This article is more than 1 year old
How TV ads silently ping commands to phones: Sneaky SilverPush code reverse-engineered
Near-ultrasonic sound system drives pets, and users, crazy
Earlier this week the Center for Democracy and Technology (CDT) warned that an Indian firm called SilverPush has technology that allows adverts to ping inaudible commands to smartphones and tablets.
Now someone has reverse-engineered the code and published it for everyone to check.
SilverPush's software kit can be baked into apps, and is designed to pick up near-ultrasonic sounds embedded in, say, a TV, radio or web browser advert. These signals, in the range of 18kHz to 19.95kHz, are too high pitched for most humans to hear, but can be decoded by software.
An application that uses SilverPush's code can pick up these messages from the phone or tablet's builtin microphone, and be directed to send information such as the handheld's IMEI number, location, operating system version, and potentially the identity of the owner, to the application's backend servers.
Imagine sitting in front of the telly with your smartphone nearby. An advert comes on during the show you're watching, and it has a SilverPush ultrasonic message embedded in it. This is picked up by an app on your mobile, which pings a media network with information about you, and could even display followup ads and links on your handheld.
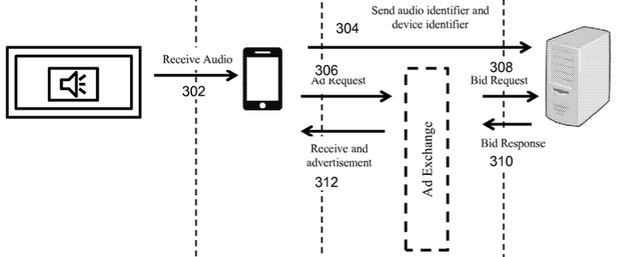
How it works ... the transfer of sound-encoded information from a TV to a phone to a backend server
"This kind of technology is fundamentally surreptitious in that it doesn't require consent; if it did require it then the number of users would drop," Joe Hall, chief technologist at CDT told The Register on Thursday. "It lacks the ability to have consumers say that they don't want this and not be associated by the software."
Hall pointed out that very few of the applications that include the SilverPush SDK tell users about it, so there was no informed consent. This makes such software technically illegal in Europe and possibly in the US.
There are similar systems in use already. Ratings agency Nielsen has an audio system that does just this to measure the size of radio station audiences, but it's something people have to agree to use and get paid to do so.
In addition, this sort of thing doesn't just need to be used for advertising. What if a repressive regime decided to use it to track the phones of dissidents, he posited.
Of course, none of this matters if you don't have an app listening out for the sounds of SilverPush. But initial research found almost 30 applications using the SilverPush SDK, predominantly shopping apps run by Indian or Far Eastern firms.
As the news about SilverPush spread, Kevin Finisterre of security consultancy Digital Munition decided to take a look at the code. He has since published his findings on GitHub.
He found that the software assigned letters of the alphabet to high-pitch tones, eg: an 18kHz sound translates into an 'A', and 19.125kHz is a 'P'. Pairs of these characters are used to identify TV ads: 'AP' is used to recognize a Geico ad and display an image and link to the insurance biz, we're told. Sound-playing online adverts appear to use a fingerprint of five characters.
The logical next step is to see if these signals can be disrupted. Finisterre played around with trying to spoof the sounds the apps are looking for and send them junk data. It would also be possible to write a program that randomly sent out ultrasonic tones to disrupt the system, although this would "probably piss your dog and a bunch of other animals off," he told The Reg.
"I would try to block this at the audio driver level, not at the browser level. Any other app can implement the same type of tech," he said.
"There are lots of possibilities. It really depends on which aspect of it you are trying to protect against. The audible beacon triggers themselves (audio driver-based protections, spoofing tones, etc), or the data collection process (think blocking the IPs of the servers), or the monetization of the data collection (think spoofing randomized invalid data at the backend)." ®
