This article is more than 1 year old
It's BACK – Stagefright 2.0: Zillions of Android gadgets can be hijacked by MP3s, movie files
Pop tunes pop phones
Updated More than a billion Android phones, tablets and other gadgets can be hijacked by merely previewing MP3 music or MP4 video files.
Booby-trapped songs and vids downloaded from the web or emails can potentially compromise vulnerable devices, and install spyware, password-stealing malware, and so on.
This is all thanks to two remote-code execution flaws billed as the second iteration of the original Stagefright vulnerability.
Zimperium researcher Joshua J Drake found the pair of Android security bugs (CVE-2015-3876 in libstagefright, and CVE-2015-6602 in libutils), and reported them to Google. We're told they will be patched in an upcoming over-the-air update to people. The flaws are present in all versions of Android in use.
There's more bad news – we're told Google has already pushed out a fix for the most critical hole to the latest Android phones. This means criminals could well be studying the changes to cook up malware-laden MP3s to infect devices that cannot be patched, or get their patches late.
"The first, and most critical issue, was pushed to AOSP nearly immediately despite an embargo," Zimperium told Vulture South.
"Good guys and bad guys alike scour open source projects to find recently patched security issues – patching an open source software project without providing an update puts users at risk, if even only for a matter of weeks."
Thanks to the fragmented state of Android – patches have to be slowly fed from Google to hardware manufacturers and out to people via mobile carriers – just half of all affected users, and possibly far fewer, stand any hope of receiving a fix.
Without the patch, phones and other gadgets running Android can be potentially hijacked and wrecked by software nasties hidden in MP3 or MP4 files.
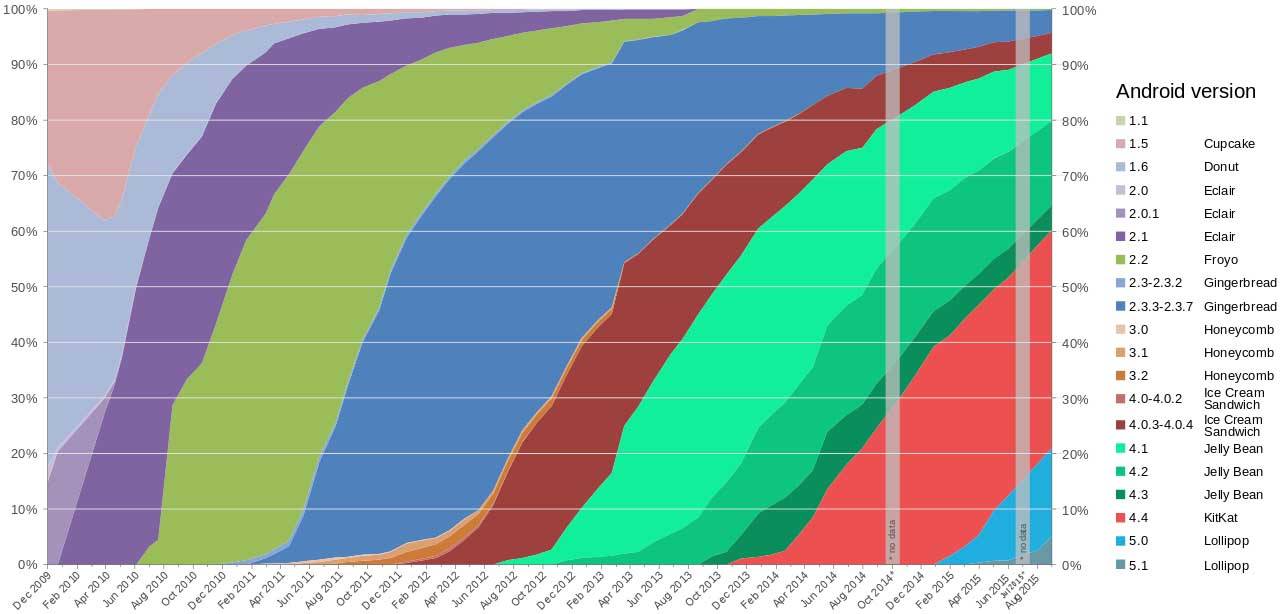
Zimperium hacker Zuk Avraham said the 40 per cent of Android users on version 4.4, aka KitKat, may receive patches along with the 20 per cent running the version 5, aka Lollipop, since Google slung out patches in this way when it fixed the first first Stagefright hole (CVE-2015-1538) in July.
"While we have no specific information about what devices will receive fixes, we believe Android devices running Android KitKat 4.4 and later will receive updates," Avraham said.
"However, since Android 6 is due to release next week as well, it's possible that only 5.0 and 6.0 devices will receive updates."
Google was not immediately available for comment.
That reasoning suggests a best-case scenario where 40 per cent of users running rather old Android phones are unpatched, and a worst case where somewhere around 70 or 80 per cent are unpatched, depending on uptake of Android 6.
Déjà vu
Stagefright 2.0 vulnerabilities are triggered when specially crafted MP3 audio or MP4 video files are scanned by software within Android. These files can be downloaded from the web, or from phishing emails, and allow arbitrary code smuggled within the media to execute.
The Zimperium guys have produced roof-of-concept exploit code, but will only share it with some customers.
Google was notified of the flaws on 15 August.
New Android phones running Lollipop or later will be instantly hosed by any music or videos exploiting the vulnerable Stagefright library, the researchers said. People owning the 20 per cent of devices running Lollipop or later are probably wealthier than others, and therefore more attractive targets.
While most users run KitKat, about 30 per cent sport Jelly Bean versions 4.1 to 4.3.1. Those latter luddites can still be hosed through malware that taps Android's libutils.
The first Stagefright hole revealed in July demonstrated how remote code execution could be obtained in a similar way by sending a poisoned MMS. It required no user interaction for users on Google Hangouts. ®
Updated to add
Google has been in touch to say the bugs will be patched in this month's batch of security fixes for Android, due out this Monday. People installing Android by hand from ASOP, and Nexus owners, will get the update from October 5. Everyone else will have to wait for their hardware maker and carrier to issue the patches, if at all.
The web giant is also not aware of anyone exploiting the flaws – but that will change as malware writers study the open-source patches, we reckon.