This article is more than 1 year old
Hacker reveals $40 attack that steals police drones from 2km away
No encryption in pro-grade drones: just sniff Wi-Fi and copy signals
Black Hat Asia IBM security guy Nils Rodday says thieves can hijack expensive professional drones used widely across the law enforcement, emergency, and private sectors thanks to absent encryption in on-board chips.
Rodday says the €25,000 (US$28,463, £19,816, AU$37,048) quadcopters can be hijacked with less than $40 of hardware, and some basic knowledge of radio communications.
With that in hand attackers can commandeer radio links to the drones from up to two kilometres away, and block operators from reconnecting to the craft.
The drone is often used by emergency services across Europe, but the exposure could be much worse; the targeted Xbee chip is common in drones everywhere and Rodday says it is likely many more aircraft are open to compromise.
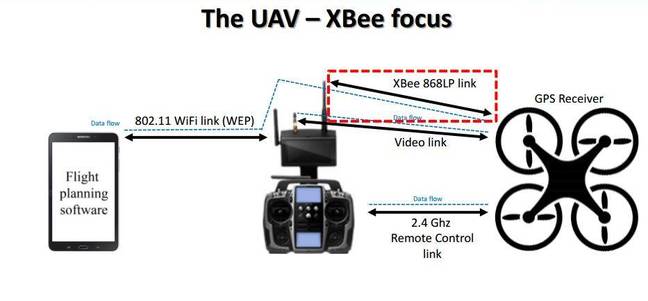
The Germany-based UAV boffin worked with the consent and assistance of the unnamed vendor to pry apart the internals of the drone and the Android application which controls it.
He found encryption, while supported, was not active in the Xbee chips due to performance limitations, and that the WiFi link used to control the aircraft at altitudes below 100 metres was protected by extremely vulnerable WEP.

The hijacked drone starts up.
Rodday told the BlackHat Asia conference in Singapore that attackers who copy commands from the Android app can fully control the drone, and demonstrated the feat with a start engines directive that fired up the aircraft's rotors.
"You can break the WiFi WEP encryption and disconnect their tablet and connect your own, but you have to be within 100 metres," Rodday told The Register.

Nils Rodday. Image Darren Pauli / The Register.
"On the Xbee link we can perform a man-in-the-middle attack and inject commands between the UAV and the telemetry box from up to two kilometres away.
"An attacker can re-route packets, block out [the operator], or let the packets go through, but I guess most attackers would [steal] it."
The drone flow.
The attacker's remote AT commands would be rejected if Xbee encryption was applied, mitigating the man-in-the-middle attack and the ability to snoop on traffic, Rodday says.
The manufacturer which supplied the drone is evaluating Rodday's suggestions about how best to shutter the attack vector, the easiest of which would be to encrypt communications within the firmware on the aircraft and the Android app.
Rodday thanked fellow researchers University of Twente's Professor Dr Aiko Pras and Dr Ricardo de O Schmidt, along with KPMG's Ruud Verbik, Matthieu Paques, Atul Kumar, and Annika Dahms. ®
