This article is more than 1 year old
It's 2017, and UPnP is helping black-hats run banking malware
Pinkslipbot malware copies Conficker for C&C channel
Another banking malware variant has been spotted in the wild, and it's using UPnP to pop home routers to expose unsuspecting home users, recruited as part of the botnet.
McAfee Labs says the new campaign uses a variant of the ancient “Pinkslipbot”, and says it uses Universal Plug'n'Play (UPnP) to open ports through home routers, “allowing incoming connections from anyone on the Internet to communicate with the infected machine”.
As with any credential-harvesting botnet, the malware needs to get its booty back to the botmasters without exposing them, and this is where the UPnP exploit comes in.
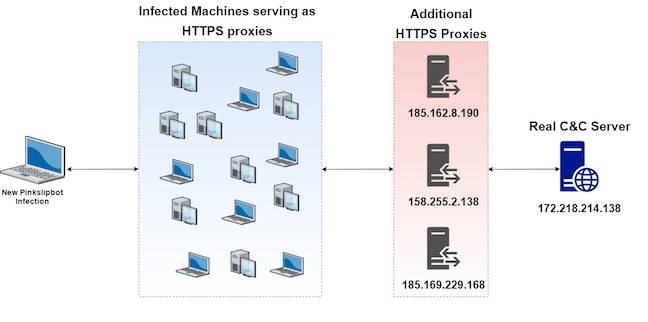
In the current Pinkslipbot campaign, UPnP merely provides the path to the targets: infect machines that provide HTTPS servers from IP addresses listed in the malware (McAfee's Sanchit Karve writes that it's the first time the company's seen HTTPS-based C&C servers).
Those machines act as a first of two layers of proxies deployed to protect the IPs of the C&C servers (see image below).
The malware scum behind the campaign are nothing if not thorough: pre-infection, they check the target's connection using a Comcast Internet speed tester (only US IP addresses are accepted). If the target passes the speed test, the malware then taps on UPnP ports to check the available services, and on vulnerable systems, checks 27 ports to see if it can map them to the outside world.
With one or more ports available, the attackers infect a machine behind the firewall, create a permanent port mapping for its traffic, and run it up as a C&C proxy.
The zombie C&Cs use the libcurl library to pass information to the second-layer proxies which handle communications with the “real” C&C servers.
McAfee suggests home users should “keep tabs on their local port-forwarding rules” [As if! - Ed], and should turn UPnP off if they don't need it (much more sensible).
While it might be true that this is only the second time malware scum have taken advantage of UPnP (the first was by Conficker in days of yore), enough bugs have been disclosed in the protocol to make it a security nightmare. ®
