This article is more than 1 year old
Li-Fi with my little eye … a vulnerability
Fooling around with VLC systems
Proponents of visible light communications (VLC) like “Li-Fi” love reminding us of the bonkers speeds they can get (200 Gbps last year, for example), but just like its radio-spectrum counterpart, it needs protection against eavesdropping and jamming.
In this paper at Arxiv, Warsaw University of Technology researcher Grzegorz Blinowski demonstrates that “it is quite easy to disrupt, and in some cases to even hijack legitimate transmission” in VLC networks.
Grzegorz says there's a widespread assumption that VLC is more secure than Wi-Fi, since a transmitter is emitting visible light, and because light is directional and doesn't travel through walls (although it does bounce around inside a room).
That assumption has led developers to pay too little attention to security, he reckons, noting that “we must better understand the physical layer mechanisms of executing a hostile-transmitter type attack”.
By arranging “legitimate” and “rogue” VLC transmitters carefully, Grzegorz claims he was able to jam between 11 per cent and 18 per cent of a room's area from receiving legitimate transmissions.
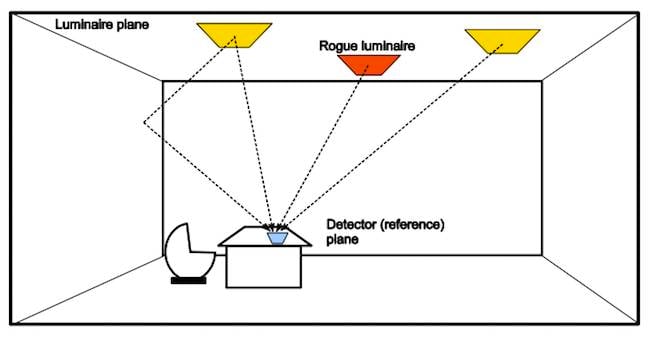
Grzegorz's pwnage model is simple: take over a light bulb in a VLC network
By replacing three downlights in a VLC installation with their own devices, he claims to have jammed around 42 per cent of the room – and was able to replace the legitimate transmission with the “attack” traffic in about 10 per cent of the room.
And yes: this particular attack depends on enough physical access to replace “legitimate” devices with “rogue” devices – but how many sysadmins have found rogue Wi-Fi access points in the businesses they work for? It's also worth considering that if someone is waltzing around a compromised network, it might not be so hard to take control of individual VLC devices within that environment. ®
