This article is more than 1 year old
Rent a denial-of-service booter for $60, wreak $720k in damage
Or $7.2 million a day, by some measures
Criminals can pay distributed-denial-of-service attackers less than US$60 to inflict as much as US$720,000 in damage to an organisation per day, researcher Dennis Schwarz says.
The so-called booter or stresser services are commonly sold as would-be legitimate tools for security professionals. These tools are supposedly used to test the resilience of corporate networks by flooding them offline with junk network traffic.
But in reality many booters are used for illegal DDoS and use hacked and stolen router and machine resources to power the attacks.
Schwarz examined one booter service sold on a Russian crime forum by a user known as Forceful comparing the cost to rent per day with the average damage of DDoS and analysing an acquired malware binary.
"In this marketplace, it almost always starts with an advertisement for a DDoS booter service on one of the many public Russian language forums," Schwarz says.
"The reason people buy a booter service is people getting upset with other gamers, robbery, and anti-competition in businesses, ransom … and possibly diversion while carrying out other attacks."
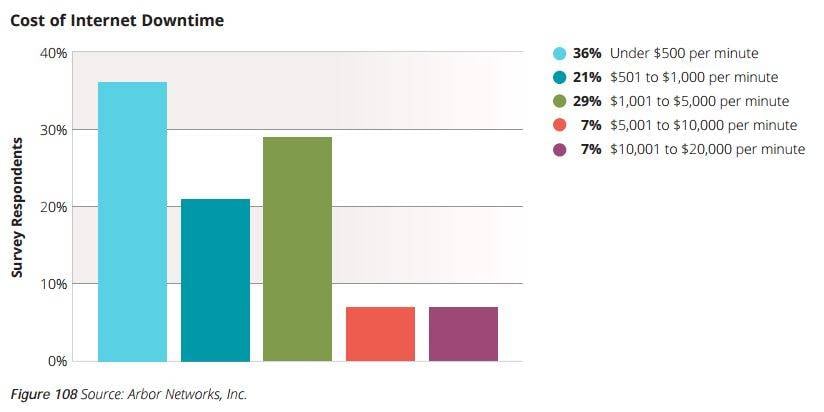
Abor says in its Worldwide Infrastructure Security Report [PDF] that the average cost is US$500 per minute largely due to downtime and reputational damage, and the price of remediation.
About a third of the 354 respondents to that research survey reports DDoS attacks cost up to $5,000 a minute.
Extrapolating that figure could mean a booter attack could cause US$7.2 million (£6.6 million, A$9.8 million) in damages a day, however it is likely those organisations would have robust DDoS defence and response mechanisms.
Schwarz says the imbalance between the rental price of attacks and the cost of damage to targets "highlights both the extreme asymmetry of the economics of DDoS attackers" and the need for DDoS defenses.
Forceful charges US$60 a day to rent their booter, or US$400 a week, with free five to 10 minute tests.
Arbor Network's BladeRunner monitored the attacks and found from July to October the booter bot was rented for 82 attacks equaling US$5,408. ®
The number of DDoS attacks are on the rise. In the dying months of last year attacks jumped 149 percent compared to the same period in 2014 according to Akamai.