This article is more than 1 year old
Ad-clicking bots predicted to rip US$7.2 billion from Mad Men
Could it be bots that fall for for those 'One Weird Trick' ads? Here's hoping!
Botnets will inflict a massive US$7.2 billion in damages against online advertisers this year according to research by ad security company White Ops.
Last year the industry was said to have lost US$5 billion, close to the $6.3 billion White Ops predicted in December 2014, thanks to the scourge of botnets that hugely inflate the number of online ad clicks.
The average loss was US$10 million per advertiser with the hardest-hit haemorrhaging a staggering US$42 million.
That earns scammers loads of cash and even more this year, according to the 2015 Bot Baseline: fraud in digital advertising [PDF]
The work is a joint effort with the Association of National Advertisers in which 49 ad companies tagged their online content in August through to September to allow researchers to tell how many bots were clicking ads.
Brands include Playstation, Ford, Unilever, Dell, IBM, and McDonalds among other giants. The amounts lost are not attributed to individual companies.
About nine percent were fake, the researchers say, equating to $10 million in lost revenue per advertiser.
One publisher’s impression volume rose by six percent thanks to bots.
Some advertisers stand to lose tens of millions of dollars this year if they do not move to lock out bots, the report says.
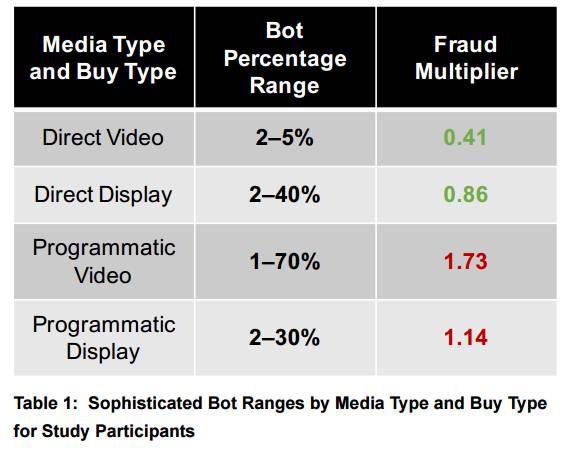
The New York company co-founded by respected security man Dan Kaminsky notes in its report that most bots fleeced programmatic advertising, with a majority hitting more lucrative programmatic video ads.
Publishers buying expensive pay-per-click traffic are the best earners for fraudsters with fresh, undetected bots, while mass clicking low-end ad-men who do next-to-nothing to purge bots are the criminal's last resort.
Advertising fraud botnets remain lucrative for longer than many criminal enterprises, provided new machines can be infected.
Chief executive officer Michael Tiffany says scammers that keep their bots fresh earn the highest revenue.
"Bot operations, then, have a profit window, a period of time from when a computer has been freshly infected until the bot is so widely detected that no one will pay for its impressions anymore," Tiffany says.
"Infections at the leading edge of the profit window, those that are fresh, affect high-CPM (cost per mile) advertising buys.
"Because most systems will not determine that the just-infected machines are now sending non-human traffic, high-CPM direct buys, programmatic private marketplace deals, and buys on top-tier platforms are all affected."
The fraud traffic while resulting from compromised computers can look almost legitimate, Kaminsky says.
"Advertising fraud has the curious status of almost seeming legitimate — you couldn’t expect to get away with raiding a bank account or accessing someone else’s Gmail account, but defrauding advertisers, even by using the host user’s identifying cookies, doesn’t seem nearly as criminal," Kaminsky says.
"While the ecosystem suffers, the end user sees very little impact from the fraud."
The impact to fraud operators is huge, however, and stands only to rise. ®
