This article is more than 1 year old
Body of evidence: Biometrics and YOU
Feeling your way around non-password access systems
The proliferation of password protection has become an assault on the senses. The rise of biometric authentication is helping to create some balance, enabling verification with a simple interaction, which, for many, is the fingerprint reader on a mobile phone. And once you start using the fingerprint/phone combo for NFC payments, the convenience it offers soon becomes habitual.
So, no passwords, no pain – battery life notwithstanding, of course.
Biometric methods of user verification are, as the science implies, going to get the measure of one’s biology – something that’s unlikely to change, except by accident or deliberate design.
One of the higher profile facial recognition payment implementations has been the MasterCard Identity Check app, better known as “selfie pay”, piloted in Canada and the Netherlands for corporate card holders. Setting up requires you blink as you prepare to take a selfie. Fingerprint detection is also an option, but as not all phones have these readers and yet every phone these days has a camera, facial recognition to verify payments would seem set to mushroom.
MasterCard relies on Daon’s IdentityX for the biometric functionality – a multimodal identity verification platform that offers mobile devices what the company describes as the “triumvirate of Face, Voice and Touch ID options”.
The MasterCard Identity Check app has other layers of security including encryption and geolocation from the device. Yet for the user, all they’re likely to notice is the swift, password-free effectiveness of selfie pay. A biometric application that makes the trade, not only from your credit card but of your personal appearance in exchange for convenience.
Biometrics gets domestic
At Apple's recent WWDC, senior vice president of software engineering Craig Federighi revealed a new feature in iOS 10 Photos called Advanced Computer Vision that uses deep learning techniques to go beyond face tagging to enable object and scene recognition, performing “11bn computations per photo”. It’s a trick that Netatmo announced with its Presence camera at CES, to identify people, animals and models of cars. It’s a spin-off from its Welcome home security product that also relies on deep learning.

MasterCard uses Daon’s IdentityX – a “triumvirate of Face, Voice and Touch ID options” but you must blink
While iOS 10 will sort out your photos in clusters, Netatmo’s application of computer vision has a biometric twist, as the Welcome camera features a built-in realtime facial recognition algorithm. The company’s founder and chief executive Fred Potter explained for us the task of getting a satisfying facial at home without relying on a massive online image database to deliver the money shot.
“A computer vision algorithm is not a static work," Potter said. "It’s not something you can purchase and then it becomes an asset. It’s a dynamic work because you will use the results of the data of the algorithm that is running on the camera to enhance and fix your algorithm. Currently, we only have 97 per cent of good recognition; we still have three per cent of error. When the user says it’s the wrong recognition, this will help the algorithm to be more efficient. It’s always ongoing work.”
While the likes of Facebook, Picasa and iCloud own servers stuffed full of labelled photos, Netatmo’s approach functions on a local level with its artificial intelligence algorithm having gone through intensive training.
“The technique we are using is called RCNN, recursive convolutional neural networks. We show two pictures and we train the machine to say whether these two pictures are the same person or a different person. To do that you need to train the machine with a very large set of pictures that you know are the same person or are different,” Potter said.
A biometric home system of this kind does at least bypass all the red tape regarding compliance, as all you’re doing here is monitoring rather than interacting with a secure verification service. Typically, Netatmo’s Welcome captures video and sends alerts of unknown faces are sent to your phone or desktop. If you want to know how it works in the home, the El Reg review is featured here.
Organ-grinder
While numerous biometric authentication modalities such as iris, face, fingerprint and vein pattern recognition can simplify payments and border crossings, the user has to engage with the process to enable verification. However, there are other biometric approaches that work in the background to remove authentication barriers.
Heartbeat recognition is touted as one such option that effectively provides continuous authentication so long as the user is wearing something like a wristband. With the Nymi Band, the monitoring is simply an ECG (electro cardiogram) tracking the unique pulsating signature of the individual’s heart. Although it does suggest background authentication, the wristband still needs charging up and, of course, you have to remember to put it on.

Nymi’s Band relies on your heartbeat's disctinctive pattern for verification
This particular modality has also raised a few interesting questions: Could a heart-transplant recipient pass as another person? Would someone in the throes of a heart attack be unable to unlock their mobile phone to call for help? Or could the stimulating effects of say, Bolivian marching powder impact on verification acceptance, with the algorithm assuming transactions were being made under stress?
Paying lip service
Voice biometrics can be either active, requiring a pass phrase, or passive, where the technology can analyse your voice as you speak to an agent. The latter approach is called Text Independent Voice Biometrics and all have to do is talk. It’s this element of background verification that’s becoming increasingly important to banks and vendors - emerging as an attractive improvement in user experience.
Nuance, the company behind the Dragon NaturallySpeaking and Apple’s Siri speech recognition software, also offers voice biometrics and has now clocked up 75 million users and over three billion verifications. Here, the task isn’t to recognise words and transform them into text but to authenticate the speaker from their unique voiceprint.
One customer, Barclays Wealth, uses Nuance voiceprint recognition to forward a customer to an agent. Account queries are then dealt with personally, eliminating not just frustrating obstacles for the customer but, likewise, removing the grind of client interrogation – the worst part of an agent’s job.
There are other benefits too, as Brett Beranek, Nuance senior principal solutions marketing manager for enterprise told us: “Voice biometrics also changes the dynamic of fraud prevention to actual prosecution. A lot of fraud teams spend their time deflecting fraud. They deflect fraud from one channel and the fraud leaks to another.
“With voice biometrics you actually have evidence that you can submit to law enforcement and basically prove in a court of law that it is a very specific individual that perpetrated that fraud or that attempted to perpetrate fraud. It’s not only more secure but allows organisations to do something about the fraud.”
Of course, getting blighted by a sinus-stuffing cold or bout of laryngitis could cause the system to reject the speaker but Beranek reckons if your mother can recognise your voice, then the voice biometrics will too. “We have an algorithm to detect a recording. It’s not foolproof, it doesn’t work one hundred per cent of the time but it works in the high nineties. And so we can prevent most, not all, but most of these social engineering attacks,” he said.
“Our first level of defence is low grade recordings and playback. I record my voice on a mobile, I play it back through a speaker – those are easy to detect because there are huge bands of low frequency audio that are not present to what a human voice would have.”
What he describes as high-definition recording is a different matter though and the focus is on audio signatures that reveal the way the sound has been reproduced.
“It’s not like you look at the audio wave and go: ‘Aha, there’s the difference between a real human voice and playback’. These audio characteristics are really minute. We just took a whole bunch of recordings and a whole bunch of live voices that are being inputted into the system and compared the two. And we had the deep neural network find what the differences are.”
Learning to behave
BehavioSec specialises in Behavioural Biometrics and has 50 million users with another five to 10 million in proof-of-concept trials. The company developed its authentication system for PC users but more recently produced behavioral biometric identification profiling for mobile.
It works by looking at the rhythm and the timings of key commands and how they are entered. All of this checking happens in the background with the user’s behavior learned quickly to create a profile. Numerous metrics are monitored, the most basic being flight (the time taken in between key presses) and press, the time spent on the key itself. How you use the mouse is observed too, such as the speed and arc of travel. Likewise, on a mobile phone’s screen, the pressure and where you press on buttons is monitored, as well as accelerometer and gyroscope metrics.
Johan Dalnert, BehavioSec's chief marketing officer, told us: “It’s all weighted, so they’re not of equal importance. Over time our algorithm will adapt to your behaviour. If your first 99 transfers were sitting down and your hundredth was on the bus, you will probably not get a very good behaviour score because you’re on something that is shaking but the bank wouldn’t necessarily stop that. It’s just an indicator for the bank to look for other anomalies, for other things that look suspicious. So we’re helping the bank focus on where to look and we’re giving them a lot more decision intelligence without disturbing the end user.”
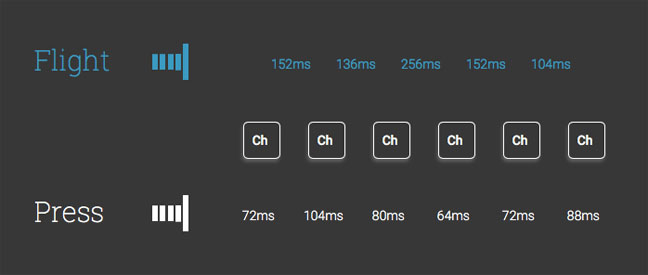
Typing "El Reg" in BehavioSec reveals the timing differences in key press and flight
This decision intelligence lets the bank choose whether to proceed as normal or introduce an additional verification step, all without the user being immediately shut out of the system. By using this near-realtime tool in risk assessment, the bank is free to make up its own rules. It could perhaps decide to rely solely on positive behavioural biometric scores to allow transfers of up to £500 in an effort to deliver a better user experience. It might also choose to lower that threshold in the wee small hours when the user’s biometric scores are looking a little tried and emotional.
You can even try this for yourself. BehavioSec has its own Keystroke Timing Tool. It’s a Javascript simulation but it gives an immediate insight on how the company monitors behavioural biometrics and harvests profile data.
With biometrics from voice, behaviour and even heart monitoring set to put verification into the background, it looks likely that we’ll regard fingerprint or facial recognition to be as irritating as two-factor password authentication is now. Perhaps inevitably, systems that know us, inside and out, will become the norm and “anonymity” will be just a word in the dictionary. ®
