This article is more than 1 year old
World's lamest ransomware authors won't answer fake tech support line
Pro-tip: Spend less on SEO and more on scrubbing the universal decrypt key from your code
Symantec malware manglers Sam Kim and "Val S" have spent 90 minutes on the phone to ransomware purveyors while researching a new variant that encrypts PCs through fake Windows 10 activation dialogues.
Kim and "S" ran out of patience and money waiting for the net menaces to answer their call placed to a phone number listed on the ransomware's splash screen.
The duo never had their call answered by the promised "Store Representative", who according to the hold audio track were "busy assisting other callers". An apology with an accompanying call-back offer triggered after 30 minutes.
With patience exhausted and funds dwindling, the pair were left to address the malicious hard drive encryption scam using reverse engineering.
It did not take long, as "... the malware author left the unlock code in plain sight without using any obfuscation techniques," the researchers say.
"The malware itself is simplistic and does not contain any connections to a command and control server."
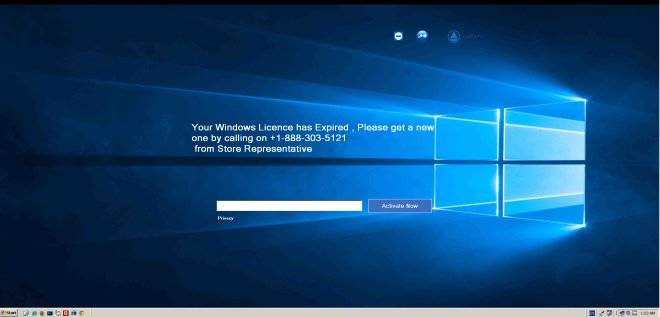
For a bad time, call +1-888-303-5121. Image: Symantec.
The phone number for the world's lamest ransomware was disconnected when The Register called, hoping to speak to the VXers, with the line now entirely out of commission.
It is a remarkable failure given the malware writers went as far as to pollute search engine results for the listed phone number by purchasing multiple domains and creating seemingly legitimate sites for PC help and malware removal, the pair note.
The Register, in a bid to reach the VXers, placed a call to a mobile linked to one business which shared the same phone number as the ransomware operators, but the call went to voice mail.
It is possible the number was ported or otherwise hijacked from innocent businesses for a short period during the infection campaign.
Symantec's researchers say "… it appears the attackers have carefully thought out how to maximize revenue generation by using a combination of branded ransomware alongside manipulated search results," the researchers say.
Victims can enter the code 8716098676542789 to unlock their files. ®
