This article is more than 1 year old
Masterful malvertisers pwn Channel 9, Sky, MSN in stealth attacks
Same group compromised a million users A DAY.
A two-year long, highly sophisticated malvertising campaign infected visitors to some of the most popular news sites in the UK, Australia, and Canada including Channel 9, Sky News, and MSN.
Readers of those news sites, just a portion of all affected (since it also affected eBay's UK portal), were infected with modular trojans capable of harvesting account and email credentials, stealing keystrokes, capturing web cam footage, and opening backdoors.
The news sites are not at direct fault as they displayed the advertising; the ad networks and the underlying structure of high-pace and low-profit margins is what lets malvertising get its huge impact.
Users from the United States were ignored, for reasons unknown.
The quiet success of the still-ongoing attacks comes despite that researchers from security firm ESET found earlier variants in late 2014 targeting Dutch users.
Well-known researcher Kafeine, now with Proofpoint, reported on a subsequent massive malvertising campaign in July in which the AdGholas malvertising campaign had ensnared as many as a million users a day.

The malware stenography revealed. Image: ESET.
Those attacks slung banking trojans at British, Australian, and Canadian users with localised ruses.
AdGholas exploited among others a low-level Internet Explorer vulnerability (CVE-2016-3351) to assist with cloaking that Microsoft was slow to patch.
Victims who surfed various news outlets using Microsoft Internet Explorer and Adobe Flash which did not have recent patches applied could be silently compromised.
Users of Yahoo!'s email service were also served the trojanised ads through the tech giant's advertising network.
Those on other browsers were ignored, as were those running packet capture, sandboxing, and virtualisation software, the latter platforms being hallmarks of white hat security researchers.
The criminals were able to maintain stealth despite the many skilled eyes of the whitehat research community by weaving malicious code into advertising banners.
They even went as far as to create legitimate software, including a still-live Google Chrome extension, which appear non-malicious and are functional.
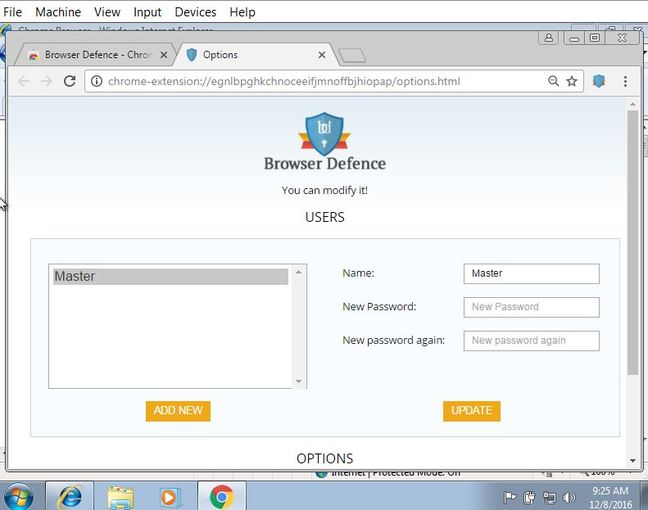
The Browser Defence Chrome app seems legit. Image: The Register.
While regular malvertising manages to get booby-trapped banner ads accepted by the likes of Google, Yahoo!, and scores of smaller networks, the AdGholas campaign served its trojans through the manipulation of individual ad pixels.
Malwarebytes analyst Jerome Segura along with ESET researchers revealed the intricacies of the latest campaign today.
They say criminals remained cloaked for so long by altering the alpha channel within pixels of the advertising banners they submitted to ad networks.
This passed the weak security checks to be displayed on major news sites, forcing the trojan to install on any machine which merely viewed the banner with vulnerable Internet Explorer and Flash installations.
Poisoned pixel ads included those for Browser Defence and BroXu, two legitimate working creations of the malware writers.
The malcode within the ads exploited Internet Explorer bug CVE-2016-0162 for initial reconnaissance and Flash bugs CVE-2016-4117, CVE-2016-1019, and CVE-2015-8651 to get payloads onto machines.
"Despite not targeting the US, the latest AdGholas campaign has once again reached epic proportions and unsuspecting users visiting top trusted portals like Yahoo or MSN [among] many top level publishers were exposed to malvertising and malware if they were not protected," Segura says.
"There is no doubt that the adversary is very advanced and has been clever to fly under the radar for long periods of time."
"At the time of posting the campaign still continues, although the major ad networks have been informed and should no longer be involved."
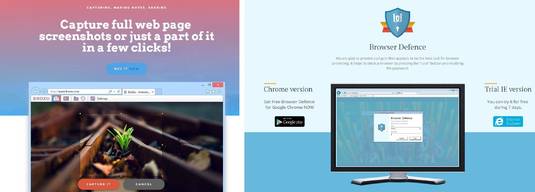
The BroXu and Browser Defence sites. Image: The Register.
Segura found the first attack based on the Browser Defence scam on 5 September through the SmartyAds network, before noticing it move to Yahoo! a month later.
It took until 27 November for Segura to "finally" reproduce the malvertising chain using a real residential IP address and a normal user machine free of monitoring tools.
"Up until then, we only had very strong suspicions that something was going on, but without a network capture, we simply did not possess the smoking gun required to make an affirmative claim," he says.
Segura informed Yahoo! once he confirmed the malvertising attacks.
Researchers at ESET reveal much the same and reveal the technical complexity of the stenography effort in which the malcode was hidden almost perfectly within advertising images. ®

