This article is more than 1 year old
Hospital servers in crosshairs of new ransomware strain
SamSam virus is highly contagious and Bitcoin's the only known cure
Security types are warning hospitals to stay on alert for a "widespread campaign" targeting vulnerable servers with new strains of ransomware.
The SamSam ransomware variant targets vulnerable servers with criminals breaking into networks and infecting as many systems as they can access.
Cisco's Talos threat man Nick Biasini says SamSam's writers are popping servers in the healthcare sector, using stolen logins to infect individual systems.
"Cisco Talos is currently observing a widespread campaign leveraging the Samsam (Samas, MSIL.B/C) ransomware variant," Biasini says.
"This particular family seems to be distributed via compromising servers and using them as a foothold to move laterally through the network to compromise additional machines which are then held for ransom.
"A particular focus appears to have been placed on the healthcare industry."
Jboss application servers are being targeted using the JexBoss security testing tool, he says.
According to an Intel February report [PDF] attackers have also used the csvde.exe tool to harvest Active Directory credentials which helps with lateral movement for further ransomware infection.
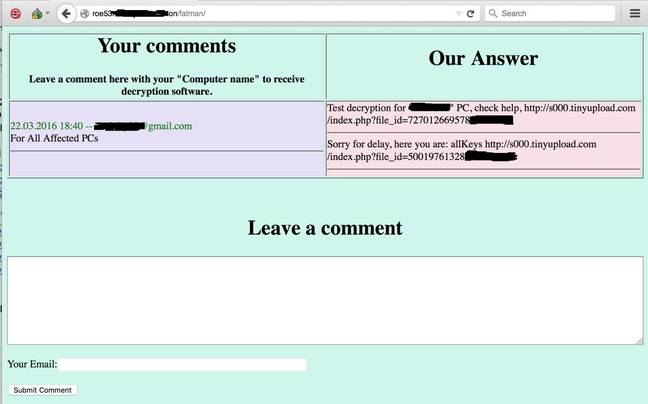
SamSam victims pay up.
SamSam and a separate strain Maktub are further unique in that file encryption takes place offline and does not use the usual command and control infrastructure for payment.
Maktub, however, spreads through typical phishing campaigns according to a MalwareBytes security wonk known as Hasherezade, who says the code will both encrypt and compress files in a likely attempt to speed up the infection process.
Maktub will not infect systems that have the Russian keyboard locale activated, in a likely bid to avoid drawing local law enforcement heat.
"Maktub Locker has clearly been developed by professionals," she says. "The full product’s complexity suggests that it is the work of a team of people with different areas of expertise."
SamSam by contrast appears to be the work of amateurs to the ransomware game, Check Point security bod Gil Sasson says.
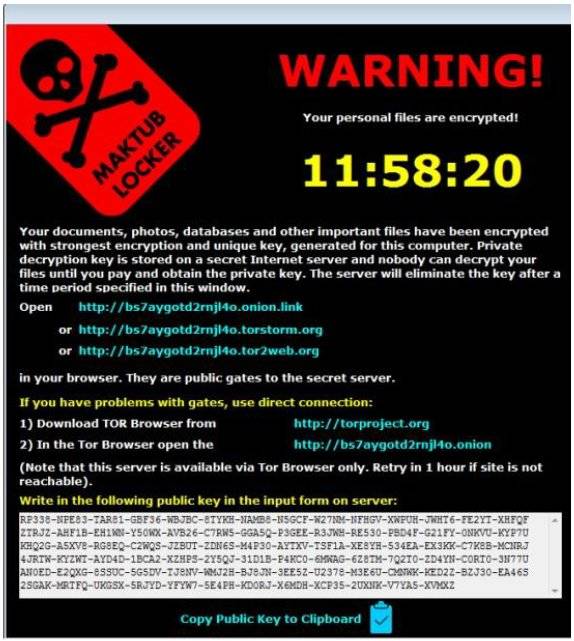
While Maktub victims are pointed to a payments site and offered two free file decryptions, SamSam casualties are asked to pay the one Bitcoin per machine ransom before noting the proof of payment in the comments section of their blogs.
Those who pay are promised a copy of decryption software along with a private key, according to the Intel report. Once files are decrypted, SamSam deletes itself.
VirusTotal checks against a related MD5 show it is detected by one antivirus platform as a generic malware tool.
Attackers have removed the latest Wordpress sites, eliminating the ability to review victim comments.
Intel reckons in its February report that "many" victims have paid the SamSam ransom. ®
