This article is more than 1 year old
Chrome dev explains how modern browsers make secure UI just about impossible
The 'LINE OF DEATH' between safe content and untrustworthy stuff is receding every year
Google Chrome engineer Eric Lawrence has described the battle of browser barons against the 'line of death', an ever-diminishing demarcation between trusted content and the no-man's land where phishers dangle their poison.
The line, Lawrence (@ericlaw) says, is a conceptual barrier between content that browser developers control, such as areas around the address bar, and untrusted content like browser windows where attackers can serve malicious material.
"If a user trusts pixels above the line of death, the thinking goes, they’ll be safe, but if they can be convinced to trust the pixels below the line, they’re gonna die," Lawrence says.
But the line is receding because untrusted content now appears above the line in tabs where attackers can enter their chosen web page title and icon.
Chevrons that open small windows can display extended information on usage of HTTPS, requests for location information, and so on extend below the line and send trusted data into untrusted territory.
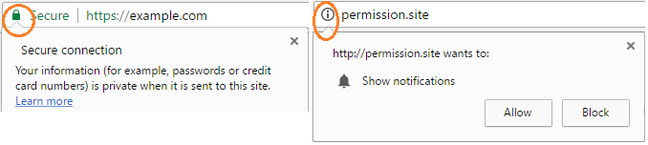
Chevrons with trusted data breach the line. Image: Lawrence.
Those subtle intrusions across the line open avenues for phishers; chevron popups can be faked and 'block' and 'allow' buttons turned into malicious clickable links, for example.
In 2005, a remote code execution flaw affecting Firefox was dug up which abused favicons, the untrusted icons websites set that appear in tabs and bookmarks.
The line of death deteriorated in 2012 when Microsoft moved Windows 8 Internet Explorer to its full screen minimalistic immersive mode. Lawrence, then program lead for Internet Explorer with Microsoft, opposed the move and says it made the line of death indistinguishable from content, .
"... because it (Internet Explorer) was designed with a philosophy of 'content over chrome', there were no reliable trustworthy pixels," he says. "I begged for a persistent trust badge to adorn the bottom-right of the screen - showing a security origin and a lock - but was overruled."
He says one Microsoft security wonk built a "visually-perfect" Paypal phishing site that duped the browser and threw fake indicators. "It was terrifying stuff, mitigated only by the hope that no one would use the new mode."
The breaching of the line of death is a boon to picture-in-picture phishing attacks, in which attackers create what appear to be fully functional browsers within a browser. Immaculate reproductions of browsers including the trusted sections above the line of death have been created that fool even eagle-eyed researchers.
Microsoft's own security researchers in 2007 would find picture-in-picture attacks to be virtually perfect. The team of four wrote, in a paper titled An Evaluation of Extended Validation and Picture-in-Picture Phishing Attacks wrote in the paper [PDF] that the attack vector was so compelling it beat all other phishing techniques including homograph tricks in which letters of legitimate URLs are replaced with visually similar equivalents from, for example, the Cyrillic alphabet.
Everything is untrusted: The line of death dies in HTML5. Image: Lawrence.
Picture-in-picture attacks also rendered ineffective the then-new extended validation SSL certificate scheme for determining malicious sites. Extended validation, now mainstream, displays a green address bar padlock for participating and verified sites. The inconvenient research spooked one large certificate vendor then in talks with Redmond over buddying up for the then new certificates.
The line of death receded further with the advent of HTML 5, which brought with it the ability for websites, and phishers, to push browsers into fullscreen mode which wiped any line between trusted and untrusted content.
And the line is all-but-absent on mobile devices, where simplicity and minimalism is king. "We are seeing a lot more hits on phishing links in mobile because it is so much harder to extract necessary information," Sophos senior technology consultant Sean Richmond tells El Reg . "Expanding the URLs is more difficult and it is harder to get the information users need to make decisions, so security awareness can suffer."
Email apps are similarly breaching the line of death. Outlook's modern versions place a trusted message of "this message is from a trusted sender" within the untrusted email contents window, allowing phishers to replicate the notice.
"Security UI is hard," Lawrence says. ®
