This article is more than 1 year old
Sophos waters down 'NHS is totally protected' by us boast
Watered down homeopathy for computers is more powerful, m'kay?
Updated Sophos updated its website over the weekend to water down claims that it was protecting the NHS from cyber-attacks following last week's catastrophic WannaCrypt outbreak.
Proud website boasts that the "NHS is totally protected with Sophos" became "Sophos understands the security needs of the NHS" after the weekend scrub-up.
Security-watchers, including former staffer Graham Cluley, noticed the reverse ferret.
Sophos didn't publish a definition update until 1825 BST, hours after an outbreak that forced hospitals to postpone scheduled treatments and appointments in scores of NHS Trusts. Sophos Live Protection functionality, if enabled, could detect WannaCrypt earlier than that.
Signature updates aren't the only layer of security in modern anti-malware but this only raises further questions about why Sophos's technology didn't pick up an attack based on a known exploit patched by Microsoft two months prior.
Sophos has been talking a lot about building better anti-ransomware defences over recent weeks, most particularly following the Invincea purchase back in February. Last month the company launched anti-ransomware CryptoGuard technology, a paid add-on to its Sophos Server Protection products.
El Reg asked Sophos to comment on what seemingly went wrong with its security defences but we're yet to hear back beyond an acknowledgement of our query.
Sophos's social media staff were tweeting about how its tech could protect against ransomware attacks on Thursday, a day before disaster struck.
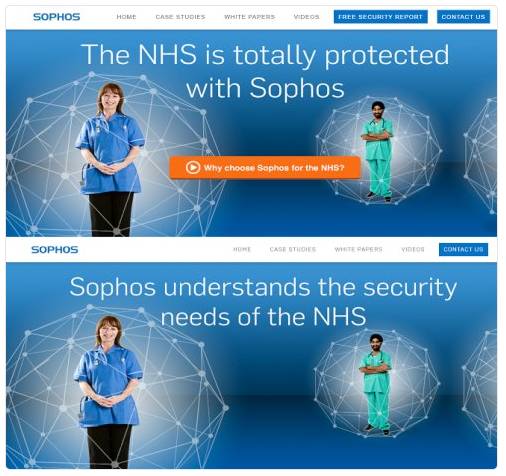
Sophos and the NHS, before and after WannaCrypt [source: Twitter]
It's all a bit awkward.
Sophos executives can, however, console themselves that the security firm's share price has risen markedly since the outbreak, rising 7.5 per cent in pre-lunchtime trading on Monday alone to reach 366.80 at the time of writing. ®
Updated at 15.05 UTC to add
Sophos has contacted us to say that customers using Sophos Intercept X or Exploit Prevention (EXP) "were protected proactively against the ransomware behaviour from the very first instance".
It added: "Sophos Endpoint Protection already detected some variants of the WannaCry ransomware. We added further detection at 15.58 UTC on Friday 12th May for samples in the new attack that we missed. This was a complex set of executables and exploits which took some time to analyse. We also thoroughly test all identity and rule updates before releasing them to our customers. The 17.25 UTC time in the KBA on our website is the time by which all our customers should have been updated. We are in the process of updating this wording in the KBA to be clearer.
"Sophos has added subsequent identities and generic detection rules to Sophos Endpoint Protection since then to block potential future variants of the malware and its techniques. We have also proactively contacted all our customers to advise them to deploy the Microsoft patch that mitigates the underlying vulnerability in the Microsoft OS."
Now read our analysis of the WannaCrypt epidemic.
