This article is more than 1 year old
Comodo's 'security' kit installed a lame VNC server on PCs on the sly
Modern antivirus: Easily crackable password, lets malware gain admin privileges
Google's Project Zero has found yet another blunder in Comodo's internet "security" software – a VNC server enabled by default with a predictable password.
Earlier this month, Googler Tavis Ormandy pointed out that Comodo's custom web browser, dubbed Chromodo, was about as unsafe as a lace condom thanks to terrible security settings. Now Ormandy has found Comodo's software included a remote desktop tool that is ideal for hackers.
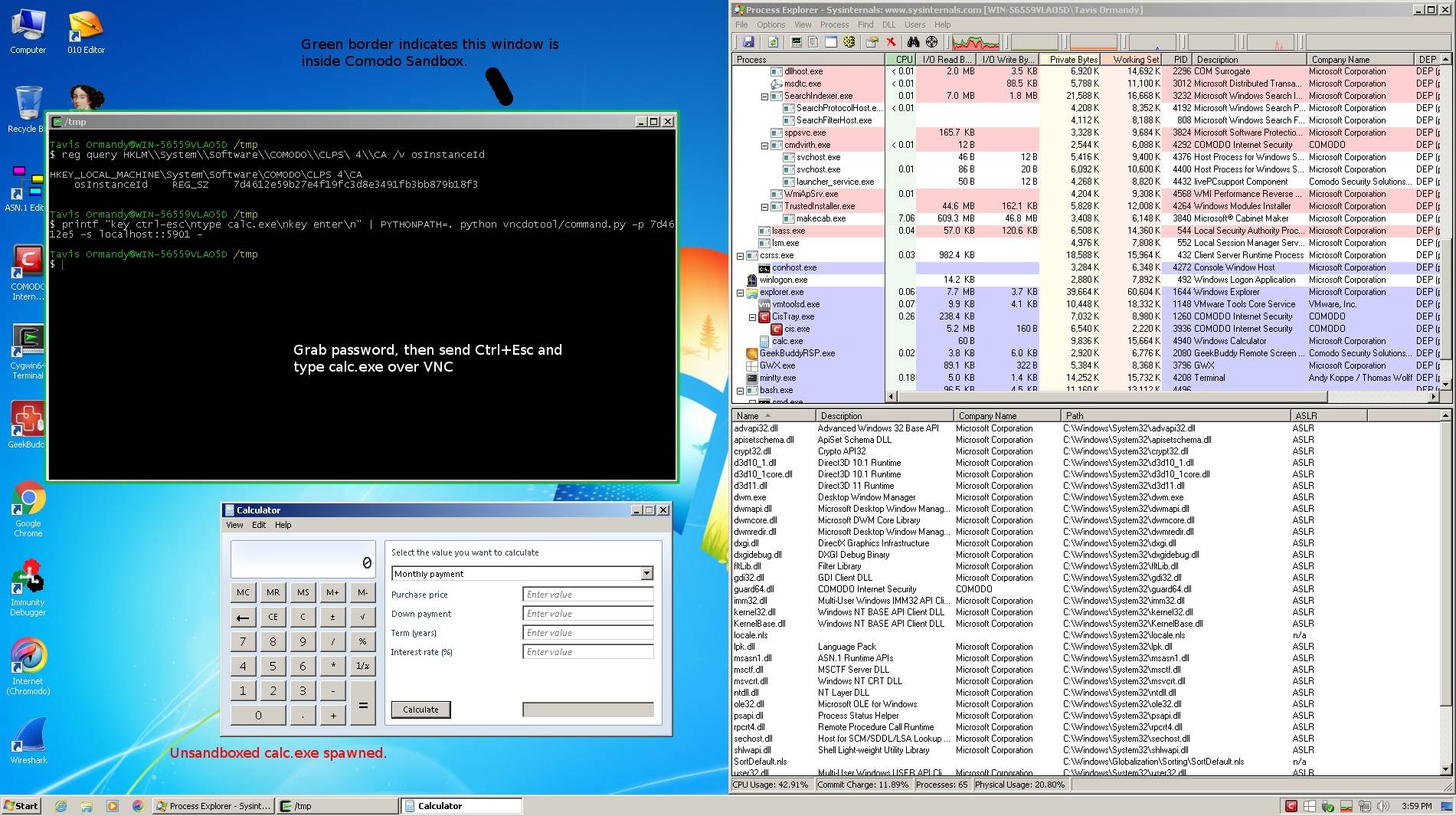
When installing Comodo Anti-Virus, Comodo Firewall, or Comodo Internet Security on a Windows PC, you'll get a program called GeekBuddy, which Comodo staff can use to carry out remote technical support on people's PCs (in exchange for money).
GeekBuddy allows this by installing a VNC server that has admin-level privileges, is enabled by default, and is open to the local network. At one point the server had no password protection at all – so anyone could connect and commandeer a system. That was fixed by enabling password protection, although Ormandy discovered the passwords were predictable.
If you're running Comodo's software, malware on your PC, miscreants on your network, or perhaps anyone on the internet, could have potentially gained control over your computer.
Any logged-in normal user, or software running on the system, could grab the VNC password from the Windows Registry, and gain higher privileges by connecting to the server. The password can be guessed by those connecting remotely as it's rather short, simple and predictable. Basically, PCs were backdoored by the security suite.
"This is an obvious and ridiculous local privilege escalation, which apparently Comodo believe they have resolved by generating a password instead of leaving it blank," reported Ormandy, an information security engineer at Google.
"That is not the case, as the password is simply the first 8 characters of SHA1(Disk.Caption+Disk.Signature+Disk.SerialNumber+Disk.TotalTracks). I imagine Comodo thought nobody would bother checking how they generated the password, because this clearly doesn't prevent the attack they claim it solved."
Ormandy reported the security design flaw to Comodo on January 19. Today, Thursday, the biz told the Google staffer that the vulnerability was addressed in version 4.25.380415.167 of GeekBuddy, which was released on February 10. We're told 90 per cent of users should have automatically installed the update by now. ®