drown in data: such are the lessons from incident response fanatic Anton Chuvakin.
The analyst, physicist, and former director of Security Warrior Consulting gave delegates of the Gartner Security and Risk Management Conference in Sydney today a sermon on the dos-and-don'ts of security incidence response.
The Garner Vice President™ says the old school incident response model security bods are taught as tots is ineffective but sadly popular. He says while "super hackers" exist, they aren't ghosts and everyone leaves logs.
"Super hackers practically do not exist," Chuvakin says. "They always leave trace."
"You should deploy more visibility tools; it's likely you don't have enough, even if you think you are drowning in data.
"Many think the win is not about being secure, but is about stopping the attackers. And that mindset makes it difficult to do advanced incident response."
The respected security bod gave something of a condensed interpretation of his incidence response blogs. In it, Chuvakin says that the classification of a security incident is a personal affair that each organisation needs to determine according to their risk appetites. But the urge to classify a response according to monetary impact should probably be left off the agenda.
"Monetary cost is a question that should have been left in the 1990s," Chuvakin says.
His sermon continues: having a plan is a vastly different beast to actual planning, the latter requiring constant updates such that threat vectors, disaster recovery phone contacts and so on are relevant when the corporate network locks are popped. "Finding the right people to call during an event rarely works well," he says.
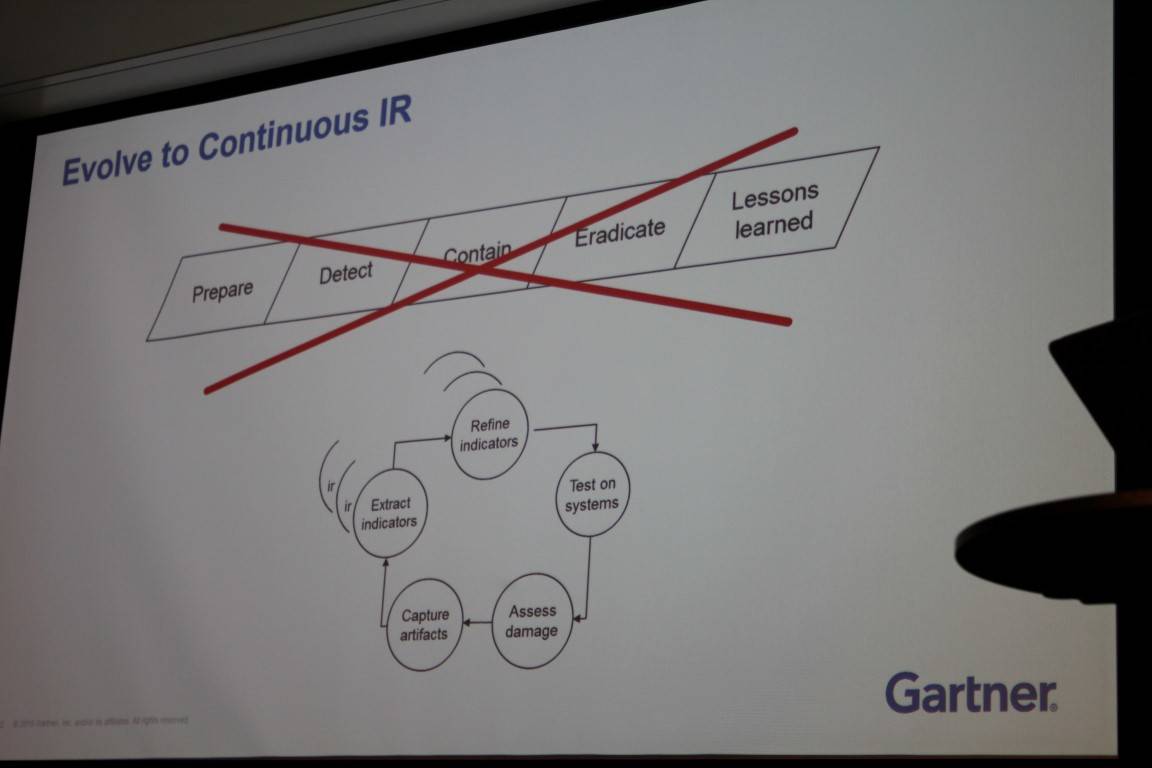
He describes continuous incidence response as the mark of a modern security boffin whereby the corporate network is considered breached such that the battle is a daily occurrence of keeping the enemy pinned down on its beachhead.
Chuvakin paints a red cross through the old-school response flow process of prepare, detect, contain, and eradicate, but says it should not be entirely consigned to the incidence response recycling bin.
The method rather needs updating to focus on indicators of compromise and to have dedicated teams charged with handling separate and dedicated areas of a response process, the boffin says. ®