This article is more than 1 year old
Poison .JPG spreading ransomware through Facebook Messenger
Cick-to-self-p0wn attack sneaks Locky ransomware past Zuck's security model
Checkpoint has found an image obfuscation trick it thinks may be behind a recent massive phishing campaign on Facebook that's distributing the dangerous Locky ransomware.
The security firm has not released technical details as the flaw it relies on still impacts Facebook and LinkedIn, among other unnamed web properties.
The flaw as described is, in this writer's opinion, ultimately of little risk to El Reg's tech savvy readers, but folks who can be conned into downloading and running unknown executables are at risk.
The attack is also significant in that it breaks Facebook's security controls.
In a proof-of-concept video by Checkpoint researchers Roman Ziakin and Dikla Barda, an attacker is shown exploiting the flaw by sending an HTA HTML app through Facebook Messenger disguised as a .JPG. (JavaScript-loaded SVG images can also be used.) The victim must click on the attachment, an act that generates a Windows save file prompt asking the victim for the save directory to which the now .HTA file will be downloaded.
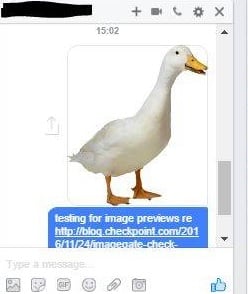
Images sent over Messenger appear
as previews, not attachments
They must then double-click the saved .HTA file to unleash the Locky ransomware.
While the attack is not automated and, it does break Facebook's hypervigilant security model and is fairly regarded by Checkpoint as a Facebook "misconfiguration".
Facebook will undoubtedly fix the flaw; The Social Network™ already warns users who open a browser javascript console to protect against malicious code.
Checkpoint's chaps says the attack is useful because Facebook is a trusted asset.
“As more people spend time on social networking sites, hackers have turned their focus to find a way into these platforms,” Ziakin and Barda write.
“Cyber criminals understand these sites are usually white listed, and for this reason, they are continually searching for new techniques to use social media as hosts for their malicious activities."
Those users who do open the hta file will unleash one of the worst ransomware variants in mass circulation, encrypting their local files in a way that leaves backup restoration or ransom payment as the only options available to them.
There is no decryption method for Locky, and most victims will find their backup files also deleted.
Locky is under active development. Its authors have recently switched to the .zzzzz encrypted file extension with a new downloader that has lower antivirus detection rates. ®