This article is more than 1 year old
World's most complex cash register malware plunders millions in US
'ModPos' kernel monster threatens haul during festive shopping blitz
The world's most complex sales till malware has been discovered ... after it ripped millions of bank cards from US retailers on the eve of post-Thanksgiving shopping frenzies.
The ModPOS malware has pilfered "multiple millions" of debit and credit cards from the unnamed but large retail companies incurring millions of dollars in damages.
The attackers have operated in a low-key, ultra professional manner since late 2013 and has only come to light after weeks of painstaking reverse-engineering efforts by malware experts.
They have kept mum, too. Cybercrime forums are entirely devoid of references to the malware.
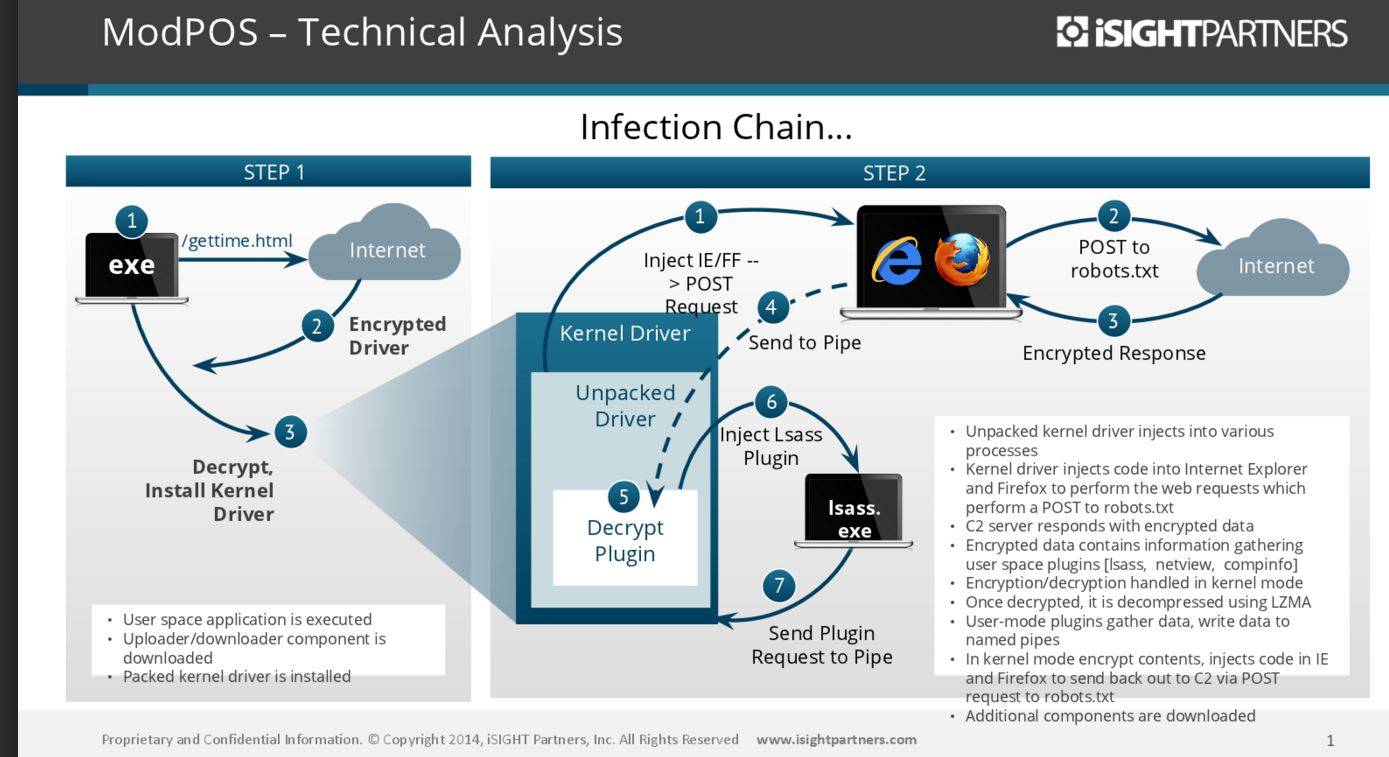
"This is POS [point-of-sale] malware on steroids," iSight Partners senior director Steve Ward says. "We have been examining POS malware forever, for at least the last eight years and we have never seen the level of sophistication in terms of development …[engineers say] it is the most sophisticated framework they have ever put their hands on."
Ward says his team took three weeks to debride one of ModPOS' three kernel modules. By contrast it took the same experts 30 minutes to reverse engineer the Cherry Picker POS malware revealed last week.
The "incredibly talented" authors have done an "amazing job" and have such an understanding of security that the work has impressed the white hat engineers.
"It is hard not to be impressed," Ward says.
He says the criminals have spent a "tonne" of time and money on each packed kernel-driver module which behaving like a rootkit is as difficult to detect as it is to reverse.
That approach to the 0module build is novel.
The anti-forensics componentry is highly-sophisticated, meaning most businesses that the advanced Eastern European attackers have popped will not know the cause of the attack.
It is clearly a tool targeted designed for large-scale revenue generation and return on investment.
Ward and his colleagues have briefed more than 80 major retailers across the US, all of which are on high alert for infection.
He says the attack group will need to change parts of its codebase to re-gain some of its now lost obfuscation, but adds that some changes will be much harder to implement than others.
The encryption used for network and command and control data exfiltration and communication is protected with 128 bit and 256 bit encryption, with the latter requiring a new private key for each customer.
This makes it much more difficult to know what data is being stolen, unlike other sales register malware that slurp details in cleartext.
"We will see disclosures and compromises in the future that point back to this framework." ®