This article is more than 1 year old
Cryptocurrency miner found armed with same exploits as WannaCrypt
Adylkuzz predates ransomware by at least a week – and pays better too
The now infamous Windows vulnerability (MS17-010) exploited by the WannaCrypt ransomware has also been abused to spread another type of malware, specifically a cryptocurrency miner.
The Adylkuzz campaign predates WannaCry by severals day and may even have limited the spread of last week’s WannaCry infection, according to security firm Proofpoint.
"Initial statistics suggest that this attack may be larger in scale than WannaCry[pt], because this attack shuts down SMB networking to prevent further infections with other malware (including the WannaCry[pt] worm) via that same vulnerability," according to Proofpoint.
Targeted machines are used to mine for the Monero cryptocurrency. Monero is an alternative to Bitcoin recently adopted by the AlphaBay darknet market to trade in drugs, stolen credit cards, and counterfeit goods.
"Once infected through use of the EternalBlue exploit, the cryptocurrency miner Adylkuzz is installed and used to generate cybercash for the attackers," said Robert Holmes, vice president of products at Proofpoint.
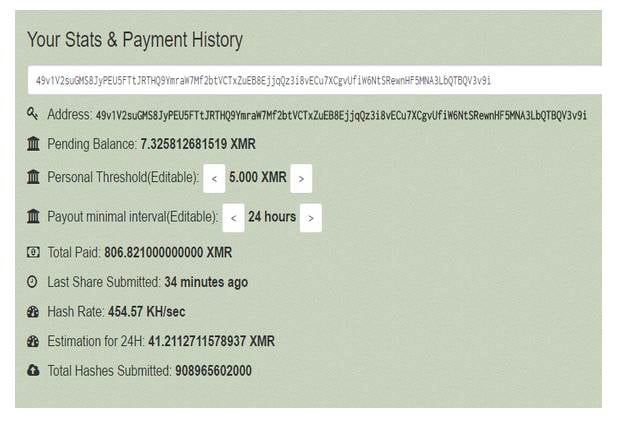
Monero address associated with Adylkuzz mining [source: Proofpoint blog post]
Adylkuzz began its campaign on or before 2 May, more than a week before WannaCrypt exploded on to the scene. One of several Monero addresses associated with income from Adylkuzz mining generated $22K, another $7K and a third $14K before mining ceased. Indications are that the crooks behind Adylkuzz have generated a lot more money than the WannaCrypt ransomware fiends.
"While an individual laptop may generate only a few dollars per week, collectively the network of compromised computers appears to be generating five-figure payouts daily. Unlike ransomware, no demands for money are made of victims. The malware is deliberately stealthy; users will only notice their Windows machine is running slowly and that they don't have access to shared Windows resources."
Tens of thousands of computers worldwide have been affected by the Adylkuzz campaign, Proofpoint warns. Despite WannaCrypt-inspired clean-up and patching efforts, the security firm reckons the Adylkuzz attack is still growing.
"For organizations running legacy versions of Windows or who have not implemented the patches that Microsoft released in March and last weekend, PCs and servers will remain vulnerable to this type of attack," Holmes added. ®
