This article is more than 1 year old
CERT tells Microsoft to keep EMET alive because it's better than Win 10's own security
Vuln seeker says EMET has 13 protections Win 10 doesn't
Microsoft should reverse its planned axing of the lauded Enhanced Mitigation Toolkit (EMET) as Windows 10 cannot yet match its level of security, according to Carnegie Mellon University CERT furniture Will Dormann.
The vulnerability analyst, who has pushed out security alerts and advice from the world's first CERT for around a decade, says even a Windows 7 machine running EMET trumps Windows 10's native defences.
Redmond plans to rid the world of the exploit mitigation toolkit in mid 2018, after recently extending its end of life date by 18 months.
Microsoft's reasoning is that Windows 10 has baked in many of EMET's defences and therefore is more secure than earlier versions of WIndows.
Microsoft OS security program lead Jeffrey Sutherland explained earlier this month why EMET should and will be retired, focusing on its supposed limitations as a bolt-on compared to native security controls.
Sutherland argued EMET therefore will be less adaptable than baked-in defences, leaving users vulnerable to future threats.
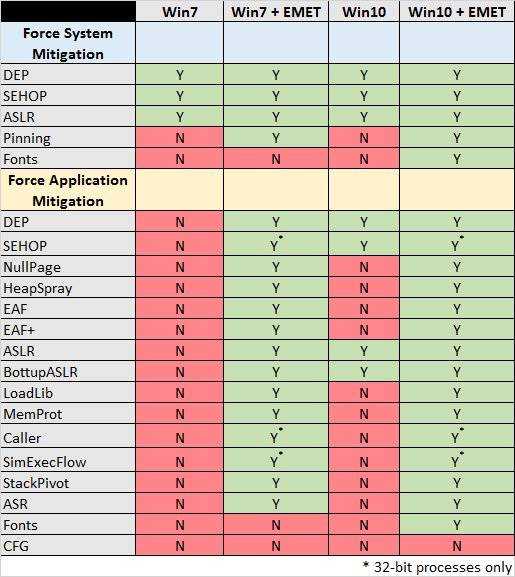
Dormann says Sutherland's assertions overlook the "primary reason" for running EMET, namely forcing extra defences to applications that do not opt into native exploit mitigation.
"It is pretty clear that an application running on a stock Windows 10 system does not have the same protections as one running on a Windows 10 system with EMET properly configured," Dormann says.
"Even a Windows 7 system with EMET configured protects your application more than a stock Windows 10 system."
The bug hunter says EMET running on Windows 10 brings 13 more mitigation protections than offered by the operating system alone.
Of those the application-specific-protection capability it provides is key since software developers often do not write code that takes advantage of the opt-in exploit mitigations available in Windows 10.
"EMET puts this control back in our hands," he says.
The July 31 2018 EMET execution day will be a critical one for those running applications also set to reach end of life like Microsoft Office 2007. Zero day vulnerabilities found in these applications will be consigned as forever days thanks to the cessation of patching.
"With such out-of-support applications, it is even more important to provide additional exploit protection with a product like EMET," Dormann says.
Windows 10 is a mostly harmless positive security upgrade on preceeding Windows platforms according to Google's Project Zero hacker house, and Dormann agrees saying it provides "nice" exploit mitigations.
But much of the benefits exposed in technologies like the ROP-like Control Flow Guard mitigation is lost when applications are not specifically compiled to utilise the security controls.
"Out of all of the applications you run in your enterprise, do you know which ones are built with Control Flow Guard support? If an application is not built to use Control Flow Guard, it doesn't matter if your underlying operating system supports it or not," Dormann says. ®